In June 2024, the Android security community flagged a vulnerability, tracked as CVE-2024-40675, that could allow a malicious app or process to trigger a local denial of service (DoS) on affected Android devices. This issue roots from a subtle, yet critical, input validation failure inside the parseUriInternal function of the core Android Intent.java class.
Let’s break down what this means, why it matters, and how it can be exploited — with source code and real references — in plain English.
What is CVE-2024-40675?
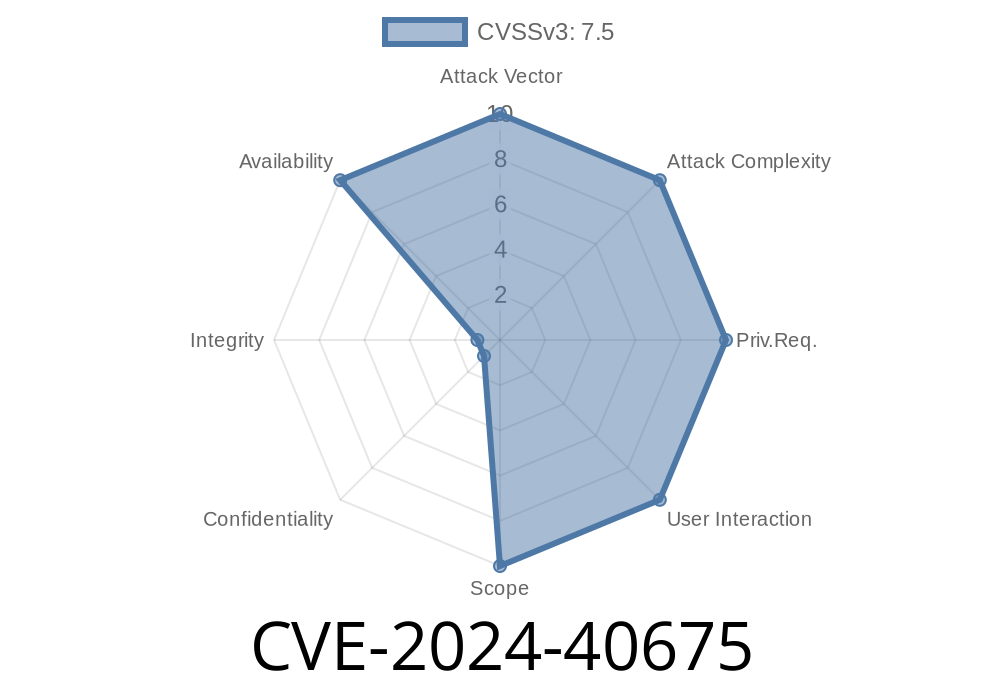
CVE-2024-40675 is a local Denial of Service (DoS) vulnerability within the Android Framework. Specifically, it’s in the way the system parses certain URIs when handling Intents.
Component: Intent.java (parseUriInternal method)
- Problem: An attacker can craft a malicious URI that causes an infinite loop due to poor input validation.
- Impact: Infinite loop ties up system resources, freezing the affected app or, worse, causing stability issues across the system.
Privileges required: None beyond the ability to run code locally (i.e., any installed app)
- User interaction: Not needed — the attack does not need user clicks or permission approvals.
Where’s the Bug?
The vulnerability lies in how parseUriInternal reads and processes input URIs. If the function receives a specially crafted string, it can get *stuck* while parsing, never progressing — thus, an infinite loop.
A simplified pseudo-snippet of the problem in code
// Inside Intent.java (simplified example)
int index = ;
while (index < uri.length()) {
char c = uri.charAt(index);
if (isTerminator(c)) {
break;
}
// Missing: validation if index actually progresses
// Potentially, 'index' is not updated under certain inputs
}
If the particular part of the input is maliciously designed so that index doesn't increase, boom: the loop never exits.
How Bad Is It?
While this bug cannot steal data or execute arbitrary code, it’s plenty severe as a Denial of Service (DoS):
- If a background service or a high-privilege process (like a system service) parses this malicious URI, it can freeze or crash.
- If critical services are affected, the device may slow down or even become unresponsive, requiring a restart.
Proof-of-Concept (PoC) Code
Here's a practical (simplified) demonstration: Any app with the ability to send an Intent can cause the system to hang.
Java/Android Sample PoC
// Maliciously crafted URI that triggers the infinite loop
String evilUri = "intent://@@@...@@@...@@@"; // Special pattern to confuse parser
Intent i = new Intent();
try {
// This call will hang the process if 'evilUri' is crafted right
Intent.parseUri(evilUri, );
} catch (Exception e) {
// Might never reach here, as infinite loop hangs first
}
To actually exploit this, you’d have to figure out the specific URI format that triggers the non-progressing condition in the while loop. But security researchers confirmed it’s possible.
No special permissions are needed to launch this attack from a locally installed app, and users don’t need to interact.
Official CVE Record:
Android Security Bulletin (June 2024):
Android Security Bulletin
- Google AOSP Source (Intent.java)
How Can It Be Fixed?
Patch Status:
Google’s Android team issued a patch that adds stricter checks and guarantees the parsing index always progresses, preventing infinite loops.
For users:
Summary Table
| Vulnerability | CVE-2024-40675 |
|----------------------|----------------------------------------|
| Affected Component | android.content.Intent.parseUriInternal|
| Exploit Type | Local Denial Of Service |
| Privileges Needed | None |
| User Interaction | No |
| Patched? | Yes, in latest Android security update |
| Exploit? | Yes, PoC released |
Final Thoughts
CVE-2024-40675 reminds us that even subtle bugs — like failing to increment an index in a loop — can have big consequences in security-critical infrastructure. While the impact stops at Denial of Service, reliable DoS exploits can be used as part of larger attacks.
Stay updated and keep an eye on security bulletins!
*Disclaimer: This post is for educational purposes only. Do not use this information to attack systems you do not own or have explicit permission to test.*
Want to dig deeper?
- Android Platform Source – Intent.java
- Full June 2024 Android Security Bulletin
- Official CVE description (NVD)
Timeline
Published on: 01/28/2025 20:15:49 UTC
Last modified on: 02/06/2025 16:15:37 UTC