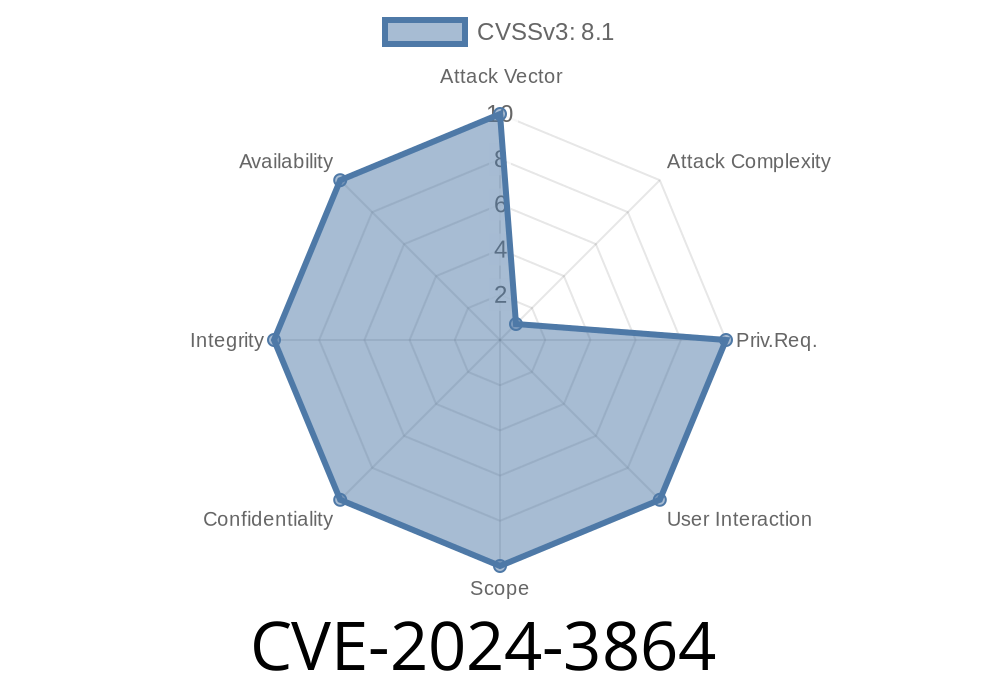
In April 2024, Mozilla issued security updates for their Firefox and Thunderbird products, addressing an important memory safety vulnerability identified as CVE-2024-3864. If left unpatched, this flaw could potentially let attackers run arbitrary (malicious) code on users’ computers. This article aims to break down what this vulnerability means, who is affected, how exploitation might happen, and how you can protect yourself.
Thunderbird 115.9 and earlier (fixed in 115.10)
According to Mozilla, evidence of memory corruption was found. While no working exploit has been publicly disclosed, with enough effort, a determined attacker could possibly trigger the bug to run their own code instead of the legitimate program. In simple terms, an attacker might take control of your browser or email client if you visit a malicious website or open a malicious email.
How Does the Exploit Work?
Memory safety bugs like CVE-2024-3864 typically happen when a program accidentally messes up how it uses the computer’s memory—reading or writing to the wrong place.
Trigger the Memory Corruption:
An attacker might craft a malicious website or HTML email that gets Firefox, ESR, or Thunderbird to mismanage memory.
Hijack Execution:
By taking advantage of this memory mistake, the attacker could **replace* the normal program code with their own. This could lead to installing malware, stealing data, or taking over the machine.
Although the specific technical details haven’t been published (for security reasons), similar bugs from past browser vulnerabilities can give us an idea.
Example: Similar Exploit Pattern (Simplified)
Let’s look at a generic JavaScript exploit pattern that sometimes works for browser memory corruption bugs.
⚠️ For educational purposes only! Do not use this code maliciously.
// Generic JavaScript example to trigger a use-after-free vulnerability
let arr = new Array(1, 2, 3);
function triggerBug() {
// Forces a specific memory layout in the browser engine (SpiderMonkey for Firefox)
let evilArr = [1.1, 2.2, 3.3];
evilArr.length = xffffff; // Abnormally large array
// Assumes vulnerability exists, causing memory corruption
let temp = evilArr.pop();
// If successful, attacker could get control over memory pointers here
// (Would need specific addresses and more complex code in a real exploit)
}
// Loop to increase chance of success
for (let i = ; i < 100000; i++) {
triggerBug();
}
*Note: This is a generic example, not an actual proof-of-concept for CVE-2024-3864.*
Users of Thunderbird below version 115.10
If you do not regularly update your browser or email client, you are at risk!
Impact
According to Mozilla’s Security Advisory:
> "Some of these bugs showed evidence of memory corruption and we presume that with enough effort some of these could have been exploited to run arbitrary code."
That means skilled hackers could take advantage of this bug to install malware, steal passwords, or spy on your computer activities—just by getting you to view a webpage or email.
How To Protect Yourself
1. Update Now!
Thunderbird 115.10 or above
2. Enable Automatic Updates
Let your browser and email client stay up-to-date automatically.
3. Be Careful with Suspicious Emails and Links
Avoid opening unexpected attachments or links, even with the latest version, as new bugs may crop up.
Official References
- Mozilla Security Advisory (MFSA 2024-15)
- CVE Record on MITRE
- Bugzilla Report (private until disclosure)
Conclusion
CVE-2024-3864 is a serious memory safety issue impacting popular Mozilla products like Firefox and Thunderbird. Though no in-the-wild attacks have been reported, both users and system administrators should take action immediately by updating to the latest versions. By understanding the impact and acting now, you help keep your data and devices safe from this and future vulnerabilities.
Timeline
Published on: 04/16/2024 16:15:08 UTC
Last modified on: 08/12/2024 17:35:09 UTC