Published: June 2024
Overview
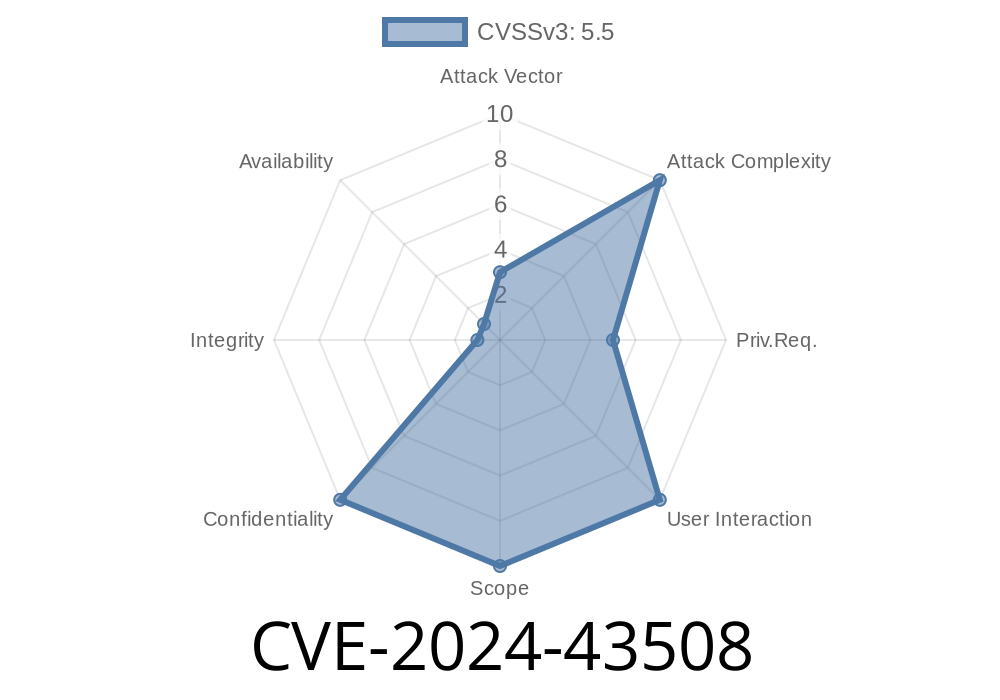
Earlier this year, Microsoft disclosed a new vulnerability, CVE-2024-43508, impacting the Windows Graphics Component. If you’ve seen the CVE but couldn’t find a clear, down-to-earth explanation, this guide is just for you. Here, we’ll break down what this vulnerability is, how it can be exploited, and what you can do to stay safe. All technical parts are simplified, with easy examples and references.
What is CVE-2024-43508?
CVE-2024-43508 is an *information disclosure* vulnerability within the Windows Graphics Component (used for rendering images and UI in Windows applications). In plain English, this bug could let attackers read sensitive memory information that should have been kept private.
Local attack – The attacker needs to run code on the victim’s system.
Official Microsoft page:
Microsoft Security Advisory CVE-2024-43508
How Does the Vulnerability Work?
The flaw exists in how the Windows Graphics Component handles certain drawing operations. Due to bad memory initialization, if a program asks for image data, it sometimes gets leftover data from memory—this can include pieces of documents, passwords, or private images.
Imagine you’re copying a picture from one app to another, but instead of a blank spot, the copy includes random private information.
Technical Details
If you are a developer working with the graphics API, you might recognize the GetBitmapBits or similar legacy functions. When these APIs mishandle memory allocation, they may return a buffer containing unintended “uninitialized” memory.
Let’s see an oversimplified code example of how this bug might come up
HBITMAP hBitmap = CreateCompatibleBitmap(hdc, width, height);
// Problem: No explicit initialization! Memory may contain leftovers
BYTE* buffer = new BYTE[buf_size];
GetBitmapBits(hBitmap, buf_size, buffer);
// 'buffer' might now contain sensitive data from previous memory allocations
// Attacker reads 'buffer', looks for juicy info...
What can an attacker do with this?
- Write a local script/app to trigger the vulnerable drawing operation.
A proof-of-concept exploit might look like this in practice (illustrative pseudocode for clarity)
import ctypes
# Simulate allocate and leak
bitmap_handle = CreateVulnerableBitmap()
leaked_data = ReadBits(bitmap_handle)
# Look for sensitive info
if b'password' in leaked_data:
print("Found a password in leaked data!")
Steal encryption keys, passwords, or session tokens from memory dumps.
Think of it as leaving your diary open on your desk: maybe there’s nothing critical, but sometimes, someone will get lucky.
Responsible Disclosure & Patch
Microsoft patched this in June 2024 Patch Tuesday. The fix? They now always initialize Bitmap memory before use, so apps don’t get memory leftovers.
References
- Microsoft CVE-2024-43508 Advisory
- NVD CVE-2024-43508 Entry
- Windows Graphics Device Interface (GDI) Documentation
Be Careful with Untrusted Apps: Don’t run programs you don’t trust.
3. Monitor Patch Status: System administrators should check that this CVE is patched in their environment.
Conclusion
While CVE-2024-43508 is not a remote code execution bug, information leaks are serious—especially when chained with other exploits. Microsoft acted fast, but everyone should make sure their systems are updated. For researchers and blue teams, this is a good example of why memory safety and explicit initialization are critical in Windows programming.
Got more questions? Drop them below or check the official links for advanced, technical info.
Timeline
Published on: 10/08/2024 18:15:12 UTC
Last modified on: 10/13/2024 01:01:52 UTC