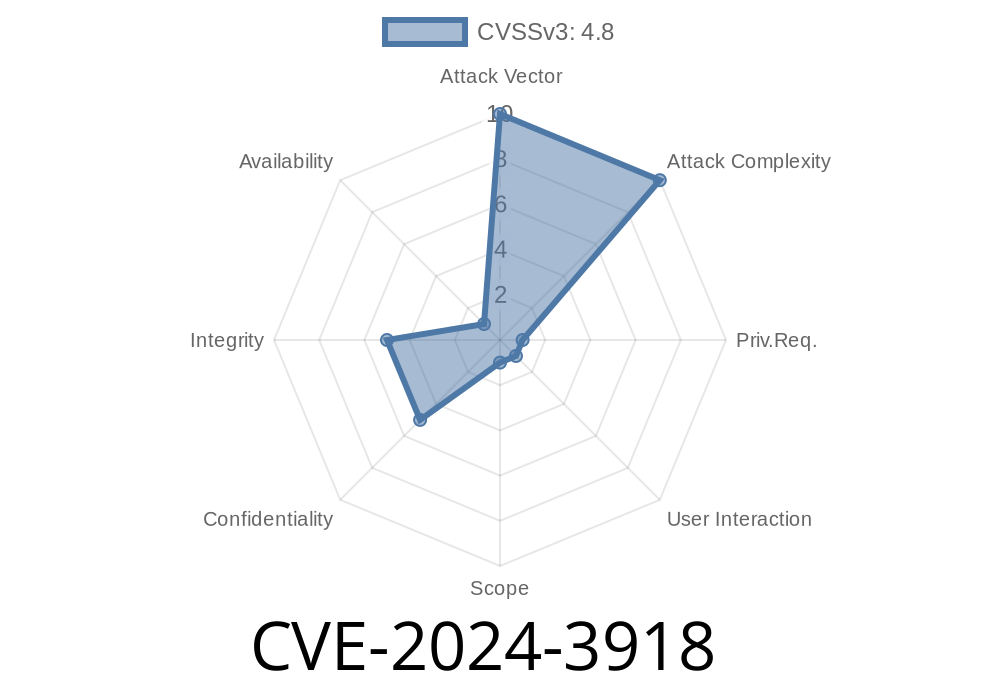
WordPress plugins are a key target for hackers. This long read explores CVE-2024-3918, a serious vulnerability found in the “Pet Manager” plugin for WordPress, up to version 1.4. It lets any high-privilege user (like a Contributor) perform Stored Cross-Site Scripting (XSS), opening doors to major site compromise.
If you use “Pet Manager,” read on to understand the bug, how it works, how it’s exploited, and what you can do.
What is CVE-2024-3918?
CVE-2024-3918 is an identifier assigned to a vulnerability in the Pet Manager WordPress plugin, a plugin commonly used by breeders, shelters, and animal enthusiasts to post pet information.
The bug:
Some pet settings in the backend are not properly sanitized or escaped. This means that if a user with contributor, author, or admin rights enters malicious scripts as part of a pet's settings (like name or description), the code gets saved *as-is* to the database—and then executed in the browser of anyone viewing that pet, including administrators.
Impact:
Problem Location
Inspecting the source (pet-manager.php and related files), Pet Manager saves settings like Pet Name, Description, and other fields with little or no escaping or sanitization:
update_post_meta( $post_id, 'pet_name', $_POST['pet_name'] );
Above, $_POST['pet_name'] is saved directly, with no sanitization.
When displaying the pet
echo get_post_meta($post->ID, 'pet_name', true);
Again, this is echoed right into the page, unescaped. JavaScript in the field runs when the page loads.
`html
Visit the front-end Pet page, or admin area listing pets.
*Result:*
An alert pops up. Replace alert() with any malicious script (keylogger, session stealer, etc.) for real attacks.
Imagine this snippet in the plugin code
// Vulnerable code (no sanitization!)
$pet_name = $_POST['pet_name'];
update_post_meta($post_id, 'pet_name', $pet_name);
// Later in frontend:
echo get_post_meta($post_id, 'pet_name', true);
*Safe code* should be like
$pet_name = sanitize_text_field($_POST['pet_name']);
update_post_meta($post_id, 'pet_name', $pet_name);
echo esc_html(get_post_meta($post_id, 'pet_name', true));
Real-World Attack Scenarios
- Privilege escalation: Contributors inject XSS and trick admins into loading a pet page, resulting in admin session hijack.
Update “Pet Manager” as soon as a patched version is available.
- Limit who can add/edit pets to trusted admins.
- Use plugins like Wordfence or Sucuri to help detect XSS.
References
- Original plugin page
- WPScan Vulnerability Entry (CVE info)
- OWASP XSS Explanation
- Example CVE entry at NIST
Final Thoughts
CVE-2024-3918 is a textbook example of a *stored XSS* caused by missing sanitization and escaping. It shows how quickly a plugin misstep exposes your WordPress site—even from “trusted” users.
Patch quickly, and always follow secure coding practices!
Timeline
Published on: 05/23/2024 06:15:11 UTC
Last modified on: 03/28/2025 21:15:17 UTC