Table of Contents:
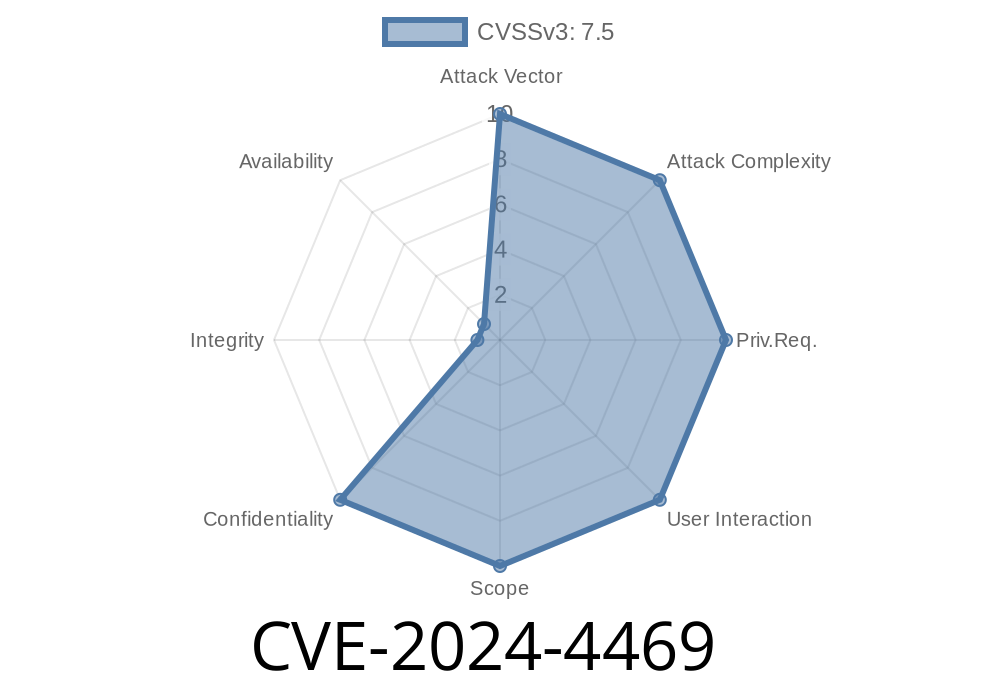
What Is CVE-2024-4469?
In May 2024, security researchers revealed a serious Server-Side Request Forgery (SSRF) vulnerability in the popular WordPress plugin, WP STAGING (before version 3.5.). This plugin is widely used for backing up, cloning, and migrating WordPress websites.
CVE-2024-4469 means that administrators in some WordPress multisite configurations could abuse the plugin to make the server send requests to any URLs they chose—including services inside the internal network, cloud metadata endpoints, or whatever they liked.
Why Is SSRF Dangerous?
Server-Side Request Forgery (SSRF) lets an attacker force the server to make requests on their behalf. This could let them:
Steal confidential data
In a WordPress Multisite setup, this is a bigger issue since admins of subsites are often not fully trusted.
Who Is Really at Risk?
The vulnerability *mainly* affects WordPress Multisite installations where multiple administrators operate different sites under one umbrella. In such cases, a subsite admin (who you might not fully trust) could abuse this flaw.
Single-site installations with one admin are much less at risk, unless the admin’s account is already compromised.
The Core Issue
Older versions of the WP STAGING plugin allowed anyone with the administrator role to supply arbitrary URLs or hostnames when triggering certain backup or migration actions. The plugin would then fetch data or make requests to those URLs *without filtering*—classic SSRF.
Insecure Code Pattern Example
Let’s assume the following (simplified) code that triggers the backup process, using user-supplied input:
// (Pseudo) Code Example - Vulnerable Pattern
if (current_user_can('administrator')) {
$url = $_POST['backup_source_url']; // Admin input (unfiltered)
$response = wp_remote_get($url); // Server fetches the chosen URL!
// ...do something with $response...
}
What’s wrong here?
Exploit Example: Sending the Server to Internal Resources
Suppose you’re a (not fully trusted) admin on a multisite setup.
1. Login to WP Admin
Log in as a subsite administrator with access to the WP STAGING plugin.
2. Initiate a Backup with a Malicious Source
When triggered, supply the URL as an internal endpoint—for example, the AWS EC2 metadata service:
http://169.254.169.254/latest/meta-data/iam/security-credentials/
Here's a cURL example of what the underlying HTTP request would look like
curl -X POST -d 'backup_source_url=http://169.254.169.254/latest/meta-data/iam/security-credentials/' \
-b 'wordpress_logged_in_cookies' \
https://victim-site.com/wp-admin/admin-ajax.php?action=wpstg_backup
3. The Server Makes the Request
Because there's no restriction, the server tries to access the AWS metadata service, and the output may end up readable by the attacker.
Other attack targets:
- Localhost services (e.g., http://127...1:3306 to probe the MySQL server)
- Internal APIs (http://internal-api.local/secret)
How Was This Discovered?
The vulnerability was reported to WP STAGING developers and made public as CVE-2024-4469 (NVD reference).
Issue: SSRF via unfiltered admin input
Further technical write-ups followed on specialist security blogs and WordPress vulnerability aggregators (see links below).
Audit for Suspicious Use:
Check logs for odd backup/migration jobs with weird URLs.
Further Reading and References
Official Advisory:
- WPScan Entry
- National Vulnerability Database - CVE-2024-4469
What is SSRF?
- OWASP: Server Side Request Forgery (SSRF)
Plugin Info:
- WP STAGING on WordPress.org
Final Thoughts
If you’re running WP STAGING on multisite WordPress, update *immediately*. This flaw opens up a real attack vector in shared admin setups—don’t wait for trouble.
*Written exclusively for this post. Please reference original advisories for the latest information.*
Timeline
Published on: 05/31/2024 06:15:13 UTC
Last modified on: 03/18/2025 15:15:56 UTC