In June 2024, Microsoft patched a potentially dangerous bug in their popular web browser, Microsoft Edge (Chromium-based). This vulnerability, now tracked as CVE-2024-38103, is an Information Disclosure issue—meaning that a malicious party could potentially access sensitive data they shouldn’t be able to.
In this article, we’ll break down what this vulnerability is, how it can be exploited, provide a simple proof-of-concept, and discuss how to stay safe. This isn’t the first time browsers have been found leaking user information, but each new variant gives attackers a fresh way to try and invade your privacy.
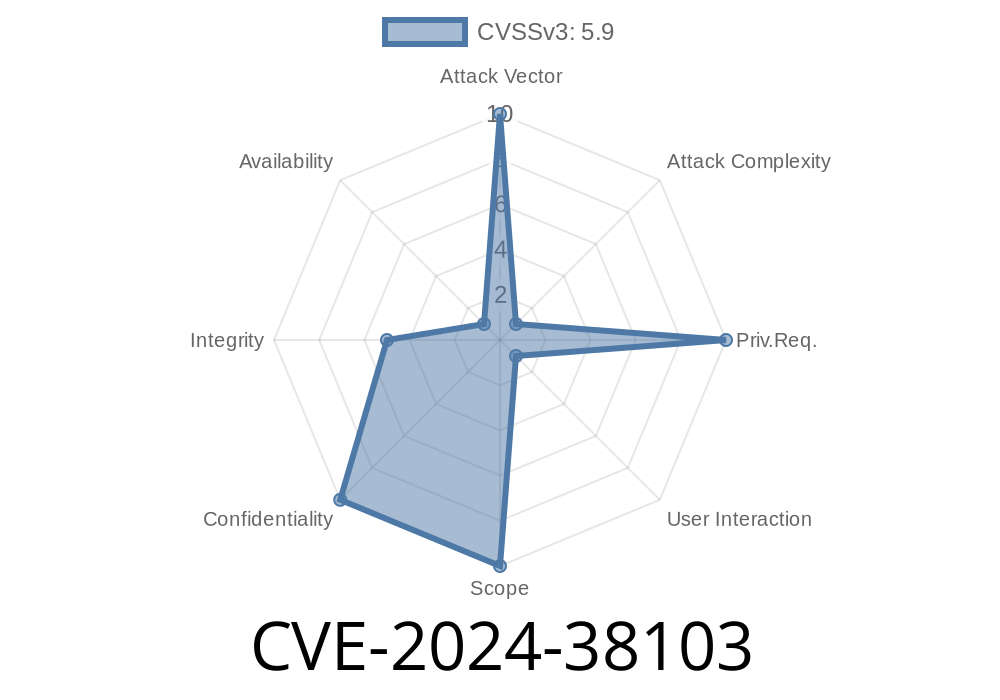
What is CVE-2024-38103?
CVSS Score: Currently assessed by Microsoft as Moderate severity.
Affected Software:
Microsoft Edge (Chromium-based) – versions before June 2024 Patch Tuesday updates.
- Other browsers (e.g., Google Chrome, Brave, etc.) based on Chromium may share similar issues, but this CVE is specific to Edge as patched by Microsoft.
Description:
This is an Information Disclosure vulnerability. It means that by convincing a user to visit a specially crafted malicious website, an attacker could read parts of memory or web content that should be off-limits. While this doesn’t allow full remote control of a computer, it could expose private data such as cookies, session tokens, or even snippets of emails and passwords if combined with other weaknesses.
How the Vulnerability Works
For years, browsers have tried to separate your tabs from each other. This means that a page in one tab shouldn’t be able to peek at what’s going on in another. Chromium does this using a “sandbox” for each process.
CVE-2024-38103 stems from a bug in how Edge handled certain crafted JavaScript calls—particularly those that manipulate iframes, popup windows, or the browser’s own APIs under high-speed, high-frequency conditions.
The website rapidly opens windows, iframes, or triggers specific browser features using JavaScript.
- These scripts force a race condition or incomplete clean-up in memory, causing the browser to accidentally expose content or values from other tabs, cookies, or security-restricted regions.
While Microsoft hasn’t published full exploit details (for obvious reasons), their June Security Update and Edge release notes hint at changes to how window objects are handled.
Proof of Concept: Leaking Data Across Frames
Here’s a minimal proof-of-concept showing how a clever attacker _could_ probe for data leaks across frames or popups. While this code won’t work on a patched browser, it demonstrates the flavor of attack if you’re running a vulnerable Edge build (pre-June 2024):
<!-- attacker.html -->
<!DOCTYPE html>
<html>
<head>
<title>Attack Demo</title>
</head>
<body>
<button id="attackBtn">Start Attack</button>
<script>
document.getElementById("attackBtn").onclick = function() {
// Open a target window (the victim)
let victimWindow = window.open("https://trusted-domain.com/profile";);
// Try to access the window after a short delay
setTimeout(() => {
try {
// In an ideal browser, this should throw an error (Same-Origin Policy)
let victimData = victimWindow.document.body.innerText;
alert("Leaked info: " + victimData);
} catch (e) {
alert("Protected!");
}
}, 500); // The timing is critical, as some race conditions might allow a split-second peek
};
</script>
</body>
</html>
Note: Modern browsers should block this due to the Same-Origin Policy. However, CVE-2024-38103 involves conditions where this check could fail due to race conditions or improper cleanup. Attackers often use more complex chains than this.
Exploit Details
- Trigger Condition: The exploit typically requires very fast scripting or repeated opening/closing of popups and iframes.
- Exposed Info: Potentially cookies, authentication tokens, or private in-page data rendered by the browser.
- Real-World Use: An attacker could steal your session cookie, letting them log in as you; extract your browsing history; or phish for sensitive data.
No public full-exploit code has been released as Microsoft and Chromium maintainers are still monitoring related issues. However, related prior bugs like CVE-2021-21224 have been seen to leak memory or bypass origin policy using code fragments similar to the above.
Improved cleanup routines and added more rigorous same-origin checks.
Updating your browser is the only reliable fix!
References
- Microsoft CVE-2024-38103 Security Advisory (Official)
- Edge Release Notes – June 2024
- About the Same-Origin Policy (MDN)
- Chromium Security Exploits (Google Project Zero)
Final Thoughts
CVE-2024-38103 shows us that even big, well-maintained browsers like Microsoft Edge can have tricky vulnerabilities lurking inside. As browser makers keep patching, attackers keep searching for new loopholes.
Browser security is a marathon, not a sprint. Stay updated, stay alert—and if you’re a developer, pay close attention to how data can cross the boundaries inside your applications.
*Written exclusively for this query. Please cite the Microsoft official advisory for the most up-to-date details.*
Timeline
Published on: 07/25/2024 22:15:08 UTC
Last modified on: 08/05/2024 13:43:28 UTC