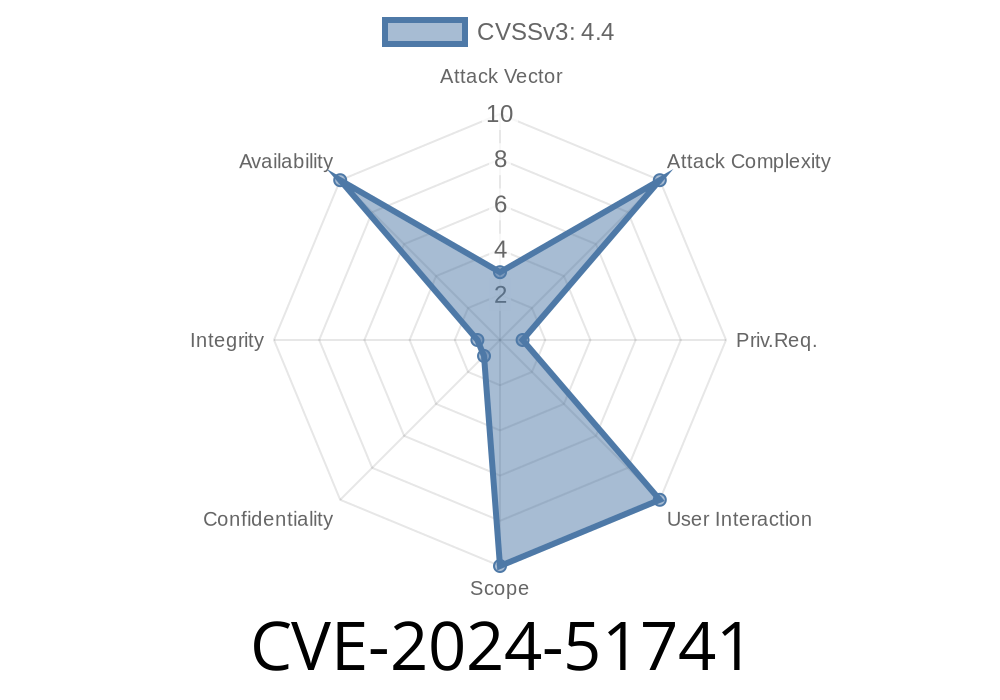
Redis, an open-source, lightning-fast in-memory database, is used everywhere—from caching web pages to powering real-time messaging platforms. But recently, the Redis team disclosed a serious security bug: CVE-2024-51741. This flaw lets a logged-in attacker with the right privileges crash a Redis server just by crafting a sneaky access control list (ACL) selector. Below, I’ll break down exactly what this vulnerability is, how it works, and what you should do now.
What is CVE-2024-51741?
CVE-2024-51741 is a vulnerability in Redis’s ACL (Access Control List) system. If an attacker already has authentication and enough privileges, they can create a malformed ACL selector. When Redis parses this selector—either via a command or a script—it can cause a server panic. In Redis, a panic usually means it instantly terminates itself, causing a denial of service (DoS).
Here’s the official advisory:
- GitHub Advisory GHSA-95j5-8prr-36wq
- NVD Entry
How Redis ACL Works
ACLs in Redis are like bouncers in front of a nightclub—they say who gets in and what they can do. You can add users, restrict them to certain commands, and even specify what keys they can touch. All of this uses “selectors” to fine-tune access.
A normal ACL rule might look like this
ACL SETUSER alice +GET +SET ~foo:*
This means:
only on keys starting with foo:
But because Redis’s ACL system is so flexible, it can also be sensitive to badly formed rules, as in this exploit.
The Heart of the Vulnerability
If a user with enough power creates an improperly formatted or intentionally tricky ACL selector, it confuses the Redis parser. Instead of rejecting the bad rule, the Redis server sometimes panics (it crashes itself to avoid undefined behavior). That can make your database go offline instantly—a real headache if you’re running an online service or a critical application!
Redis 7.4.x before 7.4.2
You’re safe if you’ve updated to 7.2.7, 7.4.2, or later!
Let’s see a simplified example.
Suppose you have a Redis admin user testuser with all the needed privileges. This user sets a malformed ACL selector like this:
# This is a deliberately invalid ACL rule to trigger the bug
ACL SETUSER testuser on +@all ~{"pattern":"*"}
Or, more specifically, using an invalid selector structure
ACL SETUSER testuser on ~[pattern="*"]
The exact structure a successful exploit needs might differ and would depend on the parser bug referenced in the patch. The idea is to provide syntactically incorrect or unexpected combinations, like nested objects or invalid attribute names, using the ACL selector.
If you’re running a vulnerable version, running this command can trigger a crash
redis-cli
127...1:6379> ACL SETUSER testuser on ~{"pattern":"*"}
(error) Server closed the connection
After issuing the command, the Redis server process will panic and shut down, resulting in denial of service.
In the logs, you’ll see something like
PANIC: Invalid ACL selector parsed
terminate called after throwing an instance of 'std::logic_error'
...
Aborted (core dumped)
If managed by systemd or another service supervisor, Redis may auto-restart, but every attempt to process the bad selector will repeat the panic.
Good news: The Redis team squashed the bug quickly. It’s fixed in
- Redis 7.2.7
- Redis 7.4.2
Update right away if you’re running anything older!
References
- GitHub Security Advisory
- NVD - CVE-2024-51741
- Redis 7.2.7 Release Notes
- Redis 7.4.2 Release Notes
Bottom Line
CVE-2024-51741 proves you need to keep your databases patched and limit who can change sensitive settings. If a trusted user account is compromised, this kind of bug can take your entire Redis system offline.
Stay safe:
- Update to Redis 7.2.7/7.4.2 or higher
Audit your users
If you have Redis exposed to the Internet or let lots of people create accounts, it’s especially urgent. Stay patched and stay online!
*Feel free to share this post with your team or security channel to help others stay ahead of the latest Redis bugs.*
Timeline
Published on: 01/06/2025 22:15:09 UTC