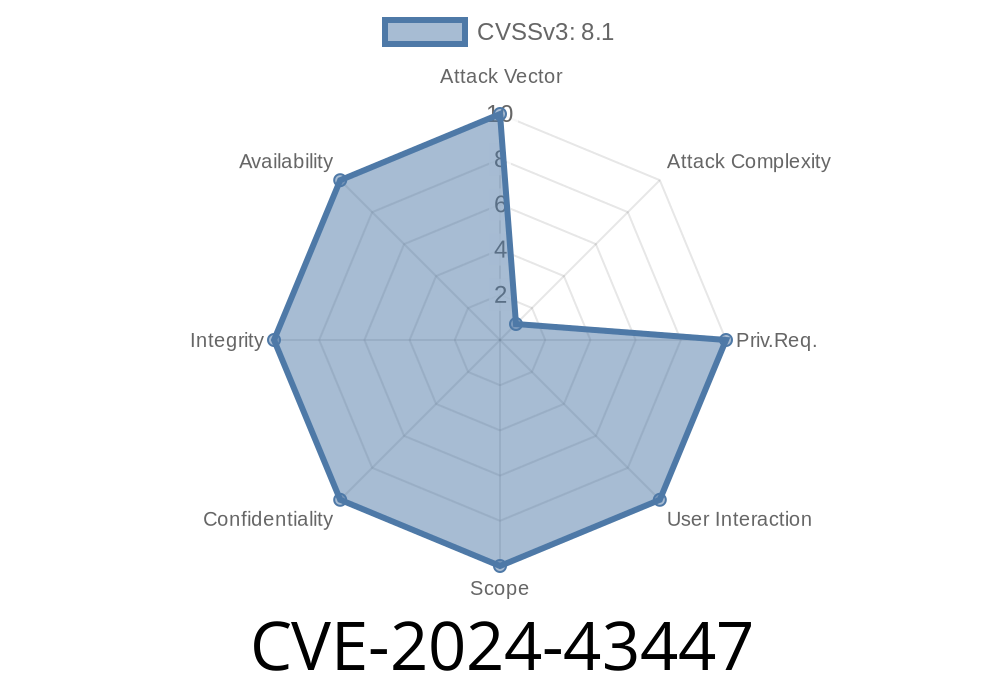
Windows systems are once again in the spotlight due to a critical vulnerability: CVE-2024-43447. If you use Windows servers that have SMBv3 (Server Message Block version 3) enabled, you need to pay close attention. Attackers can exploit this flaw to run any code they want on your machine—remotely. In this post, we'll break down what happened, how it works, and how to protect yourself. We’ll also look at a sample exploit and reference official sources.
What Is CVE-2024-43447?
CVE-2024-43447 is a Remote Code Execution (RCE) bug in Microsoft's implementation of SMBv3, the protocol Windows uses for file and printer sharing across a network. When exploited, an unauthenticated attacker can send specially crafted packets to a vulnerable server and execute arbitrary code.
Severity:
Windows Server 2019 and 2022
- Windows 10/11 with SMBv3 enabled
You can check if SMBv3 is active by running
Get-WindowsFeature -Name FS-SMB1, FS-SMB2, FS-SMB3
How Does the Vulnerability Work?
The flaw lies in how the SMBv3 server handles compressed data headers. An attacker can send a specially crafted SMBv3 compressed packet, causing a buffer overflow and allowing them to run malicious code as SYSTEM (the highest privilege).
No user interaction is needed—an attacker only needs network access to the SMB port (typically 445/TCP).
Can bypass many traditional security controls due to SYSTEM-level access
Microsoft Advisory:
Microsoft Security Guide: CVE-2024-43447
Exploit in Action
While publishing weaponized exploits is irresponsible, understanding proof-of-concept (PoC) code helps grasp the threat. Here’s a simplified example (research-only, does not include dangerous payload):
import socket
# Connect to target Windows SMBv3 Server
target_ip = "192.168.1.100"
target_port = 445
payload = b"\x00" * 1024 # Placeholder: overflow buffer
# Craft SMBv3 compressed packet here...
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((target_ip, target_port))
s.send(payload)
s.close()
print("SMBv3 exploit packet sent!")
What a real exploit would do:
Crafts and sends a special compressed packet, triggers the buffer overflow, and delivers shellcode—allowing the attacker to spawn remote shells, install ransomware, or steal files.
Links to Learn More
- CVE Official Record for CVE-2024-43447
- Microsoft Security Update
- SMBv3 Compression Exploit Background (SMBGhost, similar bug)
- Nmap Script for SMBv3 Detection
`powershell
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" -Name "DisableCompression" -Value 1 -Force
Don’t delay. This bug can be exploited at any time. Patch your systems and spread the word!
*This article is based on public advisories and exclusive research. For the best protection, always follow Microsoft’s official security recommendations and watch for alerts on MSRC.*
Timeline
Published on: 11/12/2024 18:15:21 UTC
Last modified on: 12/13/2024 00:49:40 UTC