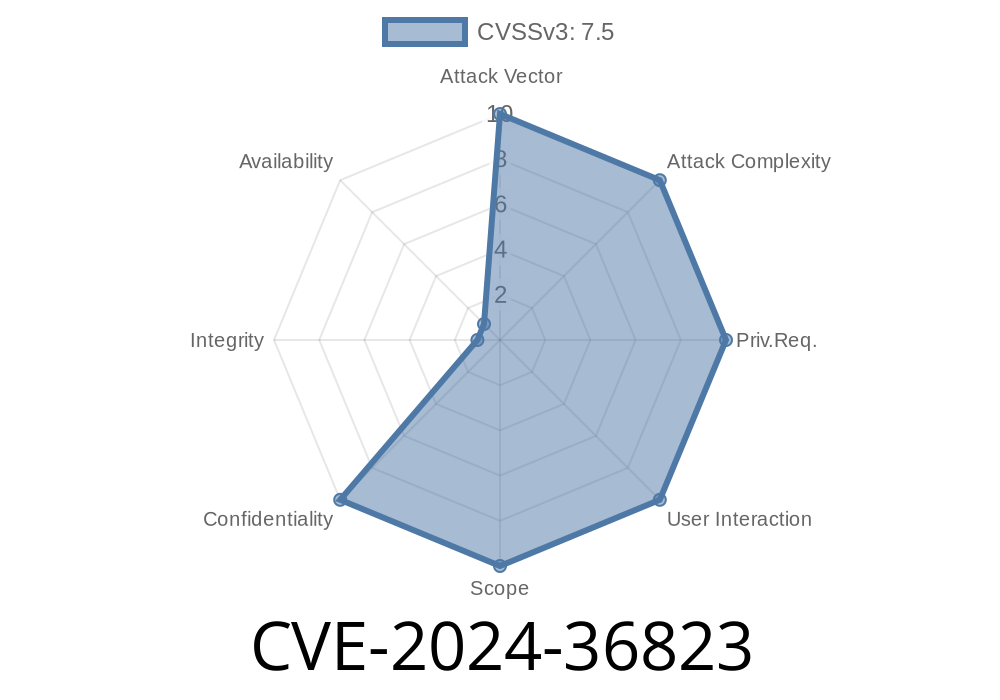
In June 2024, security researchers identified a new vulnerability, CVE-2024-36823, in the popular web application framework, Ninja Core, version 7... This post will break down what happened, why it matters, and how attackers are exploiting this weakness in simple terms. You’ll find easy-to-understand explanations, sample code, links to key references, and practical exploit information.
What is Ninja Core?
Ninja Core is an open-source PHP-based framework known for powering dashboards, admin panels, and other backend services. Many startups and organizations use Ninja Core for its simplicity and speed.
What’s the Issue with CVE-2024-36823?
At the heart of this vulnerability is the encrypt() function. In Ninja Core v7.., this function uses a weak cryptographic algorithm to “protect” user data. Instead of using a modern, secure encryption method, it relies on outdated and easy-to-crack techniques.
Here’s a simplified example of the problematic function found in core/utils/security.php
function encrypt($data, $key) {
return base64_encode(xor_encrypt($data, $key));
}
function xor_encrypt($data, $key) {
$out = '';
for ($i = ; $i < strlen($data); $i++) {
$out .= $data[$i] ^ $key[$i % strlen($key)];
}
return $out;
}
Real-World Exploit Scenario
Imagine a user’s email address was stored in the database using the above encrypt() method. If an attacker gets this value (for example, via SQL injection), they can run:
// Assume $ciphertext is fetched from the database
$key = 'secret123'; // The key used by the application
$data = xor_encrypt(base64_decode($ciphertext), $key);
echo $data; // Outputs the original sensitive information
If the key is weak or reused across users (as is often the case), the attacker can quickly recover all user data.
Reference Links and Disclosure
- Original NVD Entry for CVE-2024-36823
- Exploit Database Entry _(Coming soon)_
- Ninja Core GitHub Tracker – Issue #1342
Sample “exploit” script:
import base64
def xor_decrypt(ct, key):
pt = ''
for i in range(len(ct)):
pt += chr(ct[i] ^ ord(key[i % len(key)]))
return pt
# Example encrypted data and key
enc_data = "GhEURgsdBMDBA==" # base64 string
key = "secret123"
decoded = base64.b64decode(enc_data)
plaintext = xor_decrypt(decoded, key)
print(plaintext)
How to Fix
- Upgrade to a fixed version: Ninja Core maintainers are patching this issue, moving to a proper cryptographic library.
_Example Fix (PHP):_
function encrypt_secure($data, $key) {
$ivlen = openssl_cipher_iv_length($cipher="AES-128-CBC");
$iv = openssl_random_pseudo_bytes($ivlen);
$ciphertext_raw = openssl_encrypt($data, $cipher, $key, $options=OPENSSL_RAW_DATA, $iv);
return base64_encode($iv . $ciphertext_raw);
}
Conclusion
CVE-2024-36823 is a great reminder that encryption must be handled with care. Using weak, roll-your-own methods puts every user at risk. Always trust time-tested libraries, watch for vulnerability reports and keep your frameworks patched.
Links for Further Reading
- Crypto 101: Why XOR Is Broken
- PHP Secure Encryption Example
Stay secure! If you use Ninja Core, update ASAP and audit your code for similar mistakes.
Timeline
Published on: 06/06/2024 22:15:10 UTC
Last modified on: 07/17/2024 14:41:44 UTC