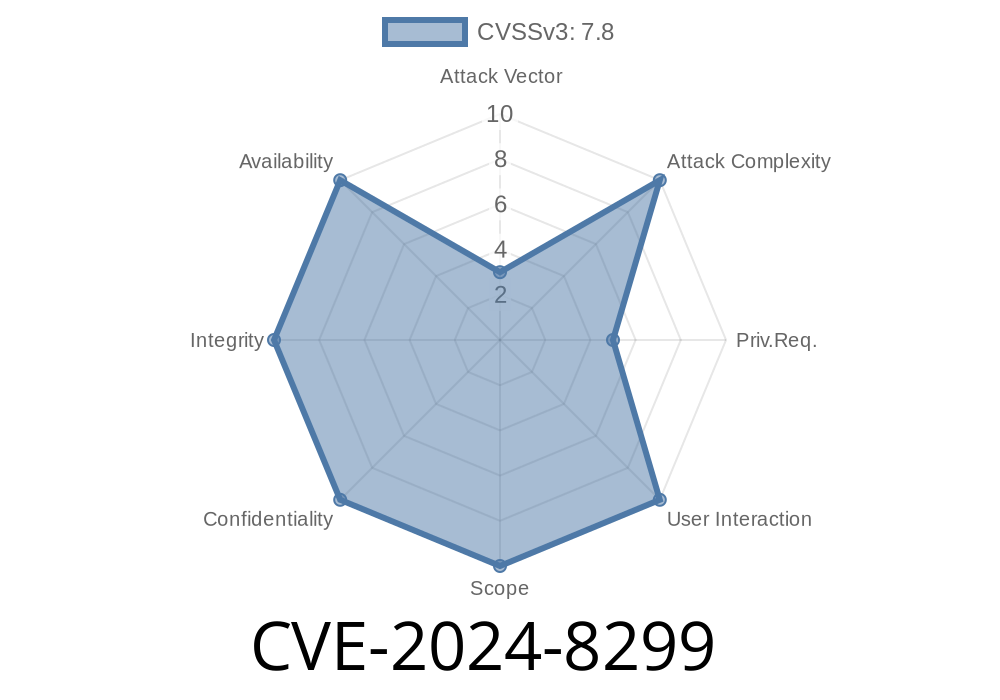
A new vulnerability tagged as CVE-2024-8299 has been recently uncovered, impacting the widely used ICONICS GENESIS64 suite and Mitsubishi Electric GENESIS64/MC Works64 industrial automation products. This flaw can let attackers load and execute malicious code on affected systems by exploiting how the software looks for required DLL files. Below, we'll break down what the risk is, how hackers can abuse it, and what steps you can take to stay protected.
What Is CVE-2024-8299?
CVE-2024-8299 is a classic “Uncontrolled Search Path Element” vulnerability. In simple terms, this means the software doesn’t properly check where it loads its DLL plugins from. If an attacker gets access, they can slip a hostile DLL file in a folder where the software is likely to look first. When the app launches, it loads the attacker’s code instead of the real deal.
Mitsubishi Electric MC Works64 (all versions)
All these are commonly used in industrial/OT (Operational Technology) environments, including energy, manufacturing, and building automation.
Who Is at Risk?
To pull off this attack, the bad guy needs some level of access: they must be locally authenticated. This means the attacker has a valid user account or has compromised one already (sometimes via phishing or stolen credentials).
How Does the Exploit Work?
At the heart of the bug is the insecure way GENESIS64 and MC Works64 load DLL files. When the app starts, it scans for DLLs following a “search order.” If an attacker can drop a malicious DLL *before* the legit one in this path, the app will load the attacker’s file.
Drop DLL in Target Folder:
Attacker copies the evil DLL into a directory GENESIS64 or MC Works64 checks *before* the regular system folder.
Trigger Application:
Starts or restarts the vulnerable application/service.
Example Code: Simple Malicious DLL Payload
Here’s a basic DLL (in C++) that opens Calculator as a proof of concept, representing attacker code:
// evilpayload.cpp
#include <windows.h>
BOOL APIENTRY DllMain(HMODULE hModule, DWORD reason, LPVOID lpReserved) {
if (reason == DLL_PROCESS_ATTACH) {
WinExec("calc.exe", SW_SHOW);
}
return TRUE;
}
Compile and name this DLL to match a missing or expected DLL GENESIS64/MC Works64 loads during startup, then drop it into the search path folder.
### Real-World Example Steps (Lab/Safe Use Only)
Identify a DLL Searched for by Process
Use ProcMon (from Sysinternals) to watch which DLLs GENESIS64 looks for during startup that are not found.
Place Evil DLL
Copy your compiled badguy.dll into the application’s working directory or another writable directory checked earlier.
Restart Service
Restart GENESIS64/MC Works64—your code runs with the program’s permissions.
How Can I Fix or Mitigate CVE-2024-8299?
- Install Official Fixes: ICONICS and Mitsubishi Electric are expected to release security updates — apply them ASAP.
Limit Write Permissions: Make sure untrusted users cannot write to application directories.
- Monitor for Unexpected DLLs: Use file monitoring tools to alert on new/unknown DLL files in GENESIS64/MC Works64 folders.
Follow Least Privilege: Keep user accounts with the minimum permissions necessary.
- Disable Unneeded Features: Turn off features/services you don't use in GENESIS64 or MC Works64.
References & Further Reading
- MITRE CVE page for CVE-2024-8299
- ICONICS Security Advisories *(Check for latest patches)*
- Mitsubishi Electric Security Advisory Portal *(Search for CVE-2024-8299)*
- Uncontrolled Search Path CWE-427
- DLL Hijacking Explanation — SANS
Final Words
Vulnerabilities like CVE-2024-8299 are serious in OT environments where uptime and process integrity are critical. Though an attacker needs to be on the inside, once there, exploiting this bug is relatively easy. Stay vigilant by patching, monitoring file changes, and restricting folder permissions. If you use ICONICS GENESIS64, Mitsubishi GENESIS64, or MC Works64, work with your vendors and IT teams to close this hole quickly.
*Keep your industrial controls locked down—don’t let a missing DLL be your weakest link!*
Timeline
Published on: 11/28/2024 23:15:03 UTC
Last modified on: 12/06/2024 06:15:22 UTC