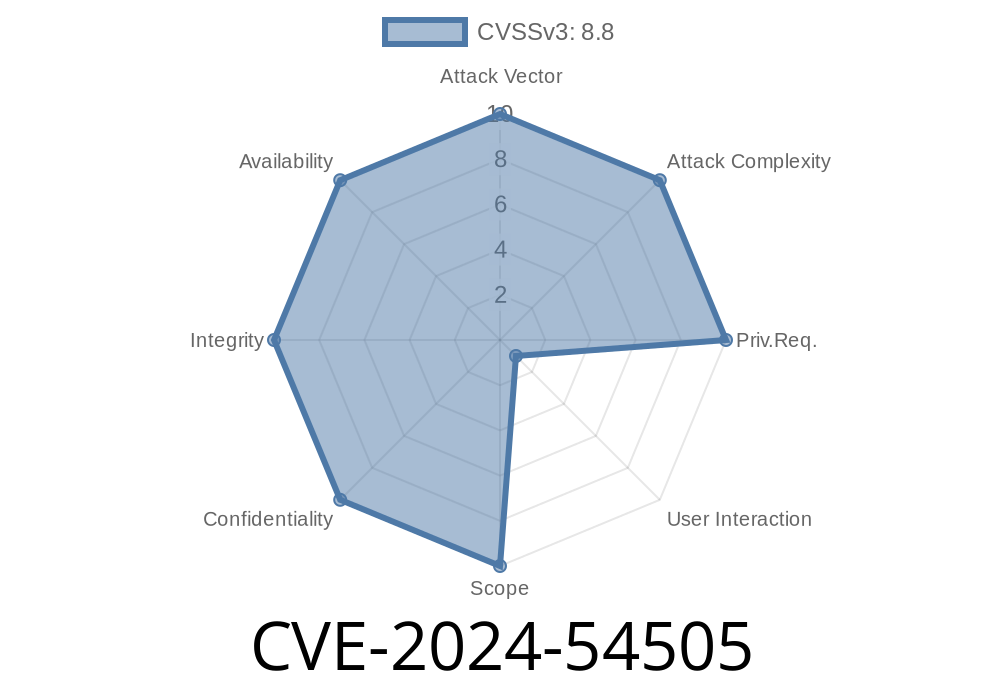
Apple devices recently patched a serious security issue with CVE-2024-54505, a type confusion vulnerability that could allow attackers to corrupt memory by processing specially crafted web content. In this article, we’ll break down what happened, look at sample code, and see how Apple fixed this bug.
What Is CVE-2024-54505?
CVE-2024-54505 is a vulnerability that affects various Apple products, including iOS, iPadOS, watchOS, macOS, visionOS, tvOS, and Safari. The flaw involves “type confusion”—a class of bugs where a program accesses memory as though it’s one data type, while it actually contains another. Attackers can abuse this confusion to corrupt memory and potentially run harmful code on your device.
Safari 18.2
Apple’s advisory:
Apple Security Updates - CVE-2024-54505
NIST CVE detail page
How Does Type Confusion Work?
Imagine a scenario in JavaScript engine code where the software expects to handle an integer, but due to poor checks, it handles a floating-point number instead. This mismatch can cause crashes or let attackers change how the program behaves in memory.
Simple Example (Not the Real Exploit)
// Pseudo-code example of type confusion:
function triggerTypeConfusion(array) {
// Suppose array is sometimes made of ints, sometimes of floats
return array[] + 2;
}
If the underlying engine trusts that array[] is an integer, but it’s a float (possibly attacker-controlled), the result is unpredictable. In real attacks, this is much more complex and can be used to read or write unauthorized memory areas.
What could an attacker do?
By luring a user to a malicious website, the attacker sends specifically crafted code to exploit the type confusion bug inside the WebKit browser engine. This could allow them to:
Security researchers often craft JavaScript like this
// Example pseudo exploit code
let array = [1.1, 2.2, 3.3];
let obj = {};
array.__proto__ = obj; // force array to behave differently
// Then interact with 'array' in a way that causes type confusion inside WebKit.
// In real attacks, the details depend highly on browser internals.
Note: The actual exploit for CVE-2024-54505 will be much more complex and will not be publicly released right away to protect users.
How Did Apple Fix The Bug?
In official statements, Apple said they improved “memory handling.” That usually means they added stricter checks that make sure data types are what they’re supposed to be before acting on them.
In code, it might look like this
// Older unsafe code:
if (somePointer) {
ProcessAsTypeA(somePointer);
}
// Improved safe code:
if (somePointer && somePointer->isTypeA()) {
ProcessAsTypeA(somePointer);
}
// Otherwise, decline to process or safely handle error
While we don’t have Apple’s exact code changes, these improvements remove opportunities for attackers to trick the browser into mixing up data types.
Install the latest security patch.
This goes for your iPhone, iPad, Mac, Apple Watch, and across all browsers if you use Safari.
More Reading & Resources
- Apple CVE-2024-54505 Advisory
- NIST CVE-2024-54505 Page
- Wikipedia: Type Confusion
Conclusion
CVE-2024-54505 shows how sneaky bugs in browsers or system code can lead to serious security problems. Type confusion might seem technical, but the bottom line is: update your devices and stay safe from these kinds of attacks. Apple’s quick patching helps keep your devices protected, but only if you install their updates in time.
Timeline
Published on: 12/12/2024 02:15:31 UTC
Last modified on: 12/13/2024 18:43:13 UTC