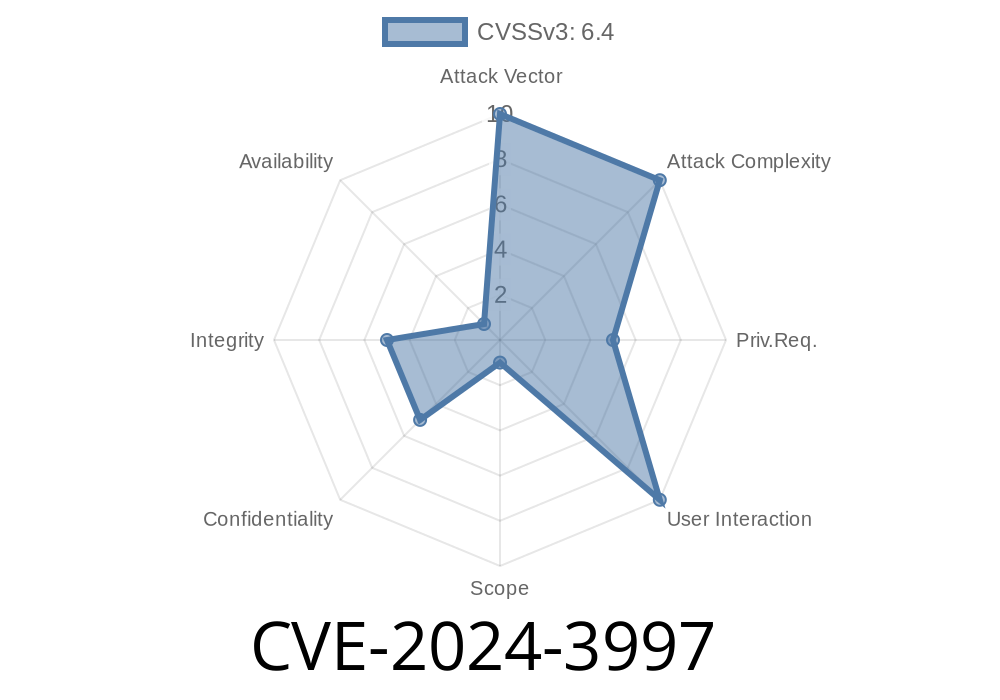
A critical Stored Cross-Site Scripting (XSS) vulnerability has been discovered in the popular WordPress plugin Prime Slider – Addons For Elementor. Registered under CVE-2024-3997, this flaw affects all versions up to and including 3.14.1. Specifically, the vulnerability lies in the plugin’s Pagepiling widget, allowing contributor-level users or higher to inject malicious scripts into WordPress pages. When a user visits these pages, the scripts run in their browser context – potentially leading to site compromise, account hijack, or unauthorized admin actions.
In this article, we’ll break down the technical details, demonstrate a proof-of-concept exploit, and provide mitigation steps.
What Is Prime Slider – Addons For Elementor?
Prime Slider is a plugin that extends the Elementor page builder with feature-rich sliders such as the "Revolution Slider," "Hero Slider," and "Ecommerce Slider." These sliders are commonly used to build stunning, interactive homepages and product showcases.
Root Cause
The plugin fails to properly sanitize and escape user-supplied input in the Pagepiling widget. Consequently, attackers can inject arbitrary JavaScript code, which is executed every time someone visits the affected page.
A Contributor (or higher) logs into the WordPress site.
2. They edit/add a page using Elementor, insert the Pagepiling widget, and provide malicious content to one of its attributes.
3. When any user (including Admins) visits the contaminated page, the injected JavaScript runs in their browser.
Proof-of-Concept Exploit
Below is a simple example of how an attacker might inject a script using the vulnerable attribute in the Pagepiling widget through Elementor.
Add the Pagepiling Widget to the page.
3. Enter the following payload in a widget attribute (for example, the title, custom_id, or any text field that’s rendered unsanitized):
<script>alert('Hacked with CVE-2024-3997!')</script>
Now, every time any user visits this page, the alert executes
!XSS Example
> Note: Replace the payload with a more damaging script to steal administrator cookies or perform malicious actions.
Real-World Impacts
- Account Takeover: If an admin visits the infected page, their authentication cookies could be stolen.
Scan for Malicious Content
Review all Elementor pages for suspicious scripts in sliders/widgets.
Apply Web Application Firewall (WAF) Rules
If a patch is not yet available, use a WAF (e.g., Sucuri, Wordfence, Cloudflare) to block XSS payloads.
Long-term Actions
- Limit Contributor Permissions: Avoid letting untrusted users publish or edit content with widgets.
Regular Security Audits: Frequently scan your site for vulnerabilities and malicious code.
- Monitor Security Feeds: Track updates on WordPress plugin security, such as WPScan.
Timeline and References
- Vulnerability discovered/published: June 2024
- Original advisory: WPScan entry
- Plugin repository: Prime Slider – Addons For Elementor
Conclusion
CVE-2024-3997 is a high-impact, easily-exploited vulnerability affecting thousands of WordPress sites running the Prime Slider plugin. While it requires a contributor account to exploit, many sites have multiple authors or elevated users, making this a very real threat in the wild.
Patch as soon as possible, audit your site’s contributors, and monitor for unexpected content. Vigilance and quick response are key to staying safe until an official fix is released.
Stay safe, and keep your plugins up-to-date!
---
*References:*
- CVE-2024-3997 NVD Entry
- WPScan Report
- Prime Slider WordPress.org
Timeline
Published on: 05/23/2024 11:15:24 UTC
Last modified on: 06/04/2024 17:31:48 UTC