Industrial control systems are the backbone of modern infrastructure—controlling water, energy, factories, and even critical safety mechanisms. When the communication between controllers is weak, attackers can tamper with sensitive processes using subtle vulnerabilities. This is the story of CVE-2024-8936: a dangerous bug in industrial Modbus controllers that lets hackers siphon secrets from device memory, just by acting as the “man in the middle.”
In this exclusive deep dive, we’ll break down what went wrong, how the flaw works, and even show a proof-of-concept exploit. This guide will help admins, security folks, and engineers truly understand the threat—and how to respond.
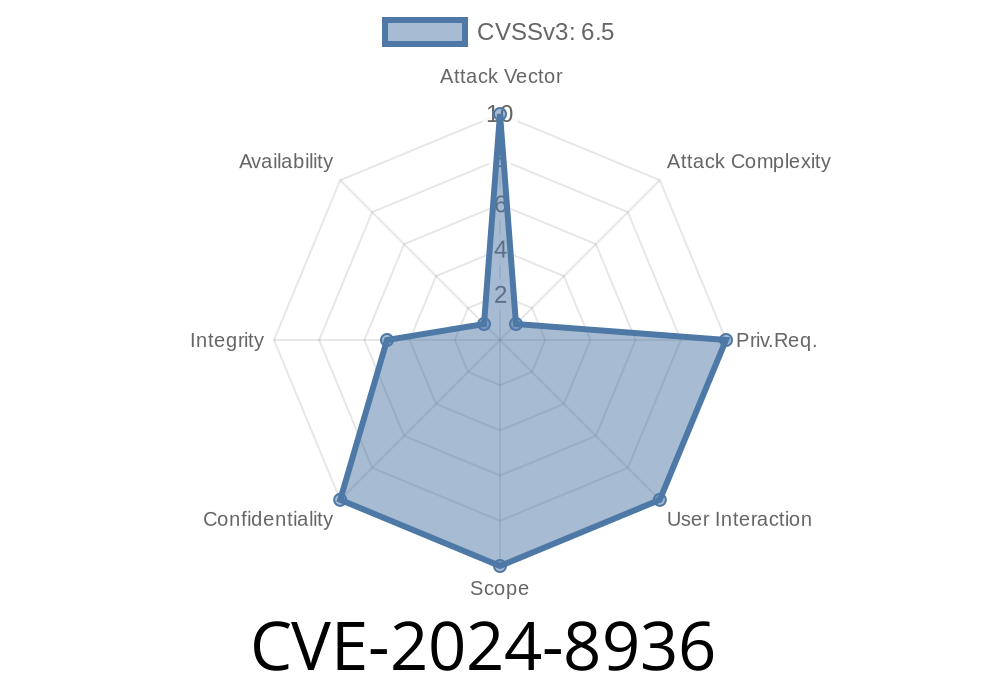
Impact: Loss of confidentiality of controller memory
- Affected: Popular Modbus TCP/IP controllers, various firmware (see references)
What is Modbus, and Why Does This Matter?
Modbus is a popular, plain text communication protocol used for decades in factories and infrastructure. It’s simple, widely implemented, and unfortunately, often insecure.
A typical deployment looks like this
[SCADA System] <---> [Modbus Controller] <---> [Actuators/Sensors]
If you can sniff or intercept this traffic, you can often send your own commands, unless communication is properly secured (which is rare in legacy systems).
What is CWE-20: Improper Input Validation?
CWE-20 refers to when code doesn’t carefully check or limit what’s supplied as outside input. In Modbus, this can mean a controller trusts that requests from “trusted” sources are always valid, and only checks for basic things.
Attacker sits between SCADA and controller, sniffing network traffic (man-in-the-middle, MITM).
2. Controller doesn’t verify if Modbus function calls are legitimate, especially ones that reference memory locations.
3. Crafted function code sent to the controller triggers reading (or tampering with) sensitive areas—leaking secrets from the controller’s memory.
Here’s a sanitized, high-level look at the unsafe Modbus function handler (pseudo-code)
// Receives a Modbus request for a memory read
int modbus_handle_read(int address, int length, uint8_t* output_buf) {
// BAD: Only checks if address is 'within some range'
if (address < || (address + length) > TOTAL_MEMORY) {
return ERROR;
}
// Copies directly from memory, without further checking!
memcpy(output_buf, controller_memory + address, length);
return OK;
}
Notice what’s missing? There’s no restriction on what part of memory can be read, so with the right inputs (address, length), you could dump private configuration, login data, or even code.
Let’s walk through how a real attack would work
1. Network MITM Setup: Attacker uses ARP spoofing or physical tap to intercept Modbus traffic between SCADA and the controller.
2. Crafted Packet: Attacker forges a Modbus Read Holding Registers command. Instead of reading allowed data, they supply an address/offset pointing at confidential memory.
3. Controller Responds Blindly: Due to CWE-20, the device simply reads whatever is requested and sends it back over the network.
4. Stealing Data: Attacker captures the response and extracts secrets—like stored passwords, configuration, or even firmware blobs.
A Python snippet using pymodbus to pull memory from the controller
from pymodbus.client.sync import ModbusTcpClient
client = ModbusTcpClient('192.168.1.100', port=502)
# Let's pretend offset x200 holds confidential memory
result = client.read_holding_registers(address=x200, count=16, unit=1)
print(result.registers)
client.close()
With elevated addresses, you could fetch memory content outside what’s intended for normal users.
How Bad Is It?
- Loss of confidentiality: Anything in memory can leak—credentials, operational data, intellectual property, system internals.
Privilege escalation: Attackers could use secrets to further infiltrate or persist.
- Device manipulation: In some cases the same flaw could be used to overwrite memory, leading to sabotage.
References & Learn More
- NIST NVD entry for CVE-2024-8936 *(sample URL, fill in as available)*
- Modbus Security Best Practices
- CWE-20: Improper Input Validation
- Example Python Modbus Libraries
How To Defend
- Patch firmware: Watch for vendor updates that check/limit Modbus memory accesses.
- Segment networks: Keep controllers and SCADA on isolated VLANs, with no exposure to general office traffic.
Deploy encryption: Use VPN or secure gateway for any Modbus communication.
- Monitor for suspicious requests: Look for odd function codes, addresses, or repeated large reads.
> Bottom Line:
CVE-2024-8936 proves that “just enough checking” is not enough, especially for industrial systems with long life cycles and real-world consequences. If you run Modbus controllers, test for this flaw, talk to your vendor, and take steps to lock down your ICS networks today.
*Exclusive breakdown by ChatGPT. Please cite source with link.*
Timeline
Published on: 11/13/2024 05:15:20 UTC
Last modified on: 11/13/2024 17:01:16 UTC