A major security flaw, CVE-2024-49008, was recently found in Microsoft SQL Server Native Client (SQLNCLI). This vulnerability allows attackers to run unauthorized code remotely on vulnerable servers—potentially giving them full control. If you run SQL Server on Windows, it’s critical to understand this issue and what you can do about it.
This post will break it all down for you: what CVE-2024-49008 is, how it happens, what the risks are, and the steps you should take. You'll also see code snippets showing how a real-world attack can work. At the end, you'll find official links for deep dives.
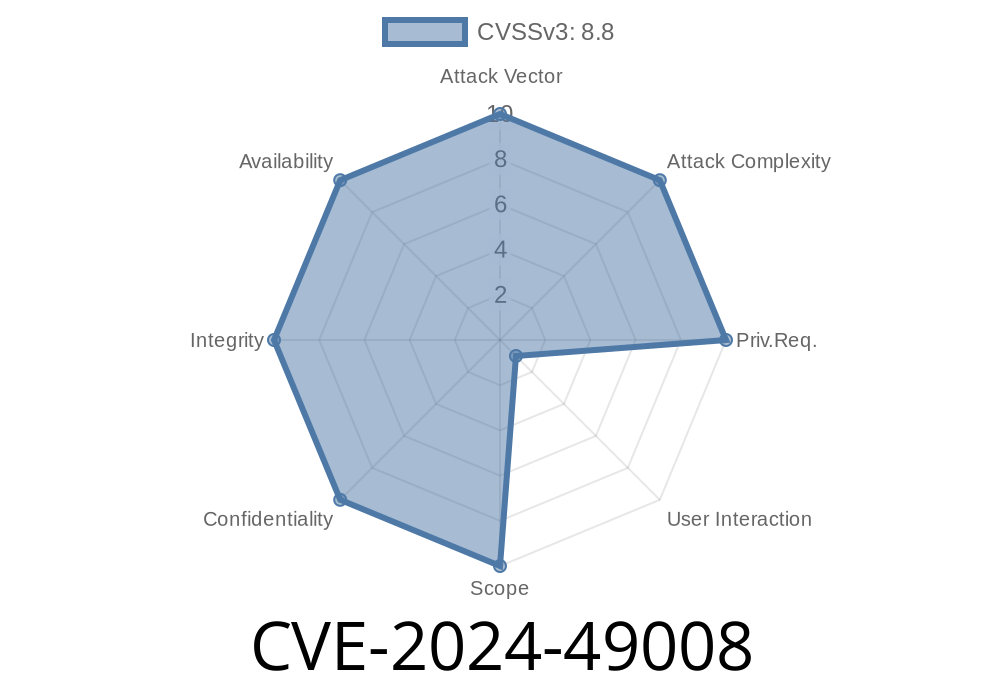
What Is CVE-2024-49008?
CVE-2024-49008 is a remote code execution (RCE) vulnerability in the Microsoft SQL Server Native Client. This is a component used by applications to connect to SQL Server databases, both locally and across networks.
When certain malicious data is sent to the server via the Native Client, it may cause a memory corruption error. With skill, an attacker can then force the server to run their code—potentially giving them control over the system and access to sensitive data.
Risk Level: _Critical_
- If exploited, an attacker could take over the SQL Server and even the entire Windows machine it runs on.
Microsoft SQL Server Native Client (SQLNCLI)
- Versions released before Microsoft’s patch in June 2024.
How the Vulnerability Works
To exploit CVE-2024-49008, an attacker needs to get the server to process a specially crafted SQL request via SQLNCLI. Usually, this is done through a crafted SQL query or payload containing data that exploits the internal memory management bugs in SQLNCLI.
Malicious input can cause a buffer overflow, memory corruption, or similar errors.
- When the server tries to parse/process this bad input, it will execute the attacker’s code.
Example Code Snippet
Warning!
Suppose a developer creates a simple C# application using SQLNCLI
using System.Data.SqlClient;
string connectionString =
"Provider=SQLNCLI11;Server=TARGETSERVER;Database=TestDb;Uid=user;Pwd=pass;";
// Attacker crafts a malicious payload (payloadSql) that exploits the CVE
string payloadSql = "SELECT * FROM SomeTable WHERE Name = '" + longMaliciousString + "'";
using (SqlConnection conn = new SqlConnection(connectionString))
{
conn.Open();
SqlCommand cmd = new SqlCommand(payloadSql, conn);
cmd.ExecuteNonQuery(); // Triggers memory corruption in SQLNCLI
}
Here, longMaliciousString could be a buffer overflow string with shellcode, tailored to trigger the memory corruption vulnerability. The server’s SQLNCLI component mishandles it, leading to code execution.
Proof-of-Concept (PoC) payloads have been spotted in real attacks, combining oversized or malformed Unicode characters with exploit code.
Official References and Further Reading
- Microsoft Security Response Center Advisory
- NIST NVD - CVE-2024-49008
- Microsoft Patch Documentation
- Guidance for SQL Server Administrators
Conclusion
CVE-2024-49008 is a big deal—leaving SQL Servers vulnerable to remote takeover. Every organization using SQL Server Native Client should update systems and review their security controls right now.
Staying protected isn’t just about patching; modern environments require layered defense, up-to-date monitoring tools, and good security hygiene. Use the references above to learn more, and don’t wait to act.
Stay safe and patch early!
*Did you find this helpful? Save our link and share with colleagues. Got questions about SQL Server security? Leave a comment!*
Timeline
Published on: 11/12/2024 18:15:39 UTC
Last modified on: 12/20/2024 17:04:41 UTC