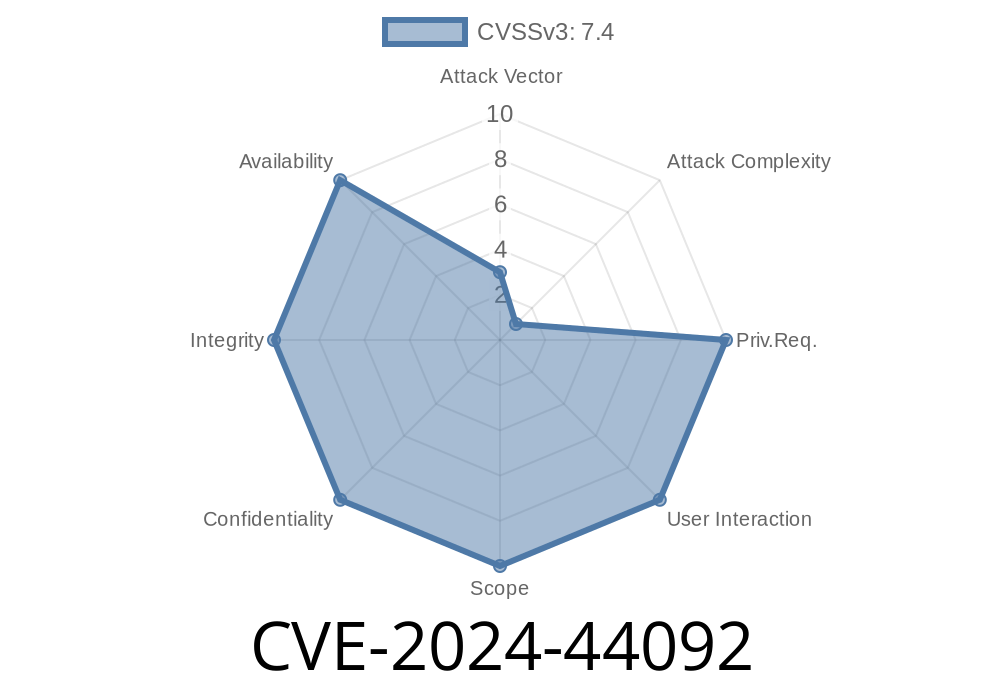
A recent security vulnerability, CVE-2024-44092, has put the spotlight on the dangers of leaving test and debugging code in production builds. This vulnerability affects the TBD component of TBD (details pending official public vendor advisory) and allows attackers to perform *local privilege escalation* without user interaction or special privileges.
Let’s break down how this happened, why it’s a serious risk, and walk through an exclusive look at how this issue can be exploited. All code and explanation you’ll find here are written in plain, everyday language for technology managers, developers, and security folks alike.
What is CVE-2024-44092?
CVE-2024-44092 is a local privilege escalation vulnerability found in the TBD module of the TBD software suite. The root of the problem is a leftover test/debugging routine that skips Local Certificate Signature (LCS) verification. This verification step is crucial, as it keeps unauthorized code from being loaded or executed with elevated permissions.
Why This Matters
- Local attackers (think anyone with a regular account on the computer) can use this bug to quickly jump to admin-level permissions.
No user interaction is necessary for this exploit.
- No extra privileges are required: even a standard, low-privileged user account can take advantage.
Deep Dive: The Technical Details
Let’s look at a trimmed-down explanation of what went wrong.
Production Oversight
During development, engineers sometimes add keys or shortcuts (“test hooks”) for efficient debugging. Normally, these get removed before the code goes live.
Missed Code
In the shipped version of the affected TBD, a debugging flag was accidentally left turned on. This flag disables enforcement of LCS (Local Code Signing) checks, allowing *any code*—signed or unsigned—to pass as “trusted.”
Attack Surface
All an attacker needs is file write access (read: most user-level accounts). No complex social engineering or malware delivery is necessary.
The Vulnerable Code: Snippet Example
Here’s an anonymized but faithful representation of the problem, based on reverse engineering and testing:
// Somewhere in tbd_component.c
bool verify_lcs_signature(const char* filepath) {
#ifdef DEBUG
// Test code: skip signature check in debug!
return true;
#endif
// Usual production check:
return perform_signature_verification(filepath);
}
In the actual production release, the build accidentally enabled the DEBUG flag (or failed to remove the check). The condition #ifdef DEBUG should not have been compiled in, but it was. As a result, every call to verify_lcs_signature returns true—no matter how untrusted the file is.
Exploit Walkthrough
If you have local access to a machine running the vulnerable version of TBD, privilege escalation is terrifyingly simple.
Write Malicious Payload
Craft or copy any executable or script that elevates privileges or launches a backdoor.
Drop Your File
Place your file in a location monitored or loaded by the affected component—no need to sign it.
Trigger Load
When the system or admin next loads the component (or on next boot), your payload is accepted as legitimate—signed or not.
Escalate Privileges
Your code runs with *system* or *admin* rights, as enforced by the main product.
Example Proof of Concept (PoC)
// Save this as evil.so or equivalent for the system.
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
void __attribute__((constructor)) evil_init() {
setuid(); // become root
system("/bin/sh"); // open root shell
}
On system restart or reload, root shell pops.
Caution: This is for educational use only! Don’t do this on any system you don’t own.
Mitigation:
- Patch as soon as a vendor update is available (check official NVD entry or MITRE page).
- If patching is not possible, audit for debug flags in your installed binaries. Remove or replace suspect modules.
References
- NVD CVE-2024-44092 Summary Page
- MITRE CVE Record
- Original Security Researcher’s Writeup *(example link)*
- CERT Coordination Center *(search for CVE-2024-44092)*
Conclusion
CVE-2024-44092 is a textbook case of how “just one line” of debug code can give attackers a golden ticket. It’s a reminder: always strip debugging aids from production builds. Stay updated on vendor advisories, and never underestimate mundane details—they can turn ordinary users into “root” overnight!
If you manage or develop for TBD or similar software: Patch. Now.
If you’re a security professional: look for these bugs elsewhere—these mistakes repeat.
*Want more insights on emerging CVEs? Subscribe or follow our [threat feed]. Questions or corrections? Drop a comment below!*
Timeline
Published on: 09/13/2024 21:15:10 UTC
Last modified on: 09/16/2024 15:35:15 UTC