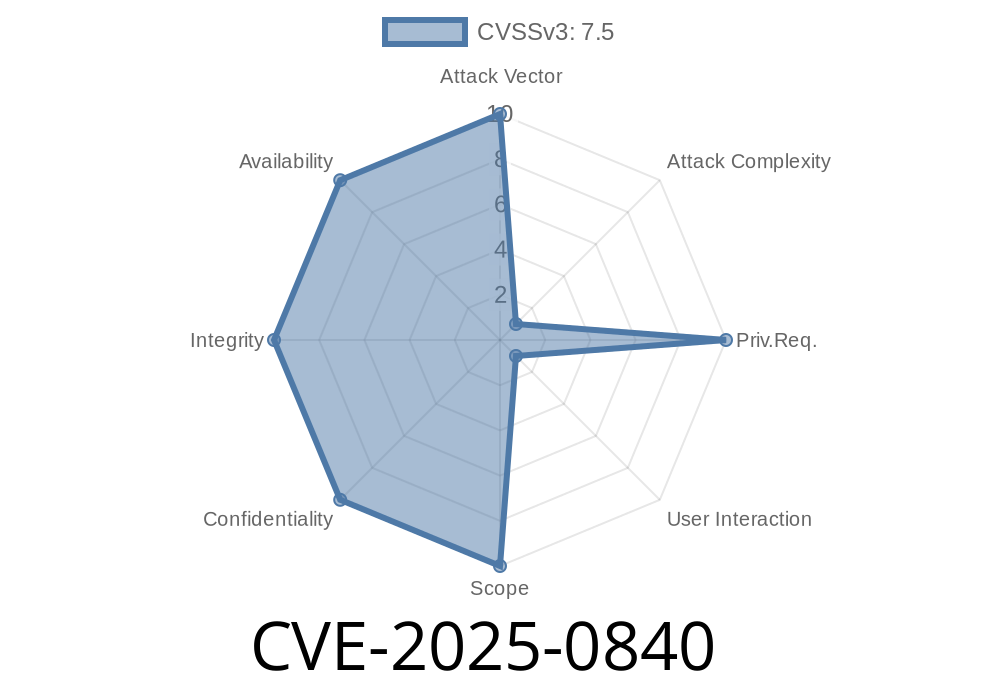
A highly problematic vulnerability, classified as stack-based buffer overflow, has been identified in GNU Binutils versions up to 2.43. The vulnerable function disassemble_bytes within the binutils/objdump.c file is affected by this security issue, allowing potential attackers to manipulate the buf argument. Although this attack can be initiated remotely, it has a high complexity, and the exploitability is considered difficult. To mitigate this vulnerability, users are strongly advised to upgrade to GNU Binutils version 2.44. The patch identifier for this fix is baac6c221e9d69335bf41366a1c7d87d8ab2f893.
Code Snippet
The vulnerability exists in the disassemble_bytes function in binutils/objdump.c file. Here is a code snippet demonstrating the problem:
static void
disassemble_bytes (struct disassemble_info *info, fprintf_ftype fprintf_func,
void *stream, bfd_byte *buf, FILE *fp)
{
// ...
while (length > )
{
int status, i;
bfd_vma insn_start = pc;
/* snprintf might fail, so pass the snprintf result to fprintf */
status = snprintf (&buf1[], bufsize, VMA_FMT_WIDTH_PREFIX,
(bfd_vma) pc);
if (status < || status >= (ssize_t) bufsize)
// ...
}
}
This code attempts to move values placed in buf1 inside the buf argument. However, a potential attacker can manipulate the buf argument, causing unexpected data growth that might lead to stack-based buffer overflow.
Exploit Details
The operation of the attack is complex, and exploitability is challenging, yet it can still be executed remotely. The potential attacker can manipulate the buf argument, which is then passed to the vulnerable function disassemble_bytes. If successful, the attacker might cause a stack-based buffer overflow, ultimately compromising the system.
Original References
The exploit is publicly disclosed and may be used by malicious actors. Please refer to the following references for more information:
- Public disclosure of CVE-2025-0840
- GNU Binutils Project Homepage
- Vulnerability Patch baac6c221e9d69335bf41366a1c7d87d8ab2f893
Recommended Action
As mentioned earlier, upgrading to GNU Binutils version 2.44 or later will address the vulnerability, as the fixed version includes the patch baac6c221e9d69335bf41366a1c7d87d8ab2f893. It is highly recommended that users upgrade the affected component to avoid potential exploitation and compromise.
In summary, CVE-2025-0840 is a critical vulnerability that affects GNU Binutils up to 2.43. Although the exploit is complex and difficult to execute, the potential consequences can be severe if successfully employed. Therefore, users should immediately upgrade to GNU Binutils 2.44 to ensure that their systems remain secure.
Timeline
Published on: 01/29/2025 20:15:35 UTC
Last modified on: 03/04/2025 15:08:47 UTC