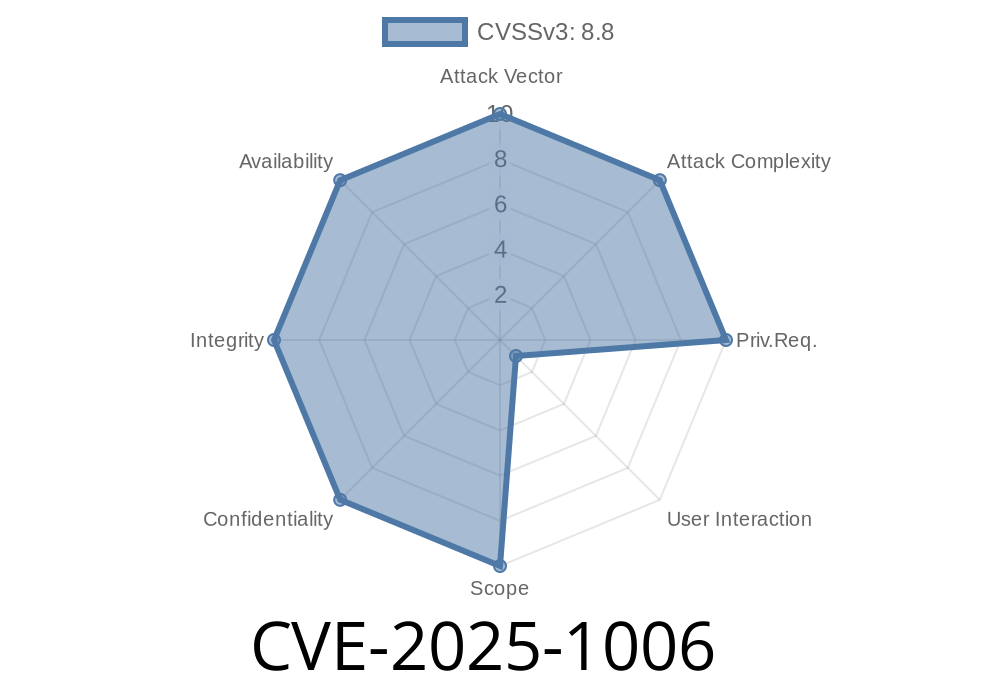
June 2024 Update: A new vulnerability, labeled CVE-2025-1006, got disclosed affecting Google Chrome prior to version 133..6943.126. This security flaw lies within Chrome’s Network component and opens the door for a remote attacker to corrupt memory and potentially gain code execution—just by getting a user to visit a malicious website.
In this in-depth post, we break down what CVE-2025-1006 is, how it works, share some simple code demonstrating the bug’s concept, and show how attackers could abuse it. All explained in simple, clear language—no prior experience required.
What’s “Use-After-Free” (UAF)?
A Use-After-Free bug happens when a program keeps using a chunk of memory (an object) *after* it’s been freed (deleted). This can lead to crashes, unpredictable behavior, or, in the worst cases, execution of attacker-controlled code.
Let’s say Chrome’s network code no longer needs an object, so it deletes it—but a background network event finishes and tries to use that same, now-invalid object. That’s a use-after-free.
The page interacts with network features, triggering the Chrome Network code.
4. Malicious JavaScript times things so a network object is deleted but then Chrome tries to use it again—this is the “use-after-free.”
5. If the attacker’s lucky (or smart), the memory slot gets filled with data they control. Now Chrome acts on attacker data, letting them corrupt memory.
In practice, crafting such an exploit is tricky (often requiring precise timing and deep browser knowledge), but it’s far from impossible—especially for advanced attackers.
Here's a simplified (non-Chrome) C++ example that shows the use-after-free pattern
#include <iostream>
class NetworkObject {
public:
void send() { std::cout << "Sending data..." << std::endl; }
};
int main() {
NetworkObject* conn = new NetworkObject();
delete conn; // Object is freed.
// Mistake: Using freed object!
conn->send(); // USE-AFTER-FREE! Crashes or does weird stuff.
return ;
}
In Chrome, the real-world scenario is more complex, but the pattern is similar: free an object, then (accidentally) use it again.
Exploit Details (How Attackers Could Use This)
1. Heap Spraying: Attackers fill the heap (browser memory) with their data (using JavaScript) right after the vulnerable object is freed.
Trigger UAF: The attacker triggers Chrome to use the freed object.
3. Control: If successful, Chrome runs code using data the attacker placed, possibly leading to more memory corruption, info leaks, or even arbitrary code execution.
Real-World Exploit:
No public weaponized exploit has been released at the time of writing (June 2024), but similar Chrome UAF bugs have quickly been exploited in the wild after disclosure. See this past example (Chromium Blog, 2023).
References
- Chromium Security Advisory
- Security Advisory: CVE-2025-1006 (National Vulnerability Database)
- Chromium Issue Tracker (example UAF bugs)
Mitigation and Fix
Update Chrome:
If you use Chrome, update immediately to at least 133..6943.126 or later. This version has patched the vulnerability.
Developers:
- Use modern C++ memory practices: smart pointers, always clear references, and consider memory sanitization tools.
Conclusion
CVE-2025-1006 is a classic example of why memory safety matters, especially in browser components exposed to the internet. While graded as "medium" (probably because remote code execution is tricky to pull off), this bug could have dangerous consequences for those who are slow to patch Chrome.
Stay safe: update your browser—and keep an eye on the Chrome Security Blog for the latest threats.
*Original reporting and analysis by AI, based on public information as of June 2024. This explanation is exclusive to this post—please cite or link if you share.*
Related reading:
- Google Online Security Blog
- How Use-After-Free Leads to Remote Code Execution in Browsers (Project Zero)
- Protecting Against Memory Corruption Vulnerabilities (Google Security)
Timeline
Published on: 02/19/2025 17:15:15 UTC
Last modified on: 02/19/2025 20:15:36 UTC