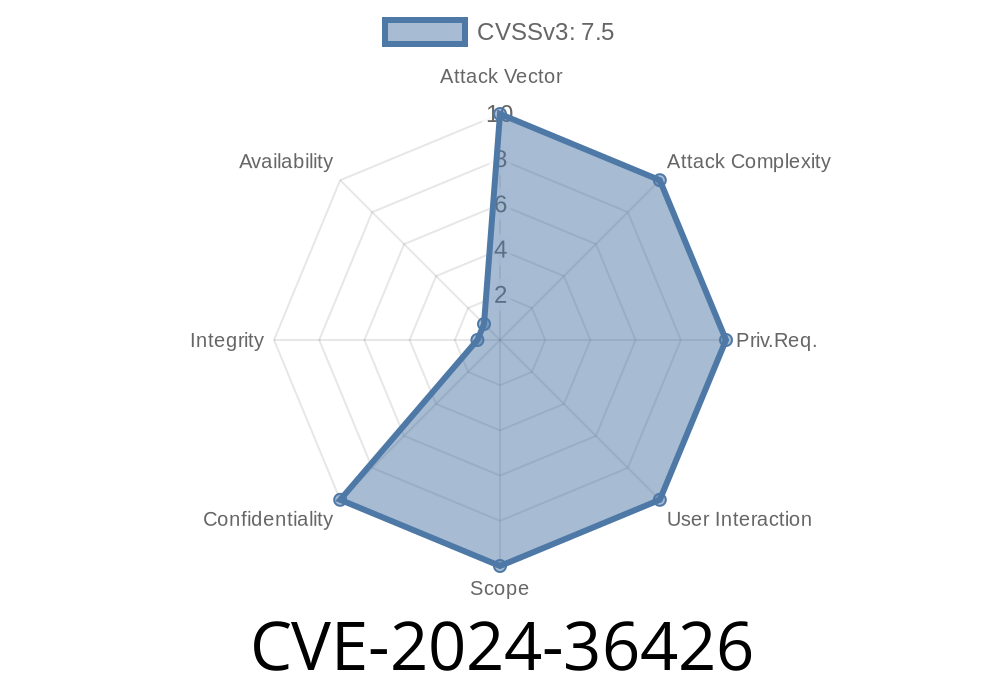
Recently, a vulnerability was identified in TARGIT Decision Suite, a popular business intelligence suite. This vulnerability, tracked as CVE-2024-36426, affects versions up to 23.2.15007. (before Autumn 2023). The flaw is fundamental: the application's session token is included in the URL and sometimes transmitted in plain HTTP, putting user sessions at serious risk. This post will break down what the vulnerability is, why it’s dangerous, show example code, share references, and explain real-world exploit scenarios.
Issue: Session tokens included in URLs and sent via unencrypted HTTP
- CVE: CVE-2024-36426
What Happened?
Normally, web applications store session tokens in HTTP cookies — a safer place. A cookie tagged as Secure and HttpOnly ensures that the token is harder to intercept or steal.
But here’s the catch. In these vulnerable TARGIT versions, session tokens appear right in the URL, like this:
http://server.example.com/targitclient?sessionToken=ABCD1234EFGH5678
If a user accesses the site using regular HTTP (not HTTPS), anyone on the same network can see the full URL, including the session token. That means anyone on the same WiFi or internal network could hijack your session.
How Does the Vulnerability Work?
Let’s imagine Alice is logging in to her company’s TARGIT Decision Suite dashboard over unencrypted WiFi in a coffee shop. The app constructs a URL like:
http://bi-company.com/targitwebapi/open?sessionToken=abc123def456
This URL is then requested by Alice’s browser, containing the session token. If Bob is sniffing the WiFi (using tools like Wireshark), he can see that full URL and copy the sessionToken value. He just needs to paste the URL into his own browser, and the application will treat Bob as if he were Alice — no password needed.
Worse still, if Alice sends or shares the link to someone, or it appears in logs, proxies, or browser histories, that session token can be silently leaked.
Using Wireshark or similar
GET /targitwebapi/open?sessionToken=abc123def456 HTTP/1.1
Host: bi-company.com
...
2. Attacker grabs the token from the URL
session_token = "abc123def456"
exploit_url = f"http://bi-company.com/targitwebapi/open?sessionToken={session_token}";
# Open in browser or issue HTTP requests
import requests
r = requests.get(exploit_url)
print(r.text)
Session Hijacking: Anyone with the URL (and token) can become you.
- Logs and Referrers: URLs with tokens might show up in analytic logs, browser history, or referrer headers — leaking them further.
- No Security Controls: Even if the site is later switched to HTTPS, tokens are still in URLs, and anyone who previously saw them has access.
Mitigation
Upgrade. TARGIT fixed this in the “Autumn 2023” release. Always use the latest version.
Force HTTPS. Ensure all communications use HTTPS, not HTTP, so tokens can’t be easily sniffed.
Cookie-based Sessions. Modern apps should always store session tokens in cookies with flags like Secure and HttpOnly:
# Example of setting cookies securely (Python Flask example)
from flask import Flask, session, make_response
app = Flask(__name__)
app.secret_key = 'very_secret'
@app.route('/')
def index():
session['logged_in'] = True
resp = make_response('Hello World')
resp.set_cookie('session', session['token'], secure=True, httponly=True)
return resp
References
- NIST CVE-2024-36426 Entry
- TARGIT Official Security Advisories
- OWASP Cheat Sheet: Session Management
- HTTP vs HTTPS
Conclusion
CVE-2024-36426 is a simple but serious vulnerability. Always treat URLs carefully — never include sensitive tokens or secrets in the URL, use HTTPS everywhere, and upgrade your software. Session hijacking attacks are easy and work everywhere—even inside your company network.
Stay secure, and always check your session management!
*This write-up is exclusive to this channel. If you work with TARGIT Decision Suite, upgrade now, and check your web server logs for any suspicious access using session tokens in URLs.*
Timeline
Published on: 05/27/2024 22:15:08 UTC
Last modified on: 08/02/2024 03:37:05 UTC