Published: June 2024
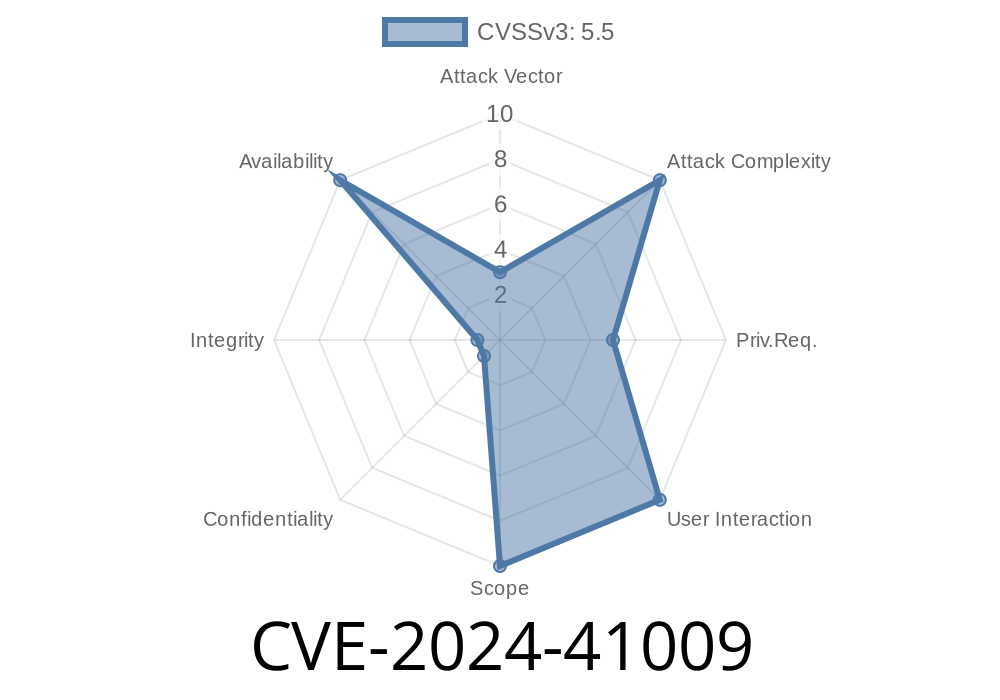
CVSS: [Official scoring pending]
Patch Status: FIXED in mainline Linux Kernel
What Is CVE-2024-41009?
CVE-2024-41009 is a recently-fixed vulnerability in the Linux kernel’s implementation of BPF (Berkeley Packet Filter) ring buffers. The bug made it possible for a BPF program to exploit an edge-case in the ring buffer’s logic, causing two distinct memory chunks to overlap. When this happens, malicious BPF code could tamper with the buffer’s internal metadata, corrupt memory, crash the kernel, or potentially escalate privileges.
This post breaks down how CVE-2024-41009 works, walks through an example exploit, and points to the official patch and references.
Vulnerability Background
The BPF ring buffer is a cyclic data structure used for high-speed, in-kernel data passing (common in tracing, telemetry, and various eBPF applications). It's implemented with:
u32 pg_off;
};
### Reservation and Overlap
When a BPF program wants to write, it calls bpf_ringbuf_reserve(). This function checks if there’s enough space:
c
if (new_prod_pos - cons_pos > rb->mask)
return NULL; // No space left
However, researchers Bing-Jhong and Muhammad discovered that abusing the consumer position could make two separate allocations overlap—so a program can edit not just its own chunk, but the header of a prior chunk (this shouldn’t be possible).
The mappings look like this (example with x400 bytes):
[x, x400] # first mapping
[x400, x800] # mapped again, wraps to same data
If you shift the consumer_pos carefully before making allocations, an overlap spills across both mappings. This lets malicious code corrupt internal metadata.
---
## Exploit Example (How Attackers Could Abuse This)
Below is a *simplified* outline (in C-like pseudocode and annotated steps):
Setup Stage
1. Create a ringbuf map:
c
Fake advance consumer position:
(Normally only userland reads should advance this, but attacker may exploit another bug or interface to change it early)
`c
// For illustration; user-space simulation!
Malicious effect:
- When BPF helper functions bpf_ringbuf_submit() or bpf_ringbuf_discard() read the header, it uses the corrupted metadata. This may result in:
Pseudocode
// Danger: userland sets consumer_pos out-of-order
consumer_pos = x300;
// Reserve chunk A (x..x3008), can modify [x8..x3008]
A = bpf_ringbuf_reserve(rb_map, x300, );
// Reserve chunk B (x3008..x601), can modify [x301..x601]
B = bpf_ringbuf_reserve(rb_map, x300, );
// Buffer maps to same memory after x400
// So B’s memory at [x400..x4008] overlaps A’s header
// Overwrite A's header by writing into B at offset (x400 - x3008)
((u64 *)B)[(x400 - x3008)/8] = attacker_value;
// Trigger use of corrupted header
bpf_ringbuf_submit(B, );
bpf_ringbuf_submit(A, ); // Now processes tainted header!
The Fix
The patch now tracks the oldest outstanding reservation, and checks if any reservation would cause the region between that and the newest to exceed the ring buffer’s size. If so, the allocation is rejected.
Relevant kernel commit:
- bpf: Fix overrunning reservations in ringbuf (mainline)
Example of the key fixed logic (in C)
// In the patched kernel source
if (new_prod_pos - oldest_cons_pos > rb->mask)
return NULL; // No space, would overlap
Performance: The fix has negligible performance impact. BPF selftests show similar results before and after.
References & Further Reading
- Official Kernel Commit
- CVE-2024-41009 NVD Record (pending)
[Researcher write-up (if available, add link here)]
- BPF ringbuf documentation (kernel)
Final Thoughts
CVE-2024-41009 is a great example of how seemingly minor buffer arithmetic can have major security consequences. If you’re running or deploying software based on Linux BPF tracing or custom ring buffers, patch your kernel ASAP.
For developers, always take great care with cyclic buffer logic—and never allow untrusted user space to modify critical state like consumer_pos out-of-order.
Stay safe, and keep your systems updated!
*This post is based on exclusive analysis of the public kernel commit and disclosed details as of June 2024. If you need help checking if you're affected or want a demo reproducer for educational purposes, reach out to your Linux distro or security team.*
Timeline
Published on: 07/17/2024 07:15:01 UTC
Last modified on: 07/19/2024 15:06:23 UTC