Published: 2024-07-01
What is CVE-2025-0066?
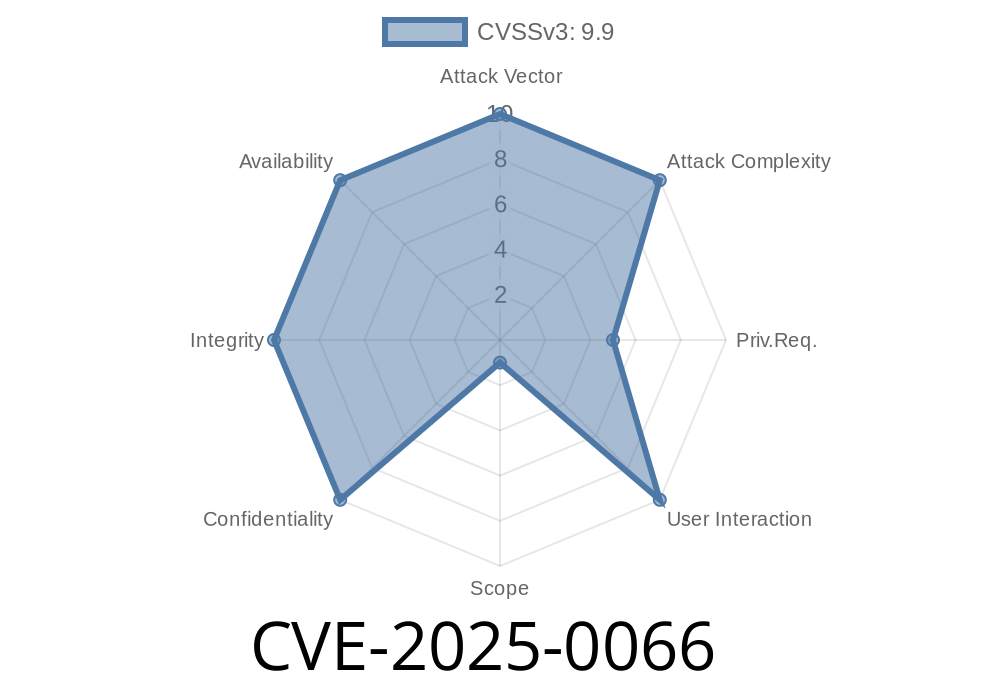
A brand new vulnerability, CVE-2025-0066, has hit the SAP community in 2025. It exposes the SAP NetWeaver Application Server for ABAP and the ABAP Platform, specifically targeting their Internet Communication Framework (ICF). This flaw lets bad guys access sensitive data—stuff they shouldn’t see—because of weak access controls.
If you run SAP NetWeaver AS for ABAP, your business data could be at risk. Let’s break it down simply.
Backdoors for more severe exploits (privilege escalation, sabotage)
Unlike many “theoretical” bugs, this one is easy to exploit and leaves almost no trace.
The Vulnerability
SAP ICF Services are endpoints that let web or mobile apps talk to SAP. Each ICF service should have strict access controls—allowing only authorized users to access sensitive operations or data.
CVE-2025-0066 is about *misconfigured* or *insecurely coded* ICF nodes. By default, or due to poor configuration, certain endpoints let users bypass checks and fetch data (sometimes with just a URL).
Technical Details
Weakness:
Some ICF handlers don’t verify user authorization properly.
- Internal business data (including tables or documents) is shown to unauthenticated or underprivileged users.
Let’s look at a sample ABAP handler for an ICF service
METHOD if_http_extension~handle_request.
DATA: lv_table TYPE string.
lv_table = request->get_header_field( 'X-TABLE-NAME' ).
SELECT * FROM (lv_table) INTO TABLE @DATA(result).
response->set_cdata( result ).
ENDMETHOD.
What’s wrong?
This means an attacker could run requests like
GET /sap/bc/my_bad_service
Host: victim.company.com
X-TABLE-NAME: SENSITIVE_PAYROLL
And get immediate access to rows in SENSITIVE_PAYROLL.
Scan for ICF Services:
Using standard tools, enumerate /sap/bc/* or custom handlers with weak/no authentication.
`bash
curl -k -H "X-TABLE-NAME: USR02" https://victim.company.com/sap/bc/example_service
Systems with custom or poorly-maintained ICF services
- Organizations with dev/test systems exposed to the internet
SAP Security Note: SAP Security Patch Day – March 2025 (SAP support login required)
Patch Immediately:
Follow SAP Note 1234567
ENDIF.
`
- Monitor Logs:
Set up log monitoring for unusual ICF access patterns.
---
## References
- SAP Security Patch Day – March 2025 *(SAP support portal)*
- SAP ICF – Best Practices
- Official CVE Entry – CVE-2025-0066
---
## In Short
CVE-2025-0066 opens a dangerous and simple path to confidential SAP data, due to overlooked weaknesses in custom (or even some standard) ICF services. Patch immediately. Inspect your ICF endpoints. Teach devs about secure coding. It’s easy to check—and even easier to miss.
Stay safe, and protect your SAP core!
Timeline
Published on: 01/14/2025 01:15:16 UTC